
“XSS” is an acronym you hear often in the field of information security as it’s a common attack found in web applications affecting both the client and the server. And while acronyms can fool you into thinking that it’s quite hi-tech and complicated, at the root of it, XSS is simply a con-artist, waiting for his next ploy.
What is XSS?
Short for Cross Site Scripting, this web vulnerability is a type of injection where the attacker inserts malicious script, or code, (more often than not, JavaScript) into a page. Failing to anticipate the malicious nature of this input, the script is passed through the application without proper validation as an “unsanitized” script. This unsanitized script is then allowed to remain in the browser and can be executed as if the administrator had written it.
With this, there could be a variety of consequences: attackers could alter the display, modify the browser, or even steal your session cookie and sign in as an administrator. The hacker may exercises complete control over the application and could manipulate it to deliver attacks to end users as well.
A great analogy to help explain this in simpler terms is to think of the XSS vulnerability as a con-artist’s latest trick. You never go out looking for a con-artist, but some way or another, they get you right where they want you.
Non-Persistent XSS: The Pickpocket
Pickpocketing is the oldest trick in the book, proven to work time and time again. It’s become a common and simple way for attackers to reach their target. The pickpocket may approach you as the “nice stranger” asking for directions on the street,but reaches for your wallet from your pocket while you’re kindly explaining directions. Though the pickpocket targeted you, when the ordeal is done and your money is gone, it’s as if it never happened.
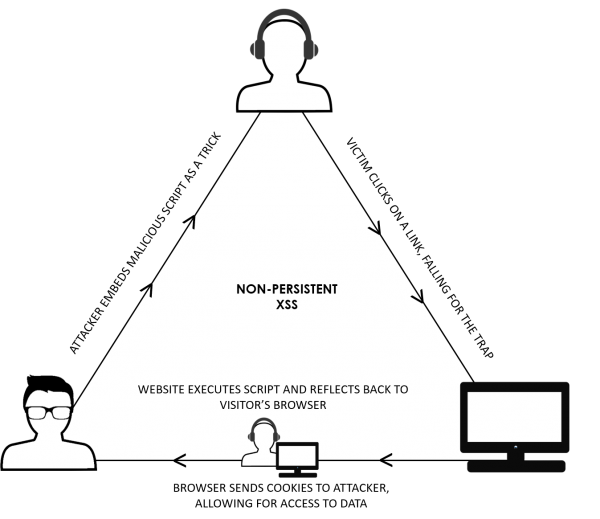
It’s the same with Non-Persistent XSS, the most common type of XSS where an attacker will inject targeted, malicious script into the vulnerable web application You click on it, and fall victim to the trap. But just like with a pickpocket, when the code is injected and you have been fooled, none of what happened goes to the server. The website will simply execute the script, reflect it back to your browser, and the cookies will go to the attacker. Immediacy and the lack of detectability are the highlights of these non-persistent XSS attacks.
Persistent XSS: The ATM Skimmer
On the other side, Persistent XSS is much less common. While it has the potential of causing more significant damage, it can also be discovered and remedied quicker. We can think along the lines of an ATM skimmer. A skimmer is an electronic device that is placed within or outside an ATM, soliciting information that a customer may put into the ATM. While the skimmer may look the same as the ATM that the customer uses on a daily basis, it is copying all information and relaying it to the con-artist. It’s non-targeted, so everyone who uses the ATM will be affected without discrimination.
With persistent XSS, like the ATM skimmer, the website may look the same as it usually does after the malicious script has been injected. It is saved by the server and then displayed on normal pages. All users browsing the website will be subjected to the XSS attacks, affecting users over and over again. Because damage can be done to a wider breadth of users without them noticing anything amiss, this type of XSS vulnerability is especially dangerous.
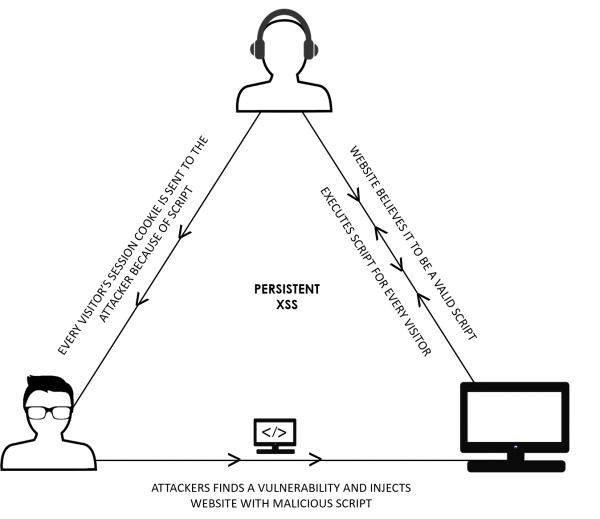
Fortunately, because persistent XSS takes place on a server, it can be remedied quickly if someone spots the unwelcome script. Returning to our skimmer analogy, picture the ATM maintenance crew noticing a missing bar code, or a warranty seal that’s in the wrong place. They can take quick and urgent steps to ensure the skimmer is removed and order is restored.
XSS Exploits in Real Life
XSS-affected websites can suffer from a variety of issues. Unfortunately, websites with a large number of active users are often affected through both persistent and non-persistent XSS. Earlier this month, an automatic Adobe Acrobat update forced a Chrome extension installation with an XSS vulnerability to users running Windows. This vulnerability, discovered and classified to be of “critical severity” by security researcher Ormandy, would have allowed for hackers to execute code or change privacy options. While Adobe managed to patch the vulnerability within a few days after being notified, security holes often go undetected by companies until severe damage is done.
Hackers will always find popular websites, big or small, to execute their attacks, so what can you do to protect your website?
Source Code Analysis: Source code analysis tools are used to find security flaws by going through source code line by line. Ideally, this tool will be used before the website goes live. This way, problems can be remediated before any issues arise.
Vulnerability Scanners: There are security scanners that will identify vulnerabilities like XSS. Although they’re not perfect (because they’re not optimized for your website or application specifically), they can help flag the most obvious vulnerabilities to clean up.
Web Application Firewall: Next-generation Web Application Firewalls or WAFs utilize rule-sets to detect or block anything suspicious. Such WAFs are capable of preventing XSS and SQLi attacks as part of their rule-set. Make sure your WAF has low false positive rates to ensure maximum site traffic.
Security as a service (SECaaS) platforms: Avoiding untrusted websites is simply not enough to protect yourself from an XSS attack, but a WAF can also be an expensive and bulky appliance for those starting out in setting up website security. To prevent infections, consider adopting security services such as anti-virus, anti-malware/spyware, and cloud-based website security. Outsourcing security to an external party ensures you always have experts looking after your website.
That’s it! You’re well on your way to having a safer, cleaner website. So which method is the most effective? There’s no perfect way to escape any form of web attack. But the best thing you can do is follow the points above like a process. Source code analysis tools will scan for flaws before anything goes live. Vulnerability scanners will then look for further issues as the website is up. A WAF will block the attempts that manage to slip through the cracks. Unfortunately, nothing is foolproof, but risk can always be minimized and controlled.





