BackgroundRansomware isn’t a new phenomenon. The concept of holding locked files for ransom has been around since the era of the floppy disks. However, many will be surprised to find out that ransomware comes in many forms. Ransomware typically comes in the variants of “locker” ransomware and “MBR” (Master Boot Record) ransomware. Locker ransomware makes a u ...
The Top 10 Hackers Arrested in 2017
Cyber criminals are rampant. Active on the dark web, hacking forums, or other platforms that facilitate illegal activities, hackers are utilizing their skills to run effective but illegal black markets. For example, DDoS-for-hire services are quite popular among cybercriminals with willing customers paying as low as $7 an hour to target a company of their choice. These days, cyber cr ...
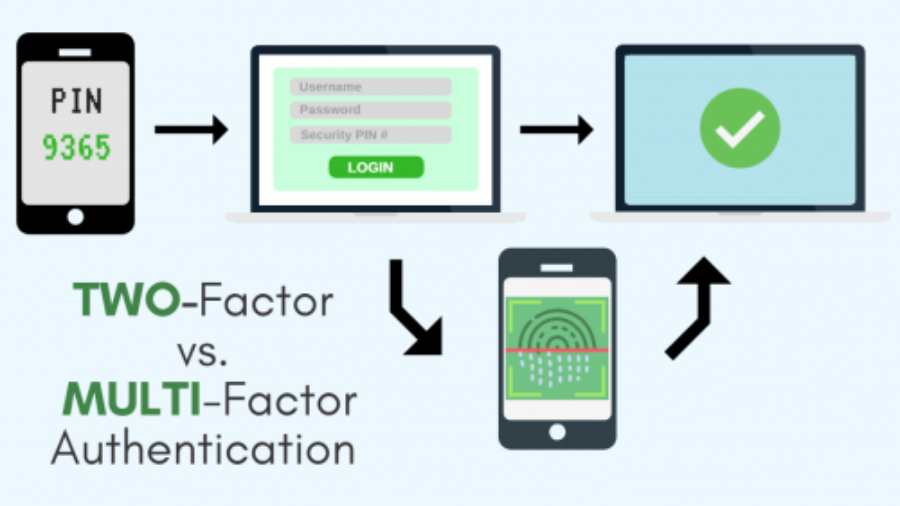
Two-Factor vs Multi-Factor Authentication
When the best online security practices are being discussed, there’s always someone that brings up either two-factor authentication (2FA) and multi-factor authentication (MFA). This is because more and more online services are recognizing the need to ensure a higher level of security for online accounts. Two-factor authentication and multi-factor authentication add additiona ...
The Anatomy of a Blended Attack
What is a blended attack?Depending on the context, a blended attack can refer to two different things. Generally speaking, a blended attack refers to the idea of using mixed techniques to invade one computer system to the next. Blended attacks, then, can include computer viruses, worms, and Trojan horses. They typically exploit an initial security flaw and move on to perform additional n ...