The Age of Cyber Warfare; Are We Safe from Cyber Attack?

Commencing with the Kosovo War in 1999, often regarded as one of the early instances of cyber warfare, we have witnessed significant developments. Operation Orchard in 2007(when the Israeli Air Force employed Trojan horses to neutralize Syria’s nuclear facilities), the Russia-Georgia war in 2008, followed by the Russia-Ukraine conflict, had widespread global repercussions.
Additionally, the recent Israeli-Palestinian Hamas conflict demonstrated how, in just over two decades, the epicenter of conflicts has rapidly shifted from traditional battlegrounds to the digital realm.
Era or Cyber Warfare
In recent times, conflicts have evolved into what is commonly referred to as hybrid warfare, encompassing both military and non-military strategies. As we transition beyond the era of conventional warfare reliant on high-tech weaponry, a new form of warfare is emerging, marked by cyber battles, guerrilla tactics, and information warfare. This transformation underscores the growing importance of cybersecurity, as indiscriminate cyberattacks now pose a significant threat to nations worldwide.

At the onset of the conflict on October 7, 2023, hackers from around the world joined the aggressiveness. While the news may present the situation in Israel’s Gaza Strip as a conventional war zone, with missile attacks, tank units on major roads, and gunpoint pointing at each other, the reality includes not only intense ground combat but also large-scale cyberattacks.
Early in the conflict, a hacker group launched DDoS attacks on Israel’s government websites and media outlets, persistently targeting the country with cyberattacks, including data theft, intrusion into Internet Service Providers (ISPs), and tampering with Israeli missile alert systems.
Since Hamas’s preemptive strike, both sides engaged in cyber warfare, deploying various cyberattack methods, such as hacking and DDoS attacks, affecting numerous Israeli and Palestinian websites and applications.

In a recent digital defense report, Microsoft unveiled the tracking history of a Gaza-based hacking organization known as Storm-1133. Microsoft suggests this group operates under the order of Hamas, primarily targeting organizations in Israel’s energy and defense sectors.
Their primary attack method involves spear phishing, where they impersonate human resources managers, project coordinators, and software developers. They then inject malicious code into employment or development inquiries, compromising the personal information of prominent Israeli figures and infiltrating company networks.
Cyberattacks on critical national infrastructure have become increasingly common in regions marked by high geopolitical competition, posing a significant threat to national security.
Influence of Global Cyber Warfare towards South Korea
Microsoft has warned that cyberattacks targeting critical infrastructure will persist during the Israeli-Palestinian Hamas conflict, and major targets include Israel, the U.S., Ukraine, and South Korea.
This is not the first time that South Korea has been a significant target of cyberattacks. During the escalation of the Russia-Ukraine conflict in early 2022, which spilled over into a cyberwar, the Korean government took preemptive measures to counter potential cyber retaliation against countries involved in sanctions against Russia.
On March 21, 2022, South Korea’s National Intelligence Service raised the national cyber crisis alert to ‘caution’ in the public sector, and the Ministry of Science and ICT also raised the national cyber crisis alert to ‘caution’ in the private sector on the same day. These cyber crisis alerts are issued when there is an increase in cyber threats to the nation, its public institutions, and critical social infrastructure.
The issuance of these cyber crisis alerts highlights the importance of preparing tailored security measures for various organizations’ system environments to counter cyber threats. This includes government agencies, public institutions, and private companies.
Response Strategies against Cyber Attacks
In the face of a rising number of cybersecurity incidents like DDoS attacks and hacking, the Korea Internet & Security Agency (KISA) has called upon agencies and companies to fortify their security management systems. It is crucial to ensure the reliability of critical systems and security equipment, establish robust security policies, and minimize unnecessary exposure to the Internet environment.
However, many companies, especially those lacking dedicated security professionals, find it challenging to bolster their security measures. Even organizations with security teams can struggle with managing vast amounts of data and threat intelligence. One effective solution to these challenges is to adopt a managed web security platform.
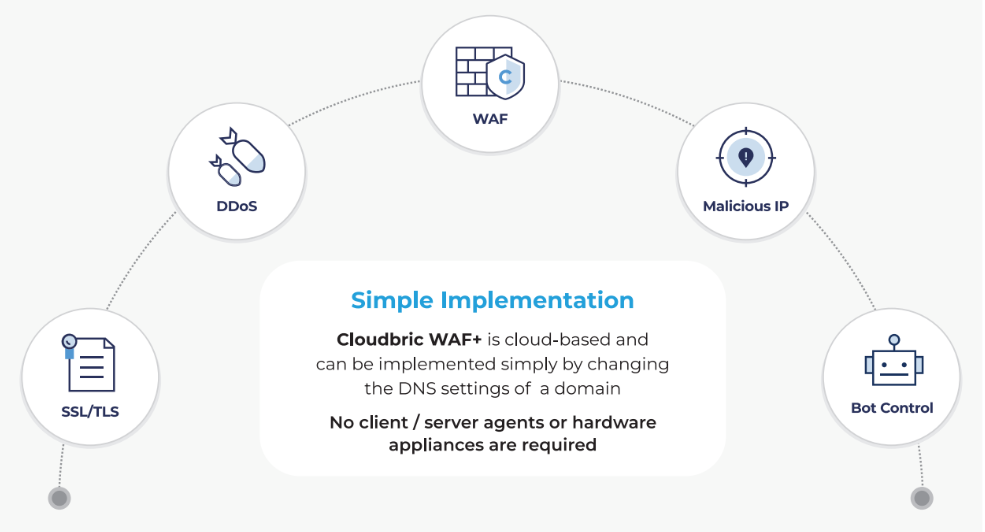
Cloudbric’s Fully managed security solution Cloudbric WAF+ offers a comprehensive, cloud-based security service managed by security professionals. With Cloudbric WAF+, customers can create a secure online environment, benefiting from essential enterprise web security services such as a fundamental web application firewall (WAF), SSL/TLS protection, DDoS mitigation, malicious bot control, and blocking of malicious IP addresses.
📌 Learn more about Cloudbric WAF+
Preventing and addressing cyberattacks is essential in preparing for cyber warfare within the global community. Cloudbric is committed to establishing a secure web security environment capable of countering increasingly powerful and sophisticated cyber threats. Stay tuned and stay vigilant!





