Key Differences Between Web Firewall and Firewall
In this modern era of sophisticated and advanced cyberattacks, it is crucial for organizations and businesses to understand and deploy the right protection solutions. Before companies deploy a type of firewall (whether application or network), it is important to acknowledge the different types of attacks they each protect. Firewalls are mainly installed to reduce damages in the event of threats or cyberattacks and these firewalls used in the network environment are similar to the firewalls installed in the building that prevent the spread of fire by constructing a wall that extends from the foundation through the roof with a prescribed fire resistance duration and independent structural stability.
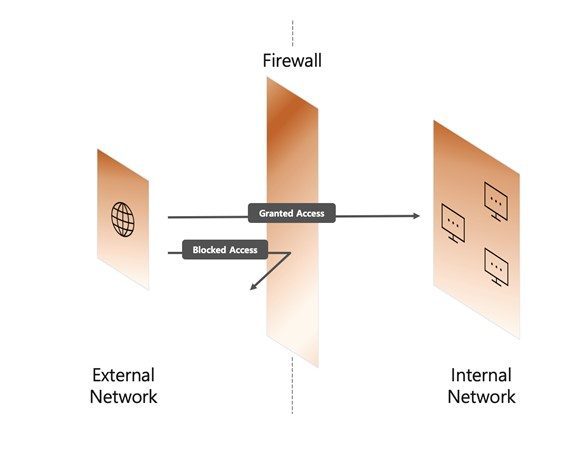
The firewall aims to prevent the threat of illegal users gaining access to the communication network in use and disturb the server or obtain information and leak it externally. It serves to protect the internal network by first controlling unauthorized access from the external network by selecting information transmitted between the network and the internet.
Web Firewall and Firewall
So what’s the difference between a web firewall and a firewall?
The biggest difference between the two is that the layers they operate on are different. The firewall is responsible for securing the network and transport layer, and the web firewall is responsible for securing the web application layer. If the firewall manages access to the IP address of the network layer and the port number of the transport layer, the web firewall is in charge of securing the web application layer to defend against attacks based on real data and application protocols.
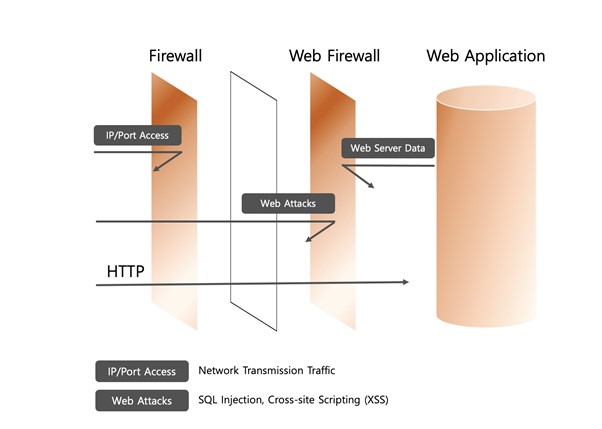
In short, a web firewall detects and blocks web attacks that may occur within access allowed by the firewall. It controls the server by manipulating the code and prevents frequent web attacks such as SQL Injection that leaks data information, and cross-site scripting (XSS) that attacks by allowing other users to browse the web page containing malicious code.
In addition, a web firewall not only directly responds to web attacks, but also realizes various security measures such as information leakage prevention solution, unauthorized login prevention solution, and website forgery prevention solution.
The Evolution of Web Firewall
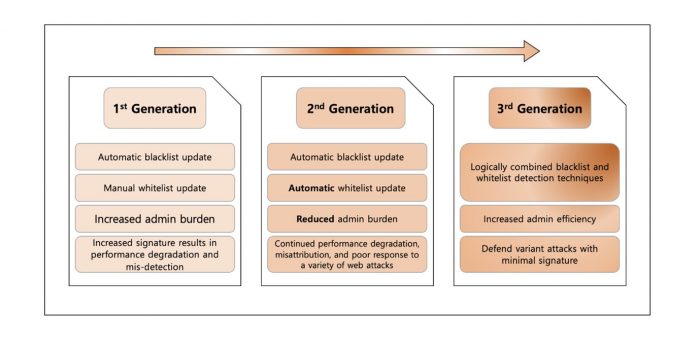
As the attack methods and scope of web utilization increase over time, more and more security flaws were found within organizations. Also, types of attacks aimed at them diversified over time and web firewalls have also steadily developed accordingly. Recently, the concept of a next-generation firewall that provides more robust and simple security functions by complying with international standards and other network security devices beyond the 3rd generation firewall (intelligent firewalls) has become the essential security measure for protecting the enterprise environment.
As the corporate work environment became more digitized, and in particular, as the digital transformation caused by the pandemic has accelerated the industry, working from home and using various devices and software became the new norm. In such environments, blocked ports or protocols are often bypassed for the convenience of access, making them the target of cyberattacks. Therefore, it is vital to deploy a dedicated firewall like Cloudbric WAF+ that protects the entire system in addition to blocking basic web attacks. Cloudbric WAF+ effectively guards against sensitive data leakage, blocks malicious web access, and prevents website defacement in this era of intensified attacks.
The engine of Cloudbric WAF+ is equipped with a logic-based detection engine and patented A.I module to provide the highest security standards all over the world. The combined technology Cloudbric can detect and analyze web threats by parsing the actual code in the traffic: this allows us to ‘understand the intent’ of the hacker and provide the user with a detailed security intelligence.
Source : https://www.pentasecurity.com/blog/





