Although the word “cloud” has been gaining popularity and trending in the IT community, the cloud industry has struggled for the last few months. This is because a fatal security flaw was discovered in the Content Delivery Network (CDN) of Cloudflare, an American security company founded in 2010. The CDN is responsible for moving content to a temporary storage server and delivering it to users when requested. In other words, it mediates the information of the website to deliver the content quickly and reliably to many visitors. In order to do this, the content passes through a “parsing” process using HTML parsing technology that efficiently processes web pages.
In Cloudflare CDN, a bug was found in which the server randomly returned incorrect information held in the memory during parsing, and a large amount of sensitive information–including personal information and authentication tokens–was leaked, causing widespread fear among knowledgeable consumers. This incident was called “Cloudbleed” by the IT community, naming it after the security flaw “Heartbleed”.
Heartbleed is a security flaw found in open SSL used to encrypt various information on the Internet. By incapacitating encrypted communications that are considered secure, information transmitted to servers, such as login information, personal information, and financial information, can all be extracted. It is found in the TLS heartbeat extension of OpenSSL and thus called Heartbleed.
Tavis Ormandy, who discovered Cloudbleed, listed leaked information he discovered, including hotel reservations, passwords, and chat messages. Companies that use Cloudflare have lost some of their traffic (HTTP cookies, IP, passwords, keys, etc.).
The Cloudbleed flaw was exacerbated by the fact that sensitive information was not only compromised, but also exposed to the search engine cache. Although major search engines helped to remove the exposed information from the cache, Cloudbleed was not found for several months, with the most damage being caused between February 13 to February 18, 2020.
Companies and individuals are making the decision to change their services to a service like Cloudbric. Cloudbric can be quickly instituted to rapidly solve emergencies such as the Cloudbleed incident.
For those who want to solve problems like Cloudbleed, here is a simple and easy way.
How to Change to Cloudbric WAF
Upon receiving an account from our team, go to the login and change your password by selecting 8 or more upper and lower case characters that include letters, numbers, and symbols. You can then view Cloudbric’s full-service website security console.
Step 1: Register an account and add your site
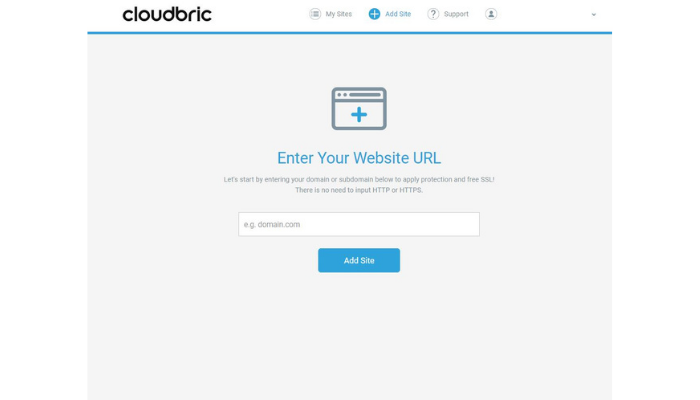 It’s very simple. Register your account by adding your email address, password, and your domain. A subdomain can be added when you register your main domain.
It’s very simple. Register your account by adding your email address, password, and your domain. A subdomain can be added when you register your main domain.
Step 2: Configure Settings
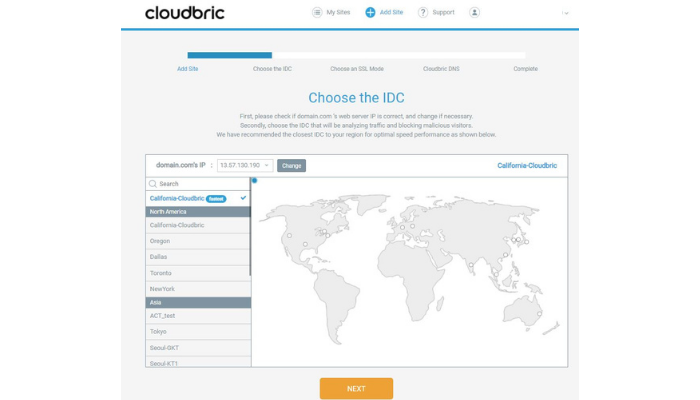 Cloudbric has Internet Data Centers (IDCs) worldwide; choose the nearest IDC and check the SSL status of your website. Cloudbric will then automatically and easily renew your SSL certificate for free.
Cloudbric has Internet Data Centers (IDCs) worldwide; choose the nearest IDC and check the SSL status of your website. Cloudbric will then automatically and easily renew your SSL certificate for free.
Step 3: Switch your DNS settings to Cloudbric
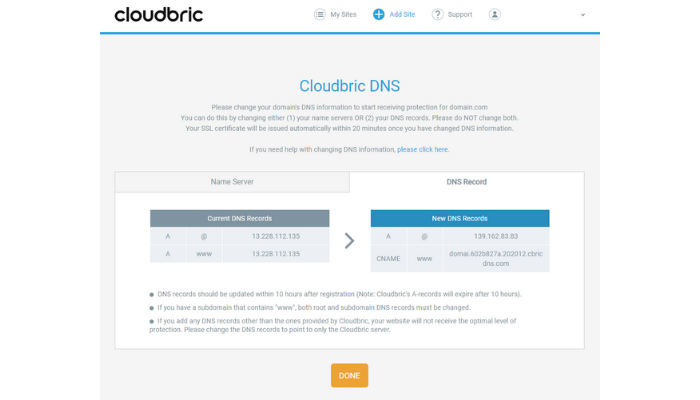 If your traffic passes through the Cloudbric network, Cloudbric will secure your site no matter what service you are currently using. These three steps are all you need to do. Cloudbric uses a proprietary logic-based analysis engine that does not need any ruleset updates. The web application firewall engine monitors your traffic and uses a defined algorithm to blocks threats via AI by learning what traffic is malicious. It results in extremely low false positive rates and increases security at a low price.Cloudbleed proved that even a small flaw is fatal to users and companies around the world as Cloudflare is used on more than 5 million websites. Put your website security first and keep updated on the most efficient security service that can be used on your site. Find out more about Cloudbric WAF.
If your traffic passes through the Cloudbric network, Cloudbric will secure your site no matter what service you are currently using. These three steps are all you need to do. Cloudbric uses a proprietary logic-based analysis engine that does not need any ruleset updates. The web application firewall engine monitors your traffic and uses a defined algorithm to blocks threats via AI by learning what traffic is malicious. It results in extremely low false positive rates and increases security at a low price.Cloudbleed proved that even a small flaw is fatal to users and companies around the world as Cloudflare is used on more than 5 million websites. Put your website security first and keep updated on the most efficient security service that can be used on your site. Find out more about Cloudbric WAF.





