Rarely do things come easy within the business world, especially within the information security sector. Various misconceptions are often made concerning best practices when approaching information security, but hopefully this article can help clear some things up in order to help small/large business pursue cyber protection efficiently and become more familiar with IT structure.
Information Security Means Building A Safe IT System
If one tries to categorize all potential information security damages, one will notice that these damages are all heavily related to the structure of the IT System. As illustrated below, there are three primary layers to an IT System consists of three layers. By understanding these layers, one can know that each layer serves different purposes and handles different information (data). At the same time, information security breaches are also different within each layer. Once one understands what types of breaches can happen in each layer and the security measures that need to be applied for each layer, a strong IT System can be supported.
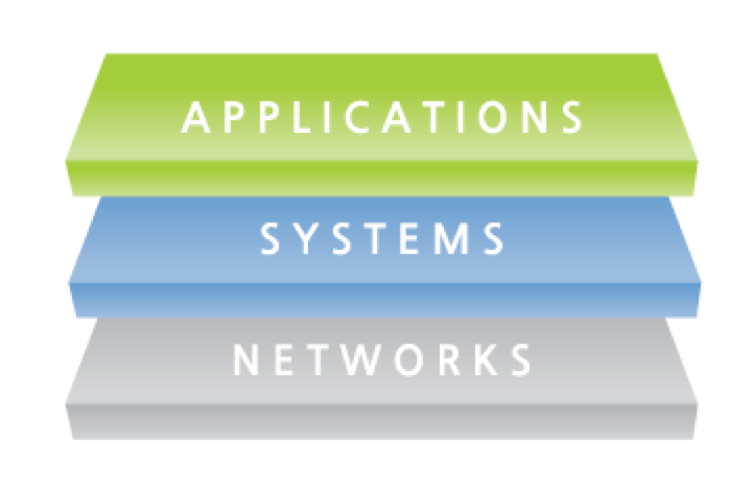
Think of the internet as a network, and the system as operation system such as Windows or Linux. Applications within each operating system then indicates the programs we use. To be more specific, within the IT system’s structure, the network deals with “packets”, which is like a box of information, and systems deal with files, which is the type of information collected and lastly, applications deal with the actual content.
SSL Communication Only Takes Care of the Safe Packet Delivery
SSL (Secure Socket Layer) is the encrypted communication method for transferred data via the web. SSL can also be defined as, “a computer networking protocol that manages server authentication, client authentication and encrypted communication between servers and clients.” Web pages with SSL use the port ‘https’ while the normal web page uses ‘http’ port. SSL technology is applied on a network layer, so it deals with the ‘packet’ as mentioned earlier. Although SSL is required for eCommerce and is known for safe communication, it’s not the panacea. There are many vital steps to creating a secure website. SSL typically only secures the information on the network layer and web attacks that target the system or the application cannot be blocked by SSL. If you see a phrase such as “this website is safe because we use SSL” this is only half the truth. What if the contents are already infected? SSL only takes care of the delivery of the packet, so it doesn’t guarantee the system’s security.
Anti-virus Can Secure the System Layer?
If the packet is broken down, it becomes data, and often its format is type of file, which is associated with the system layer. Among many security technologies for system layers, vaccines or the anti-virus are well known. In order to protect the IT system, anti-virus tries to find a file with security vulnerabilities and either removes the file or cures it. This is a common information security measure taken by individuals and it is helpful, but too trust shouldn’t be given the the anti-virus alone. Anti-viruses can detect very limited security threats, especially when it comes to the new types of attacks.
Secure Coding is the Best Way to Secure the Application Layer?
The application layer is the most important layer because most web attacks such as SQL injection or cross site scripting (XSS) occurs at this level. These types of attacks are not only the most common, but also the most dangerous forms of web attacks. In 2014, SQL injections were responsible for 8.1% of all data breaches reported for that year. Different from other layers, the application layer handles data that is readable by humans. Humans cannot read packet and data, but they can read code information from the application layers. This is why hackers target the application layer. Hackers can pose as an authorized user and pass through the network and system layer security measures, then interacting with the web server. To prevent this, maximal secure coding is considered as a solution, but this is not more than a textbook solution. Making an application with vulnerabilities sounds perfect, but realistically, while developers do not dedicate themselves in building the perfect application without vulnerabilities, hackers only focus on finding vulnerabilities.
What Would Make the Most Secure IT System?
If you secure all three layers, you can build a secure IT system. However, more practically speaking, you need to pay extra attention to the application layer. There are many security technologies and tools available to secure network and system layers, but the application layer has been underestimated, and this can be backed by the adoption rate of web application firewall. 100% security is not possible to achieve, but with the proper web application firewall, application layers can optimally protected.





