A Software Defined Perimeter (SDP) is a representative architecture that implements Zero Trust security principles in network access control. SDP aims to significantly reduce the network attack surface by completely hiding the existence of applications and services from unauthenticated and unauthorized users. In this way, organizations can strengthen Global Cybersecurity posture while al ...
What is Zero Trust Network Access (ZTNA)?
Zero Trust Network Access (ZTNA) is a next-generation remote access security model designed to replace traditional VPN-based perimeter security frameworks. As a core technology for implementing the principles of Zero Trust security in operational environments, ZTNA enforces application-level access control and grants even authenticated users only the minimum privileges necessary for thei ...
What is Zero Trust
What is Zero Trust? Zero Trust is a next-generation cybersecurity strategy built on the core principle of "Never Trust, Always Verify." Unlike traditional perimeter-based security models, Zero Trust treats every access request—regardless of origin, device, application, or transaction—as a potential threat. This model enforces continuous identity and access verification for all users and ...
How to Simplify Cloud Web Security in the Era of Cloud Expansion
Today, many enterprises are moving beyond single cloud environments and actively adopting multi-cloud and hybrid cloud strategies. As IT infrastructures expand across different platforms, cloud web security has become a foundational requirement for protecting business-critical services. Organizations now leverage multiple cloud providers based on operational needs and business objectives ...
Automated Bot Attacks: Trends and Response Strategies
Automated bot attacks have become one of the greatest threats in the web security environment. Recently, bot traffic has even surpassed human traffic in overall web sessions, significantly expanding the security risk. Traditional script‑based attacks have already shown their limitations, and the need to counter increasingly sophisticated automated attacks is growing.At the heart of this ...
What is a VPN (Virtual Private Network)?
A VPN (Virtual Private Network) is a core cybersecurity technology that enables secure data transmission over public networks, such as the internet, as if it were a private network. By applying encryption and tunneling methods during data transmission, a VPN protects users’ identities, locations, and data contents, keeping sensitive information safe from eavesdropping or hacking attempts ...
What is SaaS (Software as a Service)
With the rapid advancement of digital technologies, corporate IT environments are being reshaped at unprecedented speed. Traditional on-premises models, which require significant time and resources for infrastructure setup and maintenance, are increasingly showing their limitations. In response, companies are seeking more agile and flexible approaches to IT operations.SaaS (Software as a ...
Cloud Security in the AI Era: How Cloudbric Managed Rules for AWS WAF Defend Against Agentic AI Risks
1. Introduction: The AI & Agentic AI Security Paradox Artificial Intelligence is reshaping every industry in 2025 — from customer service to autonomous software agents. Generative AI and Agentic AI (self-directed, autonomous AI systems) promise unprecedented productivity. Frameworks like the Model Context Protocol (MCP) allow AI agents to integrate with external tools and APIs, ma ...
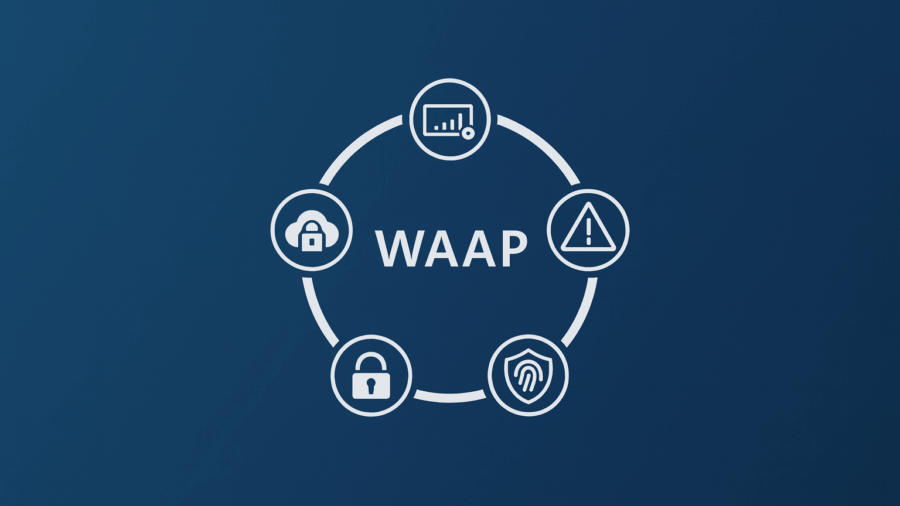
What Is WAAP (Web Application and API Protection)?
To address the complexity of modern web environments and the growing sophistication of cyber threats, WAAP (Web Application and API Protection) has emerged as the new standard for integrated security solutions. Defined by analysts at the global IT research firm Gartner, WAAP goes beyond traditional web application firewalls. With the rise of microservices architecture and API-driven deve ...
UK Online Safety Act Triggers Surge in VPN Use
UK Online Safety Act Triggers Surge in VPN Use: What It Means for Digital Privacy In July 2025, the UK’s Online Safety Act officially enacted its child protection provisions, sparking an unexpected phenomenon: VPN usage surged by an astonishing 1,400% to 6,000%. This dramatic rise is more than a statistic—it reveals deep public concern over digital privacy and internet freedom in the UK ...