Undoubtedly, remote learning has always been an alternative to face-to-face education. Teachers from any field would use cloud-based tools to encourage student’s collaboration. They would also grant access to academic resources and even provide support via teleconferencing.
But it was the COVID-19 lockdowns that made remote education a necessity. Now, many academic curricula are entirely virtual, and most will stay like that.
Educational institutions can utilize remote access solutions to allow students and faculty to securely access school computers remotely from home. They can also allow IT admin and support to manage resources remotely. And additionally, as a way to promote BYOD in classrooms to improve student’s engagement or also to allow faculty and student’s mobility.

Photo by Jordan Encarnacao on Unsplash
In this blog, we’ll discuss the top five Remote Access Solutions for Education. We’ll discuss VPNs, remote desktop software, the new software-defined perimeters, the 100% cloud networks, and the cloud-based channel with additional security. All these solutions work fine for remote access in education, but some are better than others for specific purposes.
Top 5 Remote Access Solutions for Education:
- School, College, and University-level VPNs.
- Remote Desktop Software.
- Software-Defined Perimeters.
- Cloud-Network Remote Access.
- Cloud-based Secure Channel.
1.School, College, and University-level VPNs
Although today VPNs are advertised as privacy tools, they were designed to extend private networks. If configured appropriately, VPNs are fantastic simple tools that provide remote safe access to school networks. VPNs use robust encryption mechanisms that allow a safe connection of remote clients (students) to their school servers. VPNs can create an encrypted tunnel between client and server via any network, including the public internet. Remote students with a VPN can access the school’s resources, including files, databases, specific servers, or the entire institution’s intranet.
VPN’s Drawbacks:
- VPNs leak data. VPNs are known to leak sensitive data due to misconfiguration. Although they use robust encryption mechanisms, a bad VPN implementation may lead to DNS, IPv6, or WebRTC data leak.
- Lack of granular authorization and authentication controls. It is impossible to grant different levels of access to other users. IT managers would need to install unique VPNs for different servers/users. Also, if a student’s PC is compromised, or the account rights are stolen, the entire network is at risk.
2.Remote Desktop Software
 Remote desktop is a popular access feature found in almost all operating systems and proprietary and open-source software. It allows anyone (across the room or the world) to access a desktop computer and gain total control through the established session.The most common remote desktop software is Microsoft’s RDP (Remote Desktop Protocol). But there are other popular tools, such as TeamViewer, AnyDesk, UltraVNC, and more.Remote desktop is among the favorite tools for remote administration. It is quick, easy to use, and allows a wide range of management tasks. Usually, remote desktop comes with features like screen sharing, file transfers, mobile connections, chat, etc.In remote education, entire remote classrooms can be set up, with screen sharing webinars, online conferences, collaboration, etc. When deciding between Enterprise Remote Desktop solutions vs VPNs consider the application and demand.
Remote desktop is a popular access feature found in almost all operating systems and proprietary and open-source software. It allows anyone (across the room or the world) to access a desktop computer and gain total control through the established session.The most common remote desktop software is Microsoft’s RDP (Remote Desktop Protocol). But there are other popular tools, such as TeamViewer, AnyDesk, UltraVNC, and more.Remote desktop is among the favorite tools for remote administration. It is quick, easy to use, and allows a wide range of management tasks. Usually, remote desktop comes with features like screen sharing, file transfers, mobile connections, chat, etc.In remote education, entire remote classrooms can be set up, with screen sharing webinars, online conferences, collaboration, etc. When deciding between Enterprise Remote Desktop solutions vs VPNs consider the application and demand.
Weaknesses of Remote Desktop:
- Remote desktops are single-point of failure systems. If a remote network or a single component in the remote desktop fails, the entire desktop remains inaccessible. VPN servers have an advantage here because they are made to grant access to a network, not a single system. Remote desktops don’t have tracking systems in place that could monitor their availability.
- Authentication Weaknesses. If the credentials fall into the wrong hands, the entire desktop and network may be compromised. For example, protocols such as RDP don’t use the MFA (Multi-Factor Authentication) method. If a hacker knows your email and gets a list of your network IP addresses, they can brute-force your AD (Active Directory) password. With MFA, even if a hacker has your credentials, they’ll not be able to log in.
- Remote desktop traffic has easier access and is not typically monitored. Remote desktop solutions grant remote access to user endpoints (sometimes privileged and sensitive servers) inside a network perimeter. To make this solution work, firewalls need to open their ports to remote desktop and accept their incoming traffic. Unfortunately, this traffic is not typically monitored.
3.Software-Defined Perimeters
Software-Defined Perimeters (SDP), as the name implies, refer to network boundaries based on software and fully independent from hardware. SDPs are also referred to as “Black Clouds” because they hide the internet-facing infrastructure. These black clouds are invisible to hackers or attacks. SDPs are designed to control access to resources based on Identity Access Management (IAM) and thus are only accessible by authorized users.SDPs build a virtual boundary at the network layer, which can be extended geographically. This virtual layer makes it possible for remote users and devices to authenticate based on identity. It grants access to a network only after users verify their identity and evaluate their device.
SDP Strengths:
SDPs are different from VPNs because 1) they do not share network connections (as VPNs do) and have a more granular level of access control. Additionally, SDPs are based on the zero-trust policy, making them highly efficient against common cyberattacks. Some Security-as-a-Service “SECaaS” might include SDP as part of their service offerings.
SDP Weaknesses:
- SDP communication depends on controllers. If an SDP controller goes offline, it will not be possible to establish communication with the remote resources.
- Device compatibility. If you are attempting to incorporate an old router or switch, it will likely not support SDP.
