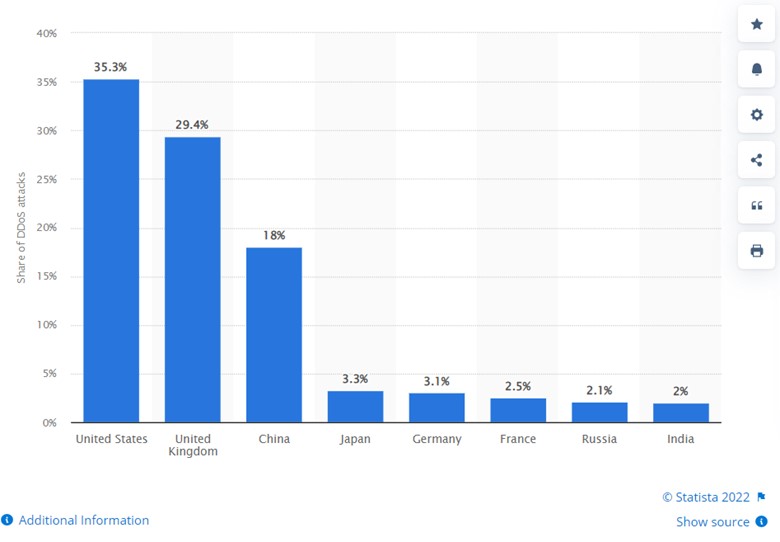
Over the past few years, the number of ransom attacks on internet users has increased substantially. The country that gets the most attacks is the United States, followed by UK and China:
So, with this growing threat in mind, what should you do to protect yourself?
We’ve compiled a few helpful tips and recommendations that will teach you how to handle a ransom DDoS attack and what to do in this situation.
What Is a Ransom DDoS Attack?
A ransom DDoS attack (also known as RDDoS) involves a malicious party trying to demand or extort money from the victim (an individual or an organization); if the victim doesn’t comply with their demands, they receive a threat in the form of a DDoS (distributed denial of service) attack.
So, basically, a person receives a note with a threat, which might also include an illustration of the consequences of a possible DDoS attack. Next, if the attacker decides to follow through with their threat, they send traffic targeting the victim’s online property, exhausting its resources. If the victim is unable to mitigate these consequences, the attacker proceeds with demanding the ransom.
Let us give you a real-life example to help you understand this process even better.
Let’s say you have a language learning app with millions of users. If it goes under the DDoS attack, which is often carried out by multiple people, it slows the app down due to the heavy traffic targeting it. As a result, your app’s performance drops significantly and goes to crash mode, which can even result in the loss of data of all your customers.
As you now understand the severity of ransom DDoS attacks, let’s take a look at how to prevent them.
1. Recognize the RDDoS Attack
First of all, you need to be 100% sure you’re dealing with a ransom attack. We already mentioned that you could receive a note with a threat. But what components does this note usually consist of?
It is often an email that contains the following:
- A mention of a previous DDoS attack (not necessarily on your organization but in general).
- A description of the weak spots in your website, application, or other product the attacker is threatening to hack.
- The attacker may specify the size of the attack, its duration, and the consequences.
- You may find that the attacker is affiliated with large hacker groups.
In the end, the people threatening you will give a deadline and a sum of money you need to pay to avoid the attack. Remember: never follow through with the attacker’s demands. It doesn’t guarantee safety.
Instead, give your team of developers a task to analyze your current traffic and possible vulnerable spots. You should have a clear idea of the traffic patterns and real-time solutions to a possible attack.
2. Create an Anti-RDDoS Plan
Once you have a clear understanding of the vulnerability points, you can create a plan that will help you resist this threat and all possible RDDoS attacks in the future. This plan should include the following measures:
- Improve network infrastructure. That involves optimizing network traffic, updating all hardware and software, using VPNs, etc.
- Check your website’s architecture. One of the key steps here is to go through the web pages that link to your website as well as the sites your website links to. Some of the traffic coming from suspicious web pages can harm your site’s performance.
- Consider incorporating best practices in web security. Do data validation, encrypt all your data, apply authentication, etc.
The key point here is to stick to this plan even if you don’t receive a ransom DDoS attack threat. If you keep up with these requirements, it will be easier for you to recognize if a threat is real or someone is simply trying to extort money for a made-up reason. Such a plan will also help you protect your website.
3. Consider Using a DDoS Attack Defense Service
As an extra layer of protection, you can purchase a DDoS Attack Defense Service. However, you need one that not only blocks threats on the transport and network level but also evolving DDoS attacks on the application layer.
The Cloudbric ADDoS solution can cover all your needs. The purpose of this product is to protect you at the human-computer interaction layer, where the probability of the HTTP flood (a process similar to refreshing a browser on many devices at once) is high. Having this solution will not only help you protect yourself from RDDoS attacks but also mitigate them in the future.
Over to You
Ransom DDoS attacks are getting more popular for several reasons. First of all, they are cheaper and less time-consuming to execute than installing malware on your devices. Besides, such attacks use common open-source web applications. So, unfortunately, their number will be increasing every year.
Hopefully, our short guide will help you protect your assets and decrease the possibility of RDDoS attacks. For more tips, please, check our website!
Check out Cloudbric’s product lines:
No.1 in the Asia Pacific – WAF with A.I & Logic-based detection engine: Cloudbric WAF+
Cloud-based DDoS attack defense service with edge computing: Cloudbric ADDoS
Zero Trust Network Access-based Remote Access Solution: Cloudbric RAS
Blockchain: Blockchain Security Solution
Click here for inquiries regarding the partner system





