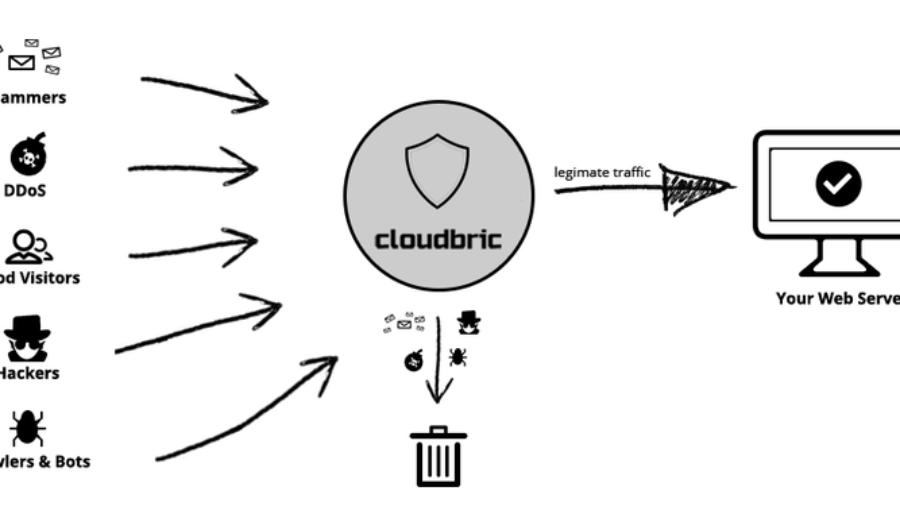
According to Fortune Magazine, many startups fail because they run out of money or they lack experience. This is probably why users are reluctant to sign up and start putting their data. Even if the product is targeted, designed and marketed really well, the situation is not so stable. How can we use the innovative products and services without having to worry about shutting down?&nbs ...
Buffer Overflow, a Common Attack Mechanism
Data can exceed a buffer's capacity Not many people may know or have heard about buffer overflow, but Cloudbric is here to help you understand this dangerous web threat. To put it simply, most programs that run in our computers manipulate data of some form. This data could originate from data associated with the program or logged data that is stored on your computer. The computer ...
Reflection Attacks and Amplification Attacks
Here are two types of attacks that are intended to monopolize your system's resources. Reflection Attacks Reflection attacks (also known as DoS (denial of service) reflection attacks) are attacks that use the same protocol in both directions. The attacker spoofs the victim's IP address and sends a request for information via UDP (User Datagram Protocol) to servers k ...
What Are Application Level Attacks?
An application-layer attack targets the layer of the internet that essentially faces the end user. This layer, also known as layer 7 in the OSI (Open Systems Interconnection) model, includes applications that you are used to accessing yourself online.Traditional DDoS attacks, such as ICMP and SYN floods, as we mentioned earlier, still challenge network operators; however, the detect ...
Attack Agents and Bots
Zombie cartoon So, we gave you guys a pretty good overview about DDoS attacks and how they are carried out. In case you missed it, check out DDoS Part 1 and Part 2 here. One of the critical parts of a successful DDoS attack relies on bots or a botnet. Botnets are groups of zombie computers under the remote control of an attacker via a command and control server (C&C Server). T ...
Types of Attacks – DDoS Part 2
Cloudbric provides comprehensive web security Today, we will continue our discussion based on the Types of Attacks - DDoS Part 1. This will be a more in-depth look at how DDoS attacks are carried out. Let's get started! Ping Flood Attacks This is a type of DDoS attack where an attacker focuses on ping flooding the ICMP packets of a victim's network. This is more successful car ...
Types of Attacks – DDoS Part 1
Hackers can take over the world OK, so we now live in a world where even a 7-year-old can break into a public network and essentially hack a website. Hacking can be that easily and the information on how to do it properly is so widespread. Now is not the time to just overlook the issue and brush it off. Your precious information is leaking somewhere on the internet and you might ...
How Safe is Your Website? – Part 2
Login credentials for computers In this second part of "How Safe Is Your Website?", we wanted to add one more attack variation that we think you should know about. The really popular way for hackers to access your website is through an attack called an SQL Injection. Here is a short post about SQL Injections and why they can be dangerous. What is an SQL Injection? SQL Injections ...
How Safe is Your Website? – Part 1
When it comes to web security, people really have no idea how vulnerable their websites can be. The majority of people aimlessly browse and post private information to share with friends and coworkers. One thing you need to keep in mind is that once it's up on the online space, then it can and will be accessed by unauthorized viewers. Posting updates to your social networks can seem ...
3 Tiers and OWASP (Open Web Application Security Project)
Cybersecurity is the hottest topic of the month. With the latest hacking news surrounding Sony, all the attention has been placed upon North Korean hackers and cyber-attacks! With Obama declaring this incident as an act of terrorism to the chaos over the opening of The Interview, it's time to take this matter into our hands and learn about web security! Various Tiers Today, ...