Internet phishing scams often use fraudulent websites to impersonate legitimate and steal your personal information. But that is not all; a website might be legitimate, but have the wrong intentions. Sites like this typically offer freeware that ends up installing malware, crypto-mining, bloatware, or botnet software.
Additionally, it might be that a website is legit and well-intentioned but it’s highly insecure. If it lacks the proper security protocols, such as HTTPS, hackers can easily launch a Man-In-The-Middle (MITM) attack and intercept your traffic. A hacker might also inject Javascript code or craft an SQL statement to steal a website’s user databases; there goes your name and credit card details.
Once you give your sensitive data to a site, it is up to them to take care of that data. So how can you make sure a website is safe and secure?

In this post, we’ll explain three best practices to know if a website is safe, secure, and trustworthy. We’ll look at, first, verifying if it is using HTTPS (and not HTTP); second, discerning that it is not an impersonated website; and, third, looking for different signs of trustworthiness. We’ll close with some advanced recommendations.
- Verify you are using HTTPS and not HTTP
- A. The SSL certificate
- B. What can you do?
- Identify impersonated websites
- A. An example
- B. What can you do?
- Look for trustworthy signs
- Final Recommendations
1. Verify you are using HTTPS and not HTTP
If you have ever encountered the infamous browser’s message “Your connection is not private,” this means that you were at risk of exposing sensitive information. In this situation, Google Chrome will show the following:
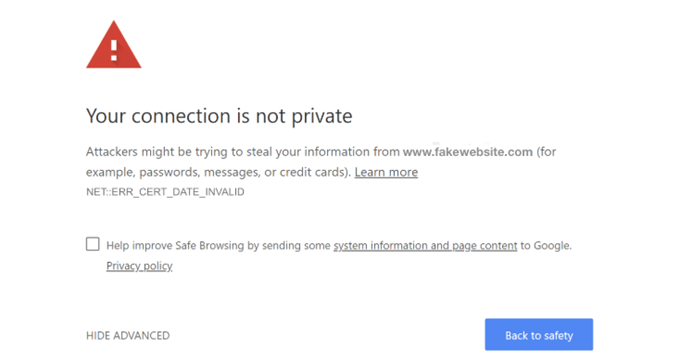
While Mozilla Firefox and Microsoft Edge will show the following message:
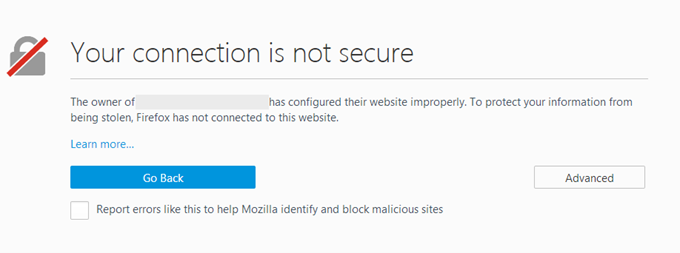
Messages like this are due to two reasons, namely that:
- The connection is not encrypted
- The web server can’t be verified
If the messages between your browser and the webserver are unencrypted, anyone between your traffic (ISP, coffee shop’s WiFi owner, network manager, CDN, etc) could be able to intercept and read your plain-text data. Additionally, the web browser (HTTP client) will be unable to ensure that it is connecting to the right server and not a spoofed one. This is why HTTPS (TLS/SSL encryption) was born.
A. The SSL Certificate
SSL certificates help websites transition from the unsecured HTTP to the secure HTTPS. Put simply, these are datafiles stored in the origin web server that contain a public key. In this way, the SSL certificate ensures SSL/TLS encryption between browser and web server, as it contains the original website’s public key and identity.
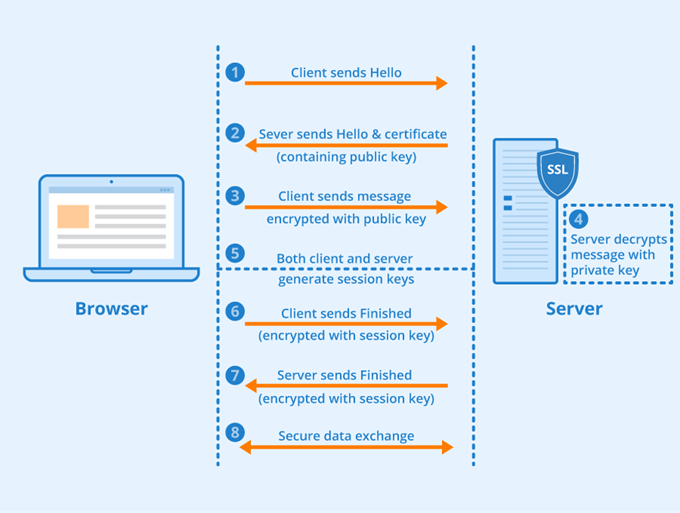
How SSL works
- To browse a website, a client (web browser) must first request HTTPs service to the origin server
- The server replies with an SSL certificate that includes a public key
- The browser (client) verifies the certificate’s trust and integrity to validate the server’s identity and uses the public key to encrypt data. In asymmetric encryption, two keys are used: A public key for encryption, and a secret private key for decryption
- The server decrypts the data using the private key
Your browser will issue warnings like “your connection is not private” or “your connection is not secure” because it doesn’t want you to interact with the web server’s SSL certificate. It might be either, missing, expired, or wasn’t issued by a legitimate Certified Authority (CA). A website without an SSL certificate has no way of proving its identity.
