2022 Cyber Attack Status and 2023 Cybersecurity Outlook And How To Respond
 In March 2023, Lockbit, a global hacking organization, caused great concern when it announced the release of data from the National Tax Service. While the National Tax Service had been operating an emergency monitoring system and the announcement turned out to be an April Fool’s Day prank, it was revealed that nearly 20,000 hacking attempts had been made against the service over the past five years. Fortunately, no actual cases of tax information leakage were reported. However, news of cyberattacks by global hacking organizations like Lockbit is becoming increasingly common.Earlier this year, the Chinese hacking group “Xiaoqiying” hacked into the websites of 12 academic institutions, including the Korean Language Society, and distributed the personal information of Korean citizens on Github. LG U+, one of Korea’s mobile carriers, also experienced a data breach due to a DDoS attack, resulting in the leakage of subscriber personal information and access failures. These incidents highlight the growing threat of cyberattacks and the need for stronger cybersecurity measures.👉 Cyber Attack of the Chinese hacking group “Xiaoqiying”
In March 2023, Lockbit, a global hacking organization, caused great concern when it announced the release of data from the National Tax Service. While the National Tax Service had been operating an emergency monitoring system and the announcement turned out to be an April Fool’s Day prank, it was revealed that nearly 20,000 hacking attempts had been made against the service over the past five years. Fortunately, no actual cases of tax information leakage were reported. However, news of cyberattacks by global hacking organizations like Lockbit is becoming increasingly common.Earlier this year, the Chinese hacking group “Xiaoqiying” hacked into the websites of 12 academic institutions, including the Korean Language Society, and distributed the personal information of Korean citizens on Github. LG U+, one of Korea’s mobile carriers, also experienced a data breach due to a DDoS attack, resulting in the leakage of subscriber personal information and access failures. These incidents highlight the growing threat of cyberattacks and the need for stronger cybersecurity measures.👉 Cyber Attack of the Chinese hacking group “Xiaoqiying”
2022 Cyber Attack Status
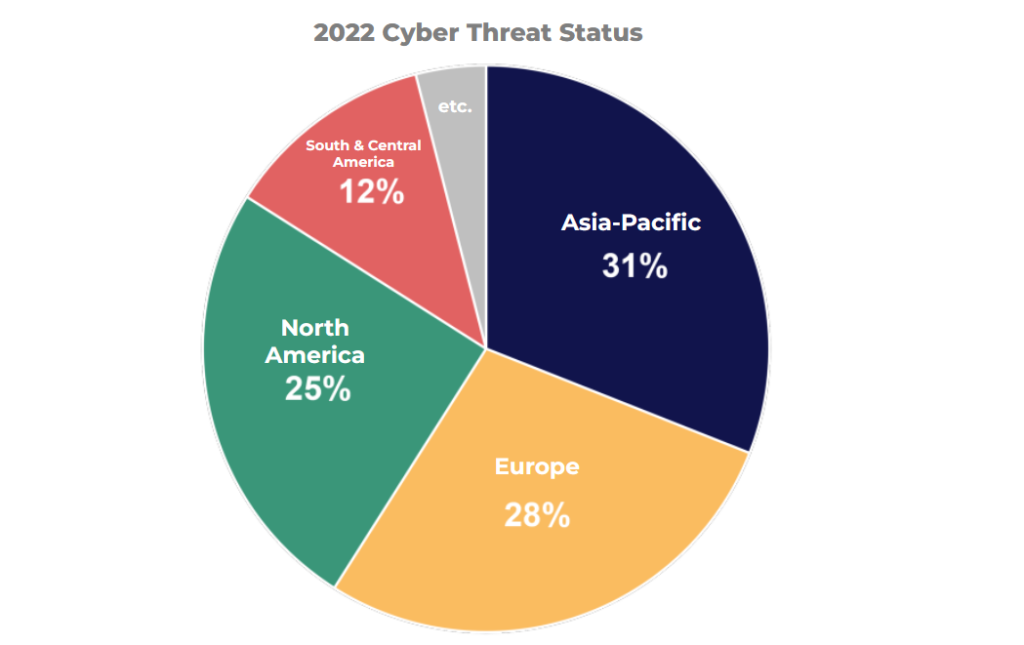 The Asia-Pacific region accounted for 31% of all cyberattacks last year, making it the region with the highest number of cyberattacks for the second consecutive year, followed by Europe, North America, and Latin America. The reason behind this trend could be attributed to the rapid growth of the economy and technological advancements in the region, which has attracted more companies, businesses, and investment opportunities, making it an appealing target for cybercriminals. As a result, the region has become more vulnerable to cyber threats, which has led to an increase in cyberattacks.
