"What do I care? I have nothing to hide." We all know some jerk who believes this. It comes up in conversations about surveillance, hacking, even airport security. The fact that you're wearing clothes means you have at least a couple things to hide. People need their secrets. Some information was not meant to be shared, and requires additional protection. But what kind of informat ...
9 Highly Effective Ways to Talk to Your CEO About Prioritizing Website Security
Online security threats are a rapidly growing menace. I know it, you know it, more than 37 million Ashley Madison users know it. So why is your CEO keeping the purse strings drawn tight? Your online business needs protection! Security often falls to the CIO, CTO, CISO, or even just an IT manager, and then everyone else might only pay attention when there's a security breach. Get Your CE ...
Ask Cloudbric: What Differences Are There Between Using Cloudbric and Not Using It?
Cloudbric received a lot of questions about our web application security service, and in our mission to democratize cyber security, we try our best to make the information readily available. We post a lot of answers in our Help Center, but every week we will give a longer answer about one question. This week, a user asks... What Differences Are There With or Without Cloudbric? We' ...
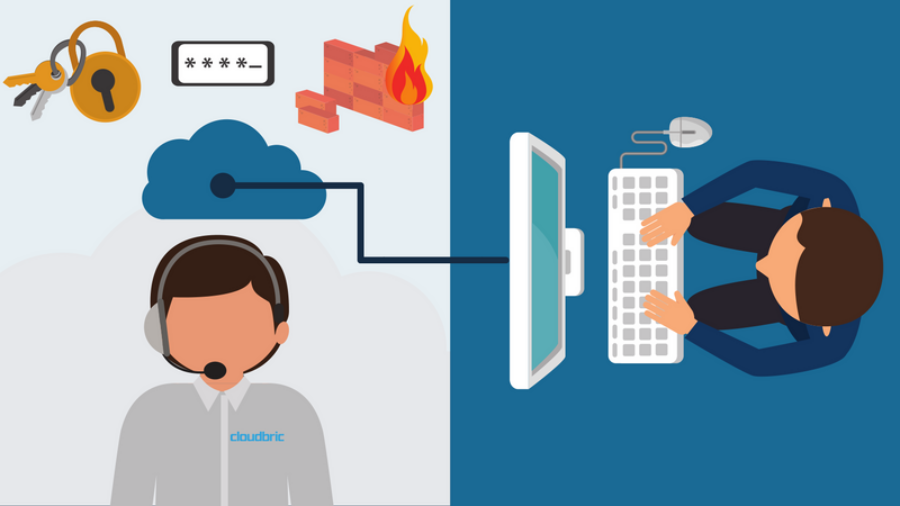
The Newbie’s Guide to Security as a Service (SECaaS)
There are a few things to look out for when outsourcing security to professionals via Security as a Service. What is Security as a Service? When you come across mention of “Security as a Service”, or “SECaaS” for short, people are most likely referring to web-based security solutions that are delivered over the cloud. However, Security as a Service is ...
3 Devastating Cyber Attacks on Banks That Show How Vulnerable Our Money Is
When it comes to online banking, there's no room for tolerating sloppy data security. You might not lose any sleep if your (hopefully unique) Adobe password is leaked and you may only experience a few minutes of rage if your Dota 2 game is DDoSed. But if your bank goes offline, better hope it's only for a few minutes and that your money is safe. These 3 Cyber Attacks on Banks Had D ...
Cloudbric Selected as a 2015 NCSAM Champion
October is National Cyber Security Awareness Month (NCSAM), a month-long campaign reaching out to the nation to encourage awareness and precautions. Sponsored by the Department of Homeland Security's National Cyber Security Division (NCSD) and the non-profit National Cyber Security Alliance (NCSA), this special program has been held annually since 2004. It is aided in this mission by ...
Ask Cloudbric: How Can I Show My Website Visitors I Use Cloudbric Protection?
Cloudbric received a lot of questions about our web application security service, and in our mission to democratize cyber security, we try our best to make the information readily available. We post a lot of answers in our Help Center, but every week we will give a longer answer about one question. This week, a user asks... How Can I Show My Website Visitors I Use Cloudbric Protection? ...
Who’s Behind DDoS Attacks and How Can You Protect Your Website?
DDoS attacks are increasing in intensity, frequency, and sophistication. So who's carrying out these attacks, and why? And what can you do to stop them? Despite all this innovating and evolving, DDoS attacks are still a blunt weapon deployed for one single basic purpose: to make target websites unavailable to users. There is very little else accomplished by a DDoS attack; they won't ...
6 Steps to Creating a Secure Website
There are roughly one billion active websites online, or one for every seven people alive right now. Every single second, a couple new websites are born into this world. That's a lot of websites, so how are they being created, and how do you make one? And also, how do you keep it secure from all the cyber threats out there?Secure Your Website With These 6 Steps The steps needed for maki ...