
Recently, As cyberattacks targeting vulnerabilities in web applications for companies have frequently occurred, the number of companies implementing a WAF as a countermeasure are increasing. There are various products on the market at present, but this time we will focus on four points to look at when choosing a WAF, as to what criteria should be selected.
A WAF is an abbreviation for Web Application Firewall, which is a security measure that protects websites from attacks that exploit vulnerabilities in web applications. It is installed in front of the webserver to analyze and inspect communications, protect the website, and prevent unauthorized login. Websites and services on the Internet are now important social infrastructures. The use of websites is steadily expanding, such as online shopping, online banking, the use of entertainment such as games and SNS, and business such as order management between companies. Along with this expansion of social infrastructure, websites have become the targets of cyber-attacks.
Source: JPCERT/CC
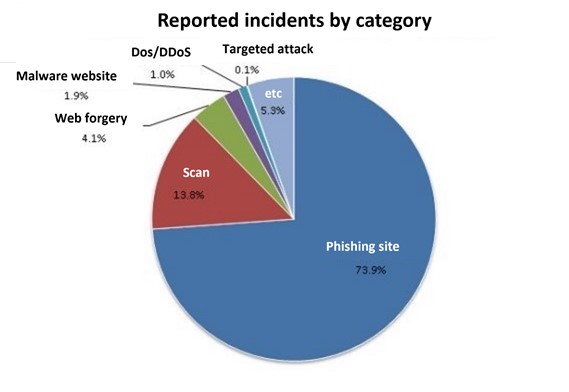
According to the latest incident response report (April 1, 2020-June 30, 2020) by JPCERT Coordination Center (JPCERT / CC) in a general corporation, 73.9% of incidents are classified as phishing sites, 13.8% of incidents to explore the weaknesses of the system are classified as scan, and incident caused by website modification accounts for 4.1%. There are 3,839 incidents of phishing sites which is the No.1 threats during this period. After embedding a malicious script in a trusted website using cross-site scripting (XSS) attacks, SQL injection, etc., It induces visitors to phishing sites to infect malicious code or leak secret and personal information. It is also possible to change the targeted website. If a company receives these attacks, the damage will be quite fatal, but a WAF can also be used to prevent such advanced cyber-attacks.
Four points that you can consider when choosing a WAF
-
Initial cost / operation cost
First, you need to consider the total cost, which is combining the initial cost and the operation cost. When it comes to installation costs, you need to be careful not to be overwhelmed by the initial cost of installation. Depending on the operating conditions, the operation cost or a case that you need to operate by your IT teams may be more expensive. Therefore, the total cost should be compared with the cost of installation and operation. For products that are supposed to be operated in-house, such as on-premises type and complicated products, there is also a cost of securing employee resources within the company. Cloud-based WAF doesn’t require dedicated hardware, therefore it is easy to install and requires less tasks of operation. Additionally, it would be better for you to apply a WAF that suits your environment considering whether the employee has operational skills.
-
Security quality
In order to select a WAF that suits your company, it is also important to be able to operate at the optimum security level. If the security level is low, there is no point in implementing it, and if it is too advanced, it may block normal access, and as a result, there is a risk of compromising the convenience of websites or applications. Furthermore, the higher the security strength, the higher the false-positive rate may be. Choose a product that is comprehensively superior in terms of detection rate, false-positive rate, and performance.
-
Support system
It goes without saying that it is a product equipped with an emergency support system. Advanced knowledge is required to operate the WAF properly. Additionally, due to the nature of security products, there are many occasions when you encounter unknown events. It is necessary to confirm in advance whether or not you will be able to receive solid support just in case.
-
Implementation performance
Products with abundant implementation records have accumulated know-how experience in responding to the latest security. It is considered that know-how and knowledge are sufficiently accumulated in proportion to records of performance. Being selected by many customers is also evidence that high-quality products and services can be provided in response to the security needs in various industries. High-performing products are one of the points to be checked because they can be considered reliable as security products.
Last but not least
FW (firewalls) or IPS (Intrusion Prevention System) is well known as a security measure to protect the website. Even if you have already implemented measures by FW or IPS, you cannot say that the measures are sufficient. FW is a security measure at the network level. Access is restricted depending on the source and destination information (IP address, port number, etc.). Communication aimed at services that do not require external disclosure such as port scans may be restricted, but the communication details are not scanned. It cannot handle attacks disguised as normal communication or communicating through port 80 and port 443. IPS is a security measure at the platform level. It inspects and defends against various types of attacks, such as attacks that exploit vulnerabilities in the OS and middleware, and attacks on file-sharing services. However, attacks on web applications are increasing in a wide variety of ways, and there are cases where advanced attacks such as those targeting application-specific vulnerabilities can’t be prevented. WAF is a security measure at the application level higher than FW and IPS and is a defense measure specialized for web applications. a WAF, FW, and IPS work at different network levels. The implementation of WAF does not mean that FW or IPS is unnecessary, but because the security level is vulnerable without any measures, it is necessary to supplement each measure. When choosing a WAF, make sure to select a product that excels in cost, security, support, and implementation results based on the points that are mentioned here.
Cloudbric with over 10,000 introduction results
Cloudbric provides a cloud-based WAF service that is equipped with a logic-based detection engine of a WAF “WAPPLES”, which has the largest market share in the Asia-Pacific market, and it can respond not only known attack patterns but also high-precision new types of attacks. We use our unique logic-based detection engine to ensure superiority in detection rate, false-positive rate, and performance. Its technical capabilities have been recognized by experts around the world and are supported by more than 700,000 sites.
In response to unknown and variants of attacks that cannot be detected by the conventional signature-based WAF, attacks are analyzed and detected by about 26 detection rules Cloudbric sets in advance if suspicious traffic is found. Since Cloudbric doesn’t use signature-based WAF, you can avoid threats occurring in frequent signature updates. It is highly secure and can be implemented at a reasonable price. Not only a WAF, DDoS measures, but also free SSL certificates are available without additional charges. You can also receive a reliable 24/7 monitoring system and generous support from the experts. Cloudbirc has already implemented more than 10,000 cases and has been highly evaluated in all aspects such as high-quality proprietary security, cost, support system.
Click here for inquiries about products and services
Click here for service experience
Click here to apply for a free trial
Click here for inquiries regarding the partner system





