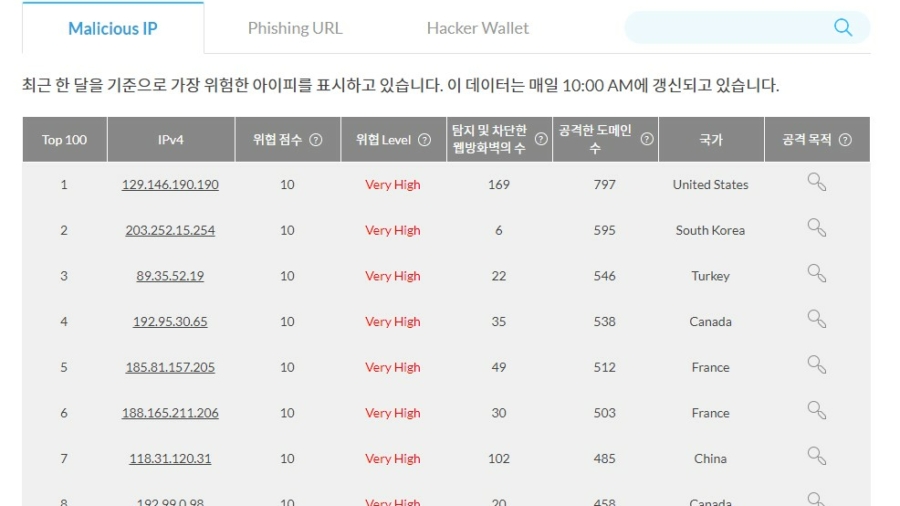
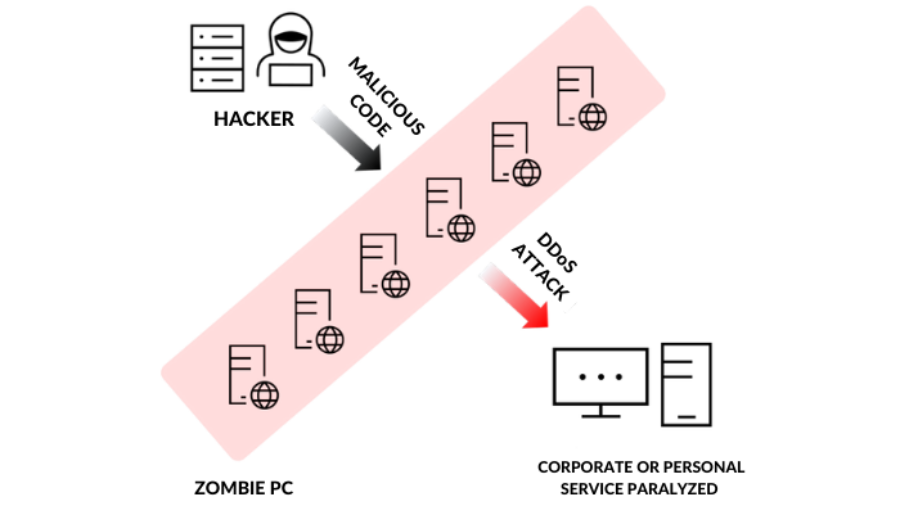
Cloud security company 'Cloudbric' announced on the 30th that it has launched a Malicious IP blocking service, which was previously provided in the form of an API. Now Cloudbric provides as a cloud security service in order to increase the ability to respond to intelligent and automated cyber threats and to improve security management convenience. Cyber threats are also on ...
Cloudbric launches Automatic IP blocking service for large-capacity threats
Cloud security company 'Cloudbric' announced on the 30th that it has launched a Malicious IP blocking service, which was previously provided in the form of an API. Now Cloudbric provides as a cloud security service in order to increase the ability to respond to intelligent and automated cyber threats and to improve security management convenience. Cyber threats are also on th ...
Ransom DDoS: “Give us Bitcoin or we will attack you”
Hackers are always finding new ways to transform traditional attacks to make a more effective and powerful cyberattack. Recently, an attack called Ransom DDoS or RDDoS attack has been targeting the financial sector. In this blog, we will discuss what an RDDoS attack is and how it threatens users. First threaten, then attack Ransom DDoS has a similar name to a cyberattack known as r ...
Virtual Private Networks (VPN): Is There a Downside?
Since the dawn of the internet, our privacy has been at risk. To paraphrase The Police—a heavy hitter band that dominated the airwaves in the 1970s and 1980s for those of you too young to remember—every move you make, someone’s watching you. From cookies quietly slipped into our laptops, tablets, and phones to surreptitious tracking of the paths we take in ...
Year in Review: Top DDoS Attacks In 2020
Since the COVID-19 pandemic started spreading across the world in the first quarter of 2020, a lot of day-to-day activities like shopping, work, food delivery, learning, and recreation have moved online. There has also been increased internet usage as people search for information regarding COVID-19. This shift to online activities has made government, health, media, retail, and othe ...
7 Tips on How to Recover From a Ransomware Attack
This guide will discuss the steps you can take to retrieve your data from a ransomware attack successfully. If you have experienced such an attack, you will agree that ransomware is one of the most dreadful experiences. Just imagine the scenario: You are working on your system, and suddenly a message pops up, indicating your system has been hijacked. And the only way t ...
DDoS Extortion Campaigns (Ransom DDoS, or RDoS) To Watch Out For
A ransom-driven DDoS attack is a new scheme performed by a group of cybercriminals that threaten to launch Distributed DoS attacks against unprotected companies. These groups extort victims by demanding ransom payments and intimidating them. Ransom DDoS can be so deadly because first, it creates fear, and second (if they are executed), they can hold the service of systems, websites, s ...
WAF and DDoS Protection: A Must-Have for Managed Security Services Providers (MSSP)
Web Application Firewalls (WAF) are one of the most important security technologies against denial-of-service attacks (DDoS). If you are new here, this is a type of cyberattack in which a malicious actor makes an online service unavailable to users by overwhelming a system with traffic from multiple sources. Simply put, a DDoS attack is more or less like a traffic snarl-up on the hig ...
What is cloud security? Can users keep the cloud 100% safe with the help of a WAF?
IT security is more than just managing a single server. Now, the growing popularity of the cloud environment is able to address the same internal and external threats within the field. Cloud service providers manage the cloud computing environment for companies, so does this mean that companies are free from all kinds of existing security problems? Not really. Cloud servi ...
9 Tips To Protect Your Business From DDoS Attacks
DDoS attacks are among the most complex and devastating cybersecurity threats that organizations struggle with today. While a blizzard of DDoS attacks continues through 2020, and many enterprises have already lost millions of dollars, 40% of companies are still unclear about how to protect their businesses. In this article, we will help you understand what a DDoS attack is a ...