The Asia-Pacific region accounted for 31% of all cyberattacks last year, making it the region with the highest number of cyberattacks for the second consecutive year, followed by Europe, North America, and Latin America. The reason behind this trend could be attributed to the rapid growth of the economy and technological advancements in the region, which has attracted more companies, businesses, and investment opportunities, making it an appealing target for cybercriminals. As a result, the region has become more vulnerable to cyber threats, which has led to an increase in cyberattacks. The manufacturing industry has been particularly hard-hit. Attacks targeting this industry accounted for nearly half (48%) of all cyberattacks. The financial and insurance industries were also frequent targets, with attacks against these sectors making up 18% of all attacks.The reason why the manufacturing industry is particularly vulnerable to cyberattacks is the significant damage and ripple effects they can cause. A brief outage in the production system could significantly reduce the value of an enterprise, which would not only affect the company itself but also consumers who depend on its products.Given the growing prevalence of cyberattacks in today’s digital environment, it is critical to respond to security threats thoroughly and quickly to mitigate the impact on both businesses and consumers.
The manufacturing industry has been particularly hard-hit. Attacks targeting this industry accounted for nearly half (48%) of all cyberattacks. The financial and insurance industries were also frequent targets, with attacks against these sectors making up 18% of all attacks.The reason why the manufacturing industry is particularly vulnerable to cyberattacks is the significant damage and ripple effects they can cause. A brief outage in the production system could significantly reduce the value of an enterprise, which would not only affect the company itself but also consumers who depend on its products.Given the growing prevalence of cyberattacks in today’s digital environment, it is critical to respond to security threats thoroughly and quickly to mitigate the impact on both businesses and consumers.
2023 Cybersecurity Outlook
The Ministry of Science and ICT (MSICT) and the Korea Internet & Security Agency (KISA) have released their “2023 Cyber Security Threat Outlook,” which predicts,① Increased attacks by global hacking organizations that threaten national and industrial security It is expected that international hacking organizations will continue to target major infrastructure and international companies on a large scale. Attackers are likely to choose targets based on size, external reliability, potential damage, and sensitivity of data in order to maximize profits. Furthermore, there is expected to be a rise in attacks on cryptocurrency exchanges and digital wallets, which provide a direct source of profit.👉 Korea Joongang Daily – 18 billion won of crypto hacked from Korea’s GDAC exchange
②Continuation of cyber attacks by exploiting sensitive social issues such as disasters and disabilities
These attacks may include electronic financial fraud, text payment fraud, and hacking mail distribution that exploits social issues. The use of high-tech technology to spread fake news is also expected to undermine national credibility and affect society as a whole. In addition, malware is likely to continue to spread, and it is important to be vigilant not only for text and email attacks but also for those using personal social media channels.
👉 Examples and precautions of rapidly Increasing Smishing Incidents
③ The evolution of ransomware armed with Advanced persistent threats and multi-threats
Ransomware is evolving into an Advanced persistent threat that exploits various vulnerabilities, including hacking mail, web server vulnerability, authentication management server, and remote access. Attackers not only recover encrypted files, disclose leaked data, and launch DDoS attacks, but also demand money by threatening the brand image of a company as a hostage.
Many companies are vulnerable to such attacks because they fear the damage to their brand image that could result from public disclosure of the attack. Attackers are expected to continue to disclose sensitive information extorted from corporate systems as a means of maximizing profits.
④ Increasing Threats from the Digital Age Cloud Transition
As companies transition to cloud-based infrastructure, security threats will increase due to inadequate security strategies that reveal new security vulnerabilities.
In particular, insufficient account management and excessive privileges can lead to increased security threats and data leakage.
Therefore, it is necessary to establish access control and access procedures through certification, taking into account the unique characteristics of the enterprise.
⑤Increasing complexity of enterprise SW supply chains and increasing threats
The corporate supply chain is composed of various software products, developers, and consumers, and its complex relationships with information technology assets, development environments, manpower, and contract management make it difficult to detect and take action quickly, despite its significant impact.
There is an expected increase in attacks that insert malware or steal source code, targeting software developers who use a lot of source code development and sharing sites like GitHub.
Furthermore, various attempts to attack the supply chain are expected to occur, including spreading malware through server modulation, adding malicious functions to the source code, and distributing forged and signed malware after stealing a company’s certificate.
How to respond to Cyber threats?