Bear in mind that some pro scammers are capable of displaying the green padlock that indicates a secure connection or HTTPS (SSL) which can mislead a user into thinking the website is 100% secure.
Can SSL certificates be faked or real ones compromised?
Technically, a hacker could issue a self-signed SSL certificate and install a fake root certificate on a user’s machine although this would require some sort of MITM or DNS spoofing.
- Real certificates can also be compromised, as seen in 2011 when a group of Iranian hackers obtained a series of nine fraudulent certificates. According to a report, they hacked into a known CA, Comodo, to accept the Certificate Signing Request (CSR) themselves. A compromised CA certificate,and especially the global trustee or root certificate, could have been used to impersonate any domain on the web with HTTPS; this could have been a disaster. Fortunately, the certificates were revoked within a couple of hours.
B. What can you do?
It is recommended that you only access sites with SSL certificate since browsing without HTTPS opens the door for data breaches. 
If you are using HTTPS, the browser will show the padlock, (or HTTPS://), which means the browser has established a “Secure Connection”. If the browser is not recognizing the SSL certificate (thus displays the error message), try reloading or updating the web browser, or refresh and clear history. Also, try synchronizing your clock, so that the certificate is not taken as expired.
- Always update your browser. This ensures the latest root certificates are installed on your browser.
- Use standard browsers. Popular and standard browsers come with the latest trusted CA’s certificate.
- Secure your communications. To avoid MITM attacks, improve authentication in your LAN, and WLAN, and set up a secure remote access between source and remote servers.
2. Identify Impersonated Websites
Phishing scams or fraudulent websites use some form of social engineering to lure victims into accessing an imitation of a legitimate site. The victim is tricked into entering their account information, and if they don’t have a trained eye, all of their credentials including, credit card information, Social Security Number, and even a scan of their ID could fall into the wrong hands.
To drive traffic to these sites, scammers send massive numbers of spam emails containing the link to their fraudulent site. This process is known as Phishing. The scammers register new domain names and create websites (even copy their HTML) that look a lot like legitimate ones, including banks, Amazon, PayPal, etc.
A. An example
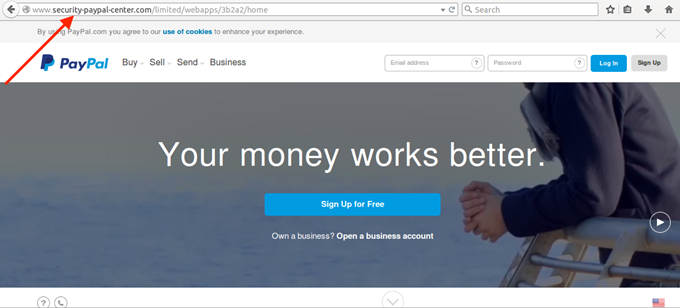
According to a report from Cisco, there has been a wide number of PayPal impersonation sites with unusual domains, which have already taken in some traffic from victims.
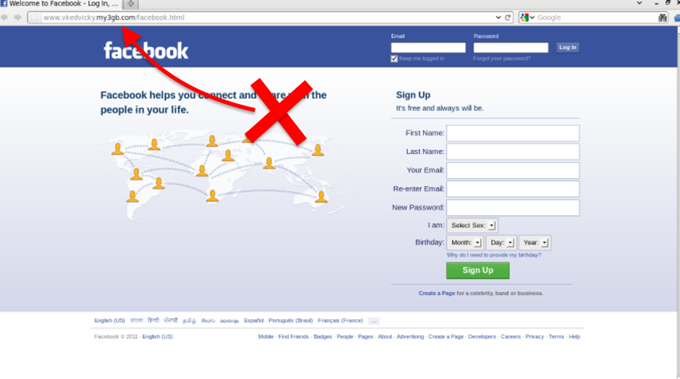
Another example is an impersonated Facebook page, the URL does not match the content.
B. What can you do?
Before you give away any personal data, consider the following recommendations.
