2017 was the year in which ransomware grabbed the attention of many. Petya, NotPetya, and WannaCry, in particular, are still fresh on our minds. But with eyes on the major headlines of the past year — from the massive Equifax data breach to Uber’s embarrassing data leakage cover up — you might have missed out on another trend: the slow but steady re-emergence of ban ...
2017’s Cybersecurity Naughty or Nice List
The word “hacker” often has a negative connotation. Most of the time, the hackers we refer to or hear about are of the villainous variety, known as “blackhat” hackers. However, these malicious hackers aren’t the only “type” of hackers you will come across online. There are also “whitehat” hackers, for example, who use th ...
Top 10 Cybersecurity Headlines of 2017
Cyber incidents like the powerful Mirai botnet and the attack on DNS provider Dyn defined some of the biggest (cyber) moments back in 2016. The Dyn attack, for instance, disrupted internet services all over the world and is now considered the largest attack of its kind in history. But 2017 also set some new precedents when it came to cyber breaches and the magnitudes of damage. Here ...
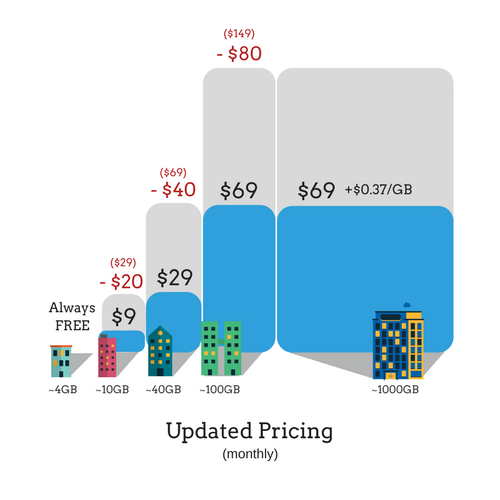
Cloudbric Updates Service Pricing
As Cloudbric continues to expand, we’re always finding ways to give our customers the best security at affordable prices. That’s why we’re pleased to announce that we’re offering reduced costs for our paid plans – no strings attached, no catch. How much you’re saving Let’s look at the comparison between the old and new pricing models. You&rsquo ...
Benefits of IP Reputation Services
Although users of the Web are becoming increasingly aware of the dangers lurking in cyberspace, many aren’t familiar with the technicalities behind certain cyber hygiene practices. Most are, however, acquainted with the basic signs of a non-secure website. One tell-tale sign is the presence of a green security lock beside a website’s URL, which indicates that the site use ...
Hacking via Remote Access Software?
Hackers typically sneak remotely into the networks of their victims by setting up phishing scams and duping users into downloading malware-ridden files, which are then executed to commence a cyberattack like ransomware. They may also look for vulnerabilities in computer systems to attempt to get into a network. Both the WannaCry and NotPetya attacks, for example, were successful beca ...
The Different Types of Cybercrimes This Holiday Season
It’s that time of year again. With October wrapped up and November in full swing, we are entering into the holiday season where cybercrimes are at an all-time peak. And even if you aren’t purchasing goods and services on the Internet, anyone can still fall victim to cybercrime. Sometimes, however, Internet users may not be aware of the different types of cybercrimes t ...
The Downsides to Bug Bounty Programs
Many people are familiar with bug bounty programs. They are designed to test the security of a company’s computer systems by crowdsourcing talent from all around the world to report bugs, especially those with critical vulnerabilities. In a way, bug bounty programs make the services and software we use much safer, but that’s just on the surface. While the rewards ...
Top 5 PCI Compliance FAQs
PCI (payment card industry) compliance may not be an expression you hear often as a business owner. However, non-compliance has noteworthy impact to the level of risk your business assumes in payment processing if you accept credit and debit cards from customers as a form of payment. Despite the media headlines that tend to focus on significant data breaches that impact major ret ...
5 Common WordPress Security Threats & Solutions You Need To Know About
WordPress is easily one of the most popular web-based platforms on the internet. In fact, over 28% of the viewable internet uses WordPress to host their websites. However, being an open-source platform where anybody can edit anything using CSS code and plugins means there are security risks. At its core, WordPress is the same for every website, meaning that hackers or users with ...