Cybersecurity Threats to Watch in 2024 As the new year unfolds, the Korea Ministry of Science and ICT, in collaboration with the Korea Internet & Security Agency (KISA), has revealed insights into cybersecurity threats demanding vigilance in 2024. Let's delve into key security issues emphasized by experts. 1. Increased Supply Chain Attacks The escalation of ...
[Weekly Security News] Cyber Threat right under your nose
Cyber Threat right under your nose 1. Chinese hackers hid in US infrastructure network for 5 years Chinese hackers have at times secretly hidden in U.S. infrastructure for up to five years, ready to conduct a potentially destructive cyberattack if the two countries were to go to war, federal agencies said Wednesday.Over the past year, U.S. officials have repeatedly issued warnings t ...
[Weekly Security News] Russian ransomware gang claims it stole ‘classified and top secret documents’ from US intelligence
Data breaches which are happening even now 1. Russian ransomware gang claims it stole ‘classified and top secret documents’ from US intelligence A Russian hacking group has claimed it infiltrated a tech company, Technica, responsible for handling “classified and top secret” documents for US intelligence agencies. A Department of Defense spokesman, meanwhile, said the agency “is awar ...
Emerging Cybersecurity Risks: The Exploitation of Generative Artificial Intelligence (Generative AI)
Emerging Cybersecurity Risks: The Exploitation of Generative Artificial Intelligence (Generative AI) Security experts have identified the misuse of Generative AI in cybercrime as a significant and growing threat in the security industry. The rapid advancement of Generative AI technology has empowered individuals without specific security expertise to engage in malicious activities, ...
[Weekly Security News] Data breaches which are happening even now
Data breaches which are happening even now 1. Authorities investigating massive security breach at Global Affairs Canada Canadian authorities are investigating a prolonged data security breach following the "detection of malicious cyber activity" affecting the internal network used by Global Affairs Canada staff. The breach affected at least two internal drives, as well as emails, c ...
[Weekly Security News] Reckless cyberattacks and related report
Reckless cyberattacks and related report 1. Web Application Firewall Software Market Data and In-depth Analysis to 2030 |Amazon Web Services, Cloudbric, Cloudflare, Akamai, Trustwave Holdings Stats N Data published a comprehensive market analysis report on Web Application Firewall Software Market. The report deals with essential questions that industry players and investors want to add ...
[Weekly Security News] Cyberattacks against unexpected target
Cyberattacks against unexpected target 1. Toronto Zoo hit by ransomware attack LoanDepot,a third-largest mortgage lender in the U.S., has been hit by cyberattack and it affected internal systems and caused disruption for customers. The company detected unauthorized activity and promptly took steps to contain and respond to the incident. If data has been stolen, it will be a potentia ...
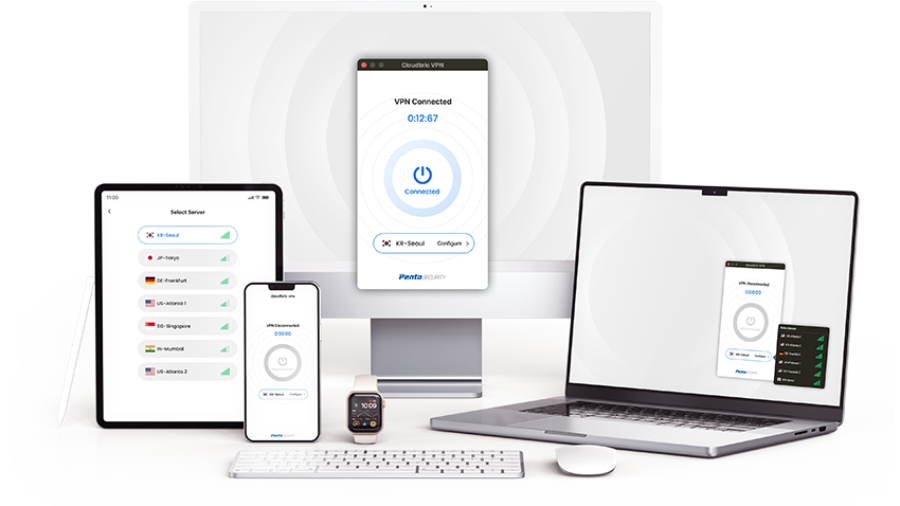
Cloudbric VPN Update: Enhanced visibility with service stability
Cloudbric VPN Update: Enhanced visibility with service stability Cloudbric VPN, developed by encryption experts Penta Security, has recently undergone a significant update to improve user experience, service stability, and adding servers overseas. Let's take a closer look at the recent updates and explore the key features of the Cloudbric VPN. 💡 Cloudbric VPN Service ...
[Weekly Security News] Predicted hacking trend in 2024 and the latest security issue relate to daily lives
Predicted hacking trend in 2024 and the latest security issue relate to daily lives 1. 2024 Cybersecurity Trends: Insights from Experts The cybersecurity experts predicted a rise in the exploitation of zero-day vulnerabilities, ransomware, state-sponsored attacks, lack of trained cybersecurity resources, mobile cybercrime, and AI-Powered Frauds. Source : The CYBER EXpress &nb ...
[Weekly Security News] Data breach at the end of the year
Data breach at the end of the year 1. Hackers steal customer data from Europe’s largest parking app operator The largest parking app operator has reported itself to information regulators in the EU and UK after hackers stole customer names, phone numbers, addresses, email addresses and parts of credit card numbers. This hack highlights the increasing centralization of parking servic ...