- Use spam filters. Configure your email to filter spam out of your inbox. For example, Gmail has anti-spam intelligence technology that can filter a big percentage of spam. Still, one or two emails might make it into your main inbox.
- Take the no-trust approach. If a request to a service or site wasn’t initiated by you— raise the red flags of suspicion. Don’t fall for big logos, bold letters, or demanding words requesting something from you. Even if it looks legitimate, never click on any link, especially if you don’t have an account with that company. Check the FTC for the guidelines on how to spot a phishing scam. It is sad but true, the Internet can be as wonderful as it is deceiving.
- Always check the URL. Even if a site’s content feels and looks real, the URL will not. Always inspect the site’s content closely and compare it with the URL. For example, Paypal.com is the real URL of Paypal. Of course, along with a big domain like that, there will be legitimate subdomains, like developer.paypal.com or shopping.paypal.com. But then, there are those fake domain names that look real, for example, pay-pal.com, x-paypal.com, securitycheck-paypal.com, paypalinspection.com, or area-paypai.es. Read more on the hierarchy and structure of DNS to be sure.
- Find out who owns the domain. Use domain registration services using WHOIS that query databases that store the registered user or name of an Internet resource, in this case, the domain. If “Mr. Anonymous” is the owner of that PayPal domain and not PayPal Inc., it might be time to trust yourself and not Mr. Anonymous.
3. Look for Trustworthy Signs
Again, before you enter sensitive information on a website, you must make sure that it’s safe and secure. A site can be secure if it is encrypted, the server is verified, it is malware-free, and the URL matches the content, but still, it can be unsafe.
There are a number of signs to help you determine if an online company is safe or not.
- Contact information. Contact Us page, social media, phone number, physical address, and email address (with a private domain) will demonstrate that a website wants you to get in touch and that they are real. A social media presence is a big indicator that the company is “out there” and that others know about and trust it.
- ‘About Us’ page. The “About us” page aims to outline the site’s intentions, its history, where the company is based, and who they really are. This kind of page can obviously be fictitious, but if you don’t see one at all, your suspicions should be raised.
- Privacy policy. It takes time and money to build a proper privacy policy. If you don’t see one, and the company wants your data, stay away. If you do see one, that is a good sign. But still, you may want to go through the policy. Some web services or application providers collect your data and sell it to third parties and might even use your resources, for things like Botnets or crypto-mining. Before you buy or download anything for free (especially free VPNs or Proxies) always check the Privacy Policy. Read more about VPNs leak data.
- External guidance. A quick Google search on reviews or forum posts by real users (or victims) can give you the upper hand about a site’s reputation.
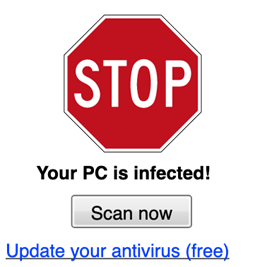
- Malvertisement and pop-ups aiming to provoke your emotions. Scams and phishing schemes work because they work on the emotions of the victims. As such, avoid all “too-good-to-be-true” offers, last-minute deals, and free stuff as well as messages about infected machines or, redeeming your Amazon gift card. Trustworthy companies use a return or refund policy to build trust with new customers if a site doesn’t provide this, it is probably because it is hiding something.
4. Final Recommendations
Your connection between (client) browser and server (website) might not be secure.
Although we’ve discussed thoroughly about unsafe and unsecured websites and how to stay safe, there are other weak points along the way that could compromise your privacy.
Whether your traffic goes to either a safe or unsafe website, it can be compromised by these middle points. Your local ISP, the coffee shop owner of the network you’re using, the neighbor with your WiFi password, or the IT manager of a large building, could potentially be participating in or the victim of a hack or scam. A hacker could perform a Man-in-the-Middle (MITM) attack and redirect all of your traffic or a DNS spoofing attack in which a corrupt DNS cache is introduced to divert your traffic to a malicious web host. Advanced hackers can even hijack DNS infrastructure to redirect the traffic itself to illegitimate sites.
Protecting DNS infrastructure is outside the scope of this article, as it should be the responsibility of DNS providers. That said, you can opt to use known safe public DNS servers such as Google’s (8.8.8.8), which supports DNSSEC.
How to stay safe amidst these other vulnerable points?
- Update all of your software, including the OS and browser.
- Never click on suspicious URLs, and make sure you are always on HTTPs (SSL Certificate). The green padlock is a good sign.
- When transferring sensitive information on public WiFi, use remote access solutions that support 2FA and block malicious traffic.
- Update to the latest version of TLS (TLS 1.3, as of May 2021), and make sure that you support DNSSEC and encrypted Server Name Indication (SNI).