 With the proliferation of digital technology, cyberattacks are becoming more sophisticated and the risks of new security threats are on the rise. In order to protect their assets, businesses need to develop a response system that can not only prevent incidents, but also minimize and recover from damage.The first step in responding to cyberattacks is to enhance the security systems in place. According to the ‘Global Perspectives on Threat Intelligence Report’ from Mandiant, identifying the source of the attack is crucial for corporate security officials when dealing with a cyberattack. In addition, detailed threat intelligence plays an important role in configuring cybersecurity strategies that can respond quickly to the latest threats.However, as the amount of data being collected continues to grow, it is becoming increasingly difficult for businesses to leverage and effectively use the threat intelligence they collect. Processing and analyzing the vast amounts of data requires significant time and resources, often placing an increased burden on already stretched security staff.
With the proliferation of digital technology, cyberattacks are becoming more sophisticated and the risks of new security threats are on the rise. In order to protect their assets, businesses need to develop a response system that can not only prevent incidents, but also minimize and recover from damage.The first step in responding to cyberattacks is to enhance the security systems in place. According to the ‘Global Perspectives on Threat Intelligence Report’ from Mandiant, identifying the source of the attack is crucial for corporate security officials when dealing with a cyberattack. In addition, detailed threat intelligence plays an important role in configuring cybersecurity strategies that can respond quickly to the latest threats.However, as the amount of data being collected continues to grow, it is becoming increasingly difficult for businesses to leverage and effectively use the threat intelligence they collect. Processing and analyzing the vast amounts of data requires significant time and resources, often placing an increased burden on already stretched security staff.
The Importance of Adopting a Managed Web Security Platform for Effective Cybersecurity
Since websites are connected to the internet, they are vulnerable to cyber threats regardless of their size. Therefore, strengthening web security is an essential task for any website owner.However, with many enterprises struggling to organize their security professionals, protecting their websites can be a challenge. Even companies with dedicated security teams find it difficult to manage and analyze large amounts of data required for threat intelligence. Introducing a managed web security platform can be an ideal solution to overcome these challenges and ensure comprehensive website protection.
Cloudbric’s Cloudbric WAF+ is the first SaaS(Software as a Service) type cloud security platform launched in Korea in 2015.
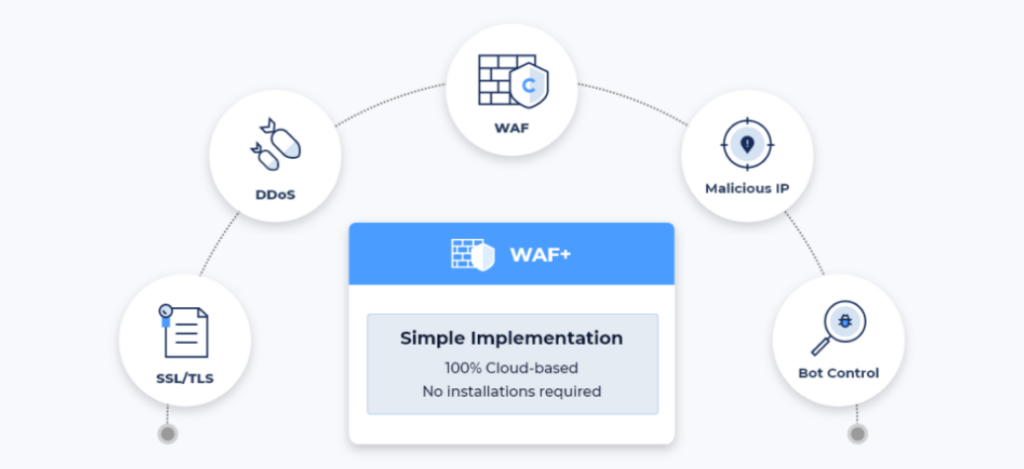
📌 Cloudbric WAF+ Features
✅ Fully managed WAF (Web Application Firewall)✅ DDoS(Distributed Denial of Service) attack protection ✅ SSL/TLS certificate✅ Block Malicious IP ✅ Bot(Spyware, Adware, Spam bot, Malicious web crawler) control
Cloudbric WAF+ is a fully managed security service provided by security experts. It offers overall cloud security services such as technical support and monitoring, proposes security operations policies optimized for each customer environment, and offers global market-proven security intelligence with a logic-based detection engine and patented deep learning engine.
Protect your website from advanced cyberattacks using Cloudbric WAF+, a fully managed Web Application and API Protection (WAAP) service that uses a powerful Logic-based detection engine and deep learning engine to offer comprehensive protection against web-based threats.





