People install CCTVs and alarm systems to prevent trespassers from entering their home or their office. But how about IT companies that have a lot of expensive products and sensitive data?
Due to time and cost difficulties, it is actually hard to apply equally high-level security in your office, home, and IT environment. That is why you should focus on securing the place with the most risks. That is the web application layer in the IT environment.
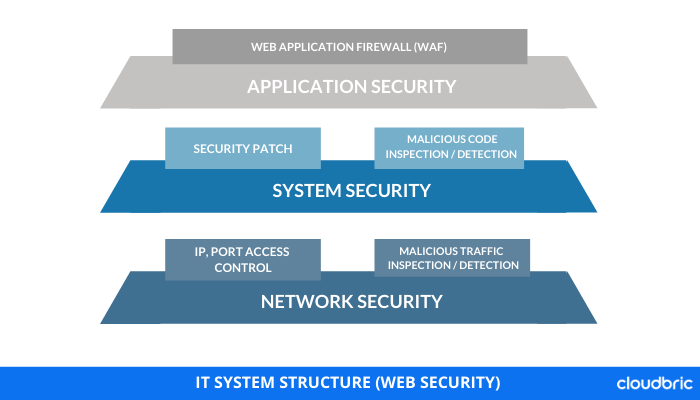
In the IT environment, the OSI model can be largely divided into three layers: Network, System, and Application layer. These three layers interact with each other to build a secure system.
Among the three layers, the application layer is the 7th layer in the OSI model and the closest layer to end-users. This layer directly interacts with the application and provides common web application services.
More than 75% of hackers are targeting the web application layer because websites and mobile apps we commonly use are all made of applications. To prevent hackers from hacking your website, adopting a WAF (Web Application Firewall) is one solution.
Compared to the number of hackers targeting the web application layer, companies tend to overlook this layer. Based on a company’s security budget, only 10% is being invested in protecting the application layer, and 90% is being used for protecting the network and system layers. And hackers who can’t afford to miss this gap are targeting the application layer.
That is the reason why companies must adopt a WAF (Web Application Firewall) to prevent cyberattacks. 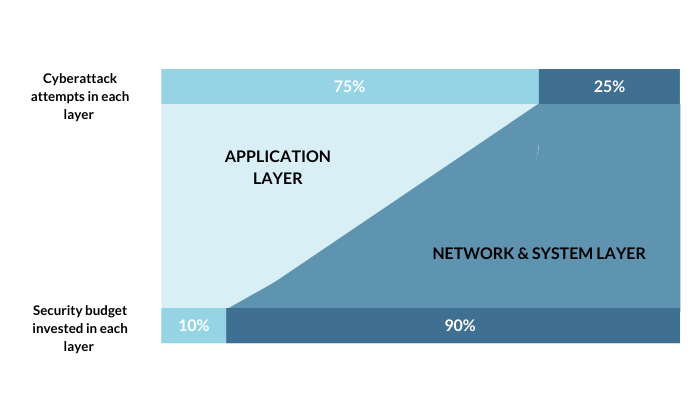 Above we have discussed the three layers (Network, System, and Application) and the reasons why companies must protect the application layer. Here are some guidelines in choosing a good WAF (Web Application Firewall):
Above we have discussed the three layers (Network, System, and Application) and the reasons why companies must protect the application layer. Here are some guidelines in choosing a good WAF (Web Application Firewall):
Basic functions of a WAF
As the name implies, WAF is a solution that is optimized for web application security. Below are the 4 basic functions of a WAF:
- Respond to web attacks
- Prevent data leakage
- Prevent unauthorized access
- Prevent web forgery
Together, they prevent web application attacks and OWASP Top10 vulnerabilities, such as SQL injection, Cross-site Scripting (XSS) attacks, and DDoS attacks.
Three checkpoints in choosing a good WAF
So what other functions should companies check before adopting a safe and effective WAF with just a limited budget? There are many factors to consider when choosing a good WAF, but the most important three points to keep in mind are user-centered, accurate detection capability, and fast detection rate.It may seem obvious, but every WAF product has its differences but these three main points are a must to be checked.
1.User-centered
‘Although the security is good, wouldn’t it affect the speed of my website or require additional cost and time to manage the service?’ Anyone who is considering adopting a WAF has thought about this problem. But if it’s a good WAF, then it should not let users worry about it.
– Automation function
Automation function is required in a WAF because there are limits to your IT staff in responding to cyber threats. The automation function in a WAF can resolve problems on its own, or notify administrators when an attack occurs. This can help companies reduce the cost and time of IT administrators in responding to web attacks. Nowadays, WAFs in the market are combining automation functions and machine learning technology to increase the security and easy management of the service.
– Easy set-up
Easy set-up of the service is important. Because if your IT administrator experiences difficulties in managing the service, it would be hard to achieve the expected effect of the service.In addition, areas that are difficult to solve must have immediate technical support. Giving pressure to your IT administrator won’t help your company. Before choosing which service to use it is best to research the provider, such as how many partners do they have, and if they respond immediately to your request.
2.Accurate detection capabilities
In the application layer, small packets of data are being delivered and the job of the firewall is to block abnormal packets/unauthorized access from entering.
The main purpose of the WAF is to protect the application layer from being attacked, but if your firewall can’t manage to do so, then it is best for you to look for another firewall that can actually do the job.
WAFs use different types of cyber attack detection methods, but most WAFs use the ‘pattern matching’ detection method in detecting cyber threats. Depending on the type of detection method your firewall uses it can affect the ability in detecting unauthorized access and blocking it from entering your network. But if your firewall blocks genuine users from entering (false positive) and gives access to not legitimate users (false negative) then that firewall is not doing its job and it will affect your business.
If your company wants to keep your network safe and not lose customers then it is important to lower the rate of both false positives and false negatives at the same time. To do so requires a WAF that uses a ‘flexible detection’ method that can respond and block new types of cyberattacks, rather than depending on pattern matching that base on the patterns of the past cyberattacks.
3.Fast detection rate
Fast detection of cyber threats is as important as detecting cyberattacks accurately. These days cyber attacks occur almost all the time; that is why the WAF you are planning on adopting should be able to detect all types of cyberattacks at all times.
Certainly, it is not easy to find a WAF that can satisfy all the needs of your company. However, having a WAF that can detect cyber threats fast and accurately is essential for a secure application environment.
Conclusion
In this blog, we discussed the importance of using a WAF (Web Application Firewall). If you are considering using one keep in mind the three checkpoints in finding a good WAF. Cloudbric provides an intelligent Web Application Firewall for all company sizes. Cloudbric has been protecting over 100,000 websites so far. Read more on how Cloudrbic’s WAF differs from other WAF providers.





