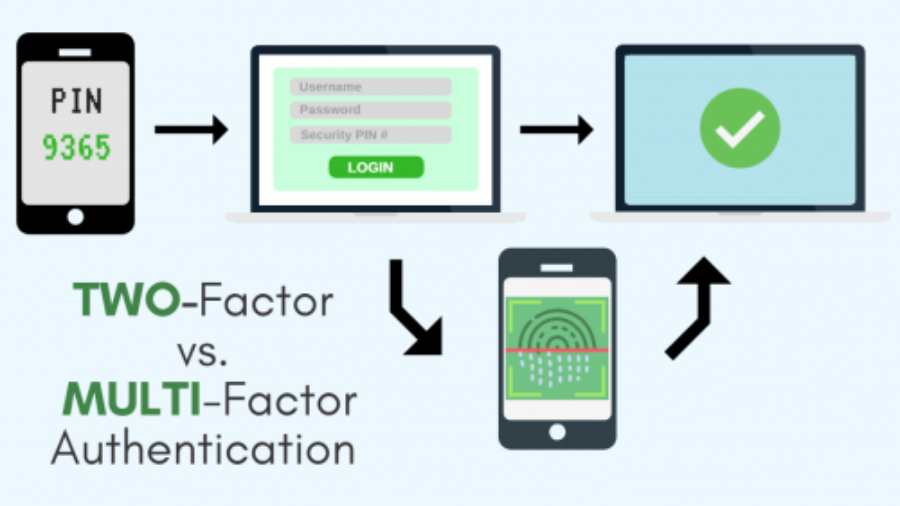
When the best online security practices are being discussed, there’s always someone that brings up either two-factor authentication (2FA) and multi-factor authentication (MFA). This is because more and more online services are recognizing the need to ensure a higher level of security for online accounts. Two-factor authentication and multi-factor authentication add additiona ...
The Anatomy of a Blended Attack
What is a blended attack?Depending on the context, a blended attack can refer to two different things. Generally speaking, a blended attack refers to the idea of using mixed techniques to invade one computer system to the next. Blended attacks, then, can include computer viruses, worms, and Trojan horses. They typically exploit an initial security flaw and move on to perform additional n ...
DDoS Protected Web Hosting
DDoS attacks can be frustrating for many website owners as hackers may aim to overwhelm a website and its server resources until it goes offline. For larger organizations, a successful DDoS attack can mean loss of hundreds or even tens of thousands of dollars for every hour the site is down. And although less quantifiable, the loss of customer loyalty resulting from a DDoS attack can ...
Website Optimization Walkthrough: Getting Speed and Security Right From The Start
No need to compromise between speed and security The idea of building a website for the first time can be daunting. Luckily there are various CMS out there that make it easy to get started. While having a responsive design is often necessary to attract potential visitors, because page load time is also now part of Google’s algorithm it’s important to make sure speed and s ...
Partner Success Story: Jensen Computer Technologies
It goes without say that customers are everything. They are the backbone to any successful business. Because Cloudbric values the opinions of our customers, we occasionally ask users to provide feedback via online surveys as part of our continual efforts to improve our services. The Cloudbric team first came in contact with Ryan Jensen of Jensen Computer Technologies after he ...
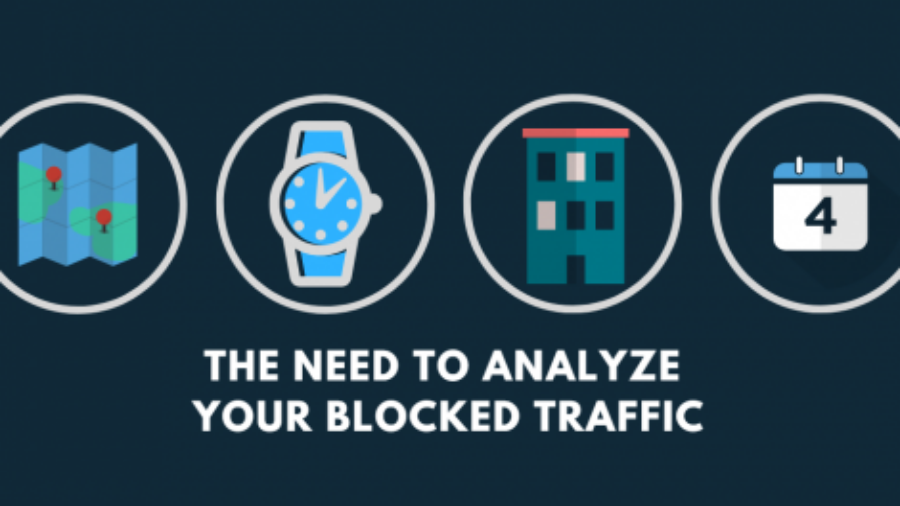
The Need to Analyze Your Blocked Traffic
We’ve all heard the statistics of the growing numbers of web threats and hacking attempts on the web. Whether it’s from the recent onslaught of ransomware attacks, or the growing Dark Web, there’s no day that passes by that we don’t hear about the dangers that the cyber realm faces. However, it’s a great day and age where more and more services are becom ...
What You Should Wanna Do About WannaCry
Is Wannacry making you want to cry? This past weekend hit the world like a pile of bricks as nearly 100 countries were hit with the ransomware, WanaCry (or WannaCry, as many are prone to calling it). This malicious ransomware, like a worm, spreads on its own. Targets are met with a ransom screen that demands $300 in bitcoin as a ransom within the first three days, lest the ransom be ...
Three Security Services That All Small Businesses Need
Small businesses are the backbone of America and account for 99.7% of all businesses. In the US, small businesses are defined as businesses with fewer than 500 employees. Because of their size, small businesses often fall into a dangerous mentality of believing they are too small to be the target of cyber attacks and assume they do not need a cyber security plan since hackers appear ...
Easter Eggs in WordPress?
Easter Eggs Background Easter eggs are nothing new in technology, especially in software. They started out in entertainment in the 1970s and have remained part of pop culture today. Easter eggs in the digital sense, particularly those found in software and applications, aren’t as popular as they once were, but developers are still in the habit of looking for ways to spice up their ...
Taking SSL One Step Further with Redirection Mode
In recent years, Secure Sockets Layer (SSL) has become a standard in the industry. Already used by millions of websites to protect their information, SSL is a necessary and relatively accessible security feature to apply onto your site. We’ve talked a lot about what SSL is, and how reliable free SSL can be - and to take it further today, we’ll talk about redirecting your ...