4.Cloud-Network Remote Access
 Although many educational institutions still have on-premises infrastructure, a big percentage is beginning to transition to full cloud-based networks and SaaS applications. On-premises infrastructure is getting thinner, and a big chunk of it is moving to the cloud. Cloud-network remote access is convenient. As long as teachers and students have access to the internet, they’ll connect to their cloud-based resources and SaaS applications like Office 365, Zoom, Google Apps, WebEx, etc. Bear in mind, that cloud computing is not a replacement for remote access technology. In fact, many educational institutions prefer (and are required) to keep data and infrastructure on-premises. Although cloud computing and remote access fall into different categories, they have something in common: they enable collaboration between users, which is critical in education.
Although many educational institutions still have on-premises infrastructure, a big percentage is beginning to transition to full cloud-based networks and SaaS applications. On-premises infrastructure is getting thinner, and a big chunk of it is moving to the cloud. Cloud-network remote access is convenient. As long as teachers and students have access to the internet, they’ll connect to their cloud-based resources and SaaS applications like Office 365, Zoom, Google Apps, WebEx, etc. Bear in mind, that cloud computing is not a replacement for remote access technology. In fact, many educational institutions prefer (and are required) to keep data and infrastructure on-premises. Although cloud computing and remote access fall into different categories, they have something in common: they enable collaboration between users, which is critical in education.
Some Advantages?
With cloud-based resources, education institutions don’t need in-house technicians to maintain and secure the infrastructure. All software, platforms, and infrastructure is hosted on the internet.Cloud-based networks are based on IAM or PAM (Privileged Access Management), so there is no need to use a VPN.
Disadvantages?
- Some data can’t be sent to the cloud. For specific industries, like education or health, some sensitive data must be kept on-premises due to regulations and compliance.
- Cloud lock-ins. Having all data and applications on the cloud makes institutions entirely dependent on the cloud.
- Moving data (especially big data) up and down the cloud introduces latency. Downloading and uploading large amounts of data will inevitably introduce latency into communications. Additionally, applications that require instant access to data will be dramatically impacted.
5.Cloud-based Secure Channel
A cloud-based secure channel is one of the most comprehensive and safest solutions for remote access. Having secure remote access is imperative for schools and educational institutions. Cloudbric’s remote access solution provides an encrypted channel from the remote user to the private network via the cloud. This remote access solution sounds just like what a VPN does. But instead, it takes the already encrypted traffic over its cloud-based, 3-layer security. It monitors traffic on the channel, authenticates users, and prevents hacking attempts.Remote access solutions, such as VPNs or Remote Desktop, require server/client deployments. With the server/client approach, it is challenging to track access to resources, and it is also a potential for connection errors. A cloud-based secure remote access channel, such as Cloudbric, does not need any hardware or software deployments on either client or server sides. Cloudbric uses the following 3-Layer security between the user and the private network: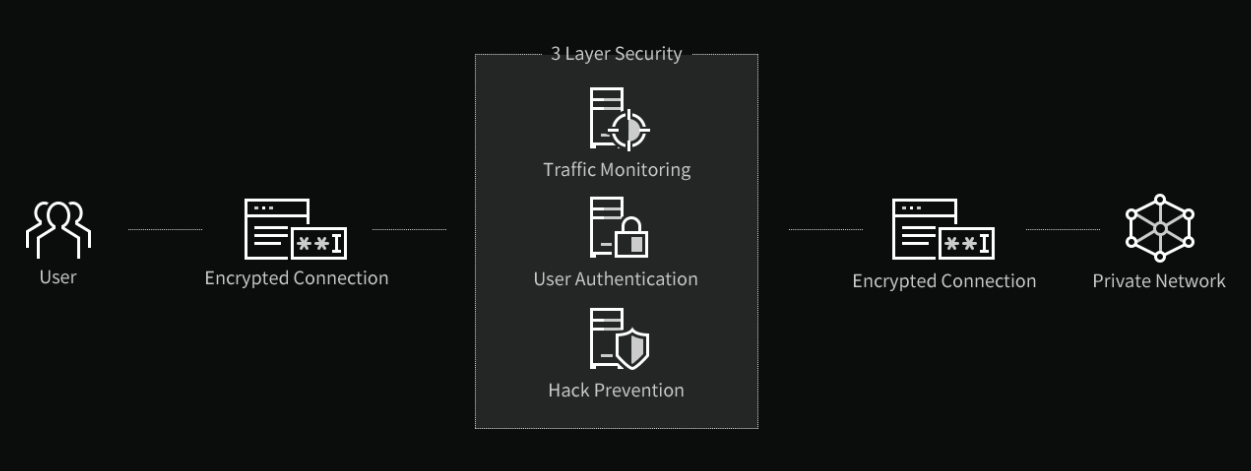
- 24/7 Traffic Monitoring: Keep track of traffic flows between source and destination. It detects and blocks common attacks, including cross-site scripting, injections, and even DDoS attacks.
- User Authentication: Uses a 2-Factor Authentication (2FA) to ensure only real users with valid credentials gain access into the private network.
- Hack Prevention: One of the most significant advantages of CloudBric’s remote access solution is that it can defend against hacking attempts. It blocks malicious traffic from bots or botnets and blocks out network scanning attempts.
Final Words
Pre-COVID-19, tele-education, and e-learning were only trends, but now they are the new norm. Their demands are too high to ignore. Now, classrooms are becoming remote and virtual. So students and teachers need instant collaboration and access to online resources in a timely and secure manner. A cloud-based secure channel such as Cloudbric leverages the cloud to do what it does best. With this approach, the cloud runs intensive security workloads on the remote access traffic. It then monitors traffic, detects and prevents hackers, and blocks unauthorized users. Try Cloudbric’s Remote Access Solution for free for a limited time, and improve your remote learning and teaching.





