“Automation might be a good thing, but don’t forget that it began with Frankenstein.” — Anonymous.
Frankenstein monster’s intelligence came from a mad scientist. The monster only knew how to carry out instructive and repetitive tasks. Whether they were wrong or right decisions? That was outside the artificial mind of the poor monster.
The same goes for today’s Artificial Intelligence (AI), which is just a tool created and used by humans. You can create self-autonomous cars, recognize criminals’ faces in crowded places, or create an intelligent army of bots to attack the Internet.

Imagine, what kind of monster would Victor Von Frankenstein have created if he had access to AI?
Well, now that there is AI, there is a new kind of monster being created by Cybercriminals. They are integrating AI into their already scary arsenal of tools. AI makes their attacks sharper, faster, and more destructive.
1. From human-based DoS to automated machine-based DDoS attacks.
Like a wrecking ball— demolishing entire well-structured buildings, DDoS comes with enough power to break down most of the well-established sites and services on the Internet. Early Denial of Service (DoS) attacks started to be effective when attackers (or DDoSers) adopted process-driven approaches like scripting and automation. Now, processes are slowly evolving to data-driven systems, like AI and ML (machine learning). An AI-based DDoS code can solve problems, make quick judgments, and even predict the defensive strategy.
The Evolution:
How did DDoS come to be so destructive and powerful?
- The Traditional (single-point of entry) DoS Attack: DoS tools began as simple scripts that gave an attacker easier access to modify HTTP, TCP, and UDP packets with different sizes, timeouts, and rates. But this approach needed human intervention 24×7; someone to “think” about how to affect the target and configure the packets that would hurt the most.
- The First Signs of Automation: To introduce the process of repetition in those single statements or blocks within the DoS scripts, the DoS code developers compiled these scripts with feedback loops. This automated process helped attackers remove themselves from the equation. But still, one source could be easily identified.
- Introduction to Multi-vector Attacks: DoS attackers brought distribution concepts to enlarge and empower the attack surface. DDoSers started to recruit bots to launch more powerful and undetectable attacks. Here’s where the name changed to Distributed DoS.
- Automated Scanning and Delivery: Recruiting new bots wasn’t easy. DDoSers started using many ungracious ways to enlarge their army. They automatically scanned thousands of networks to find unpatched and vulnerable systems to spread DoS scripts (malware) into soon-to-be bot clients. DDoSers would install “intelligent” malware like worms, which are capable of self-spreading, or trojans with executable scripts that would hide bot clients.
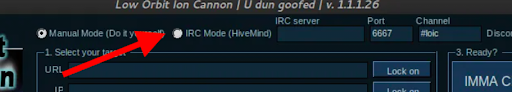
- Centralizing Command: Larger attack surfaces are difficult to manage, so attackers use the command and control center— which is a kind of proxy or controller that stores instructions for the bots. This place also provides an extra layer of anonymity for the attacker. All the bot clients automatically open an IRC botnet, IM, RSS control (via Twitter), or HTTP session with the command center. IRC communications are commonly preferred because they can be easily automated.
Below is a screenshot of LOIC (DDoS tool) which comes with an IRC-based “Hive Mind” mode that makes the LOIC (DoS client) connect to the LOIC IRC channel. This mode is used to “automatically” control bots via their IRC channel. And obviously, it also makes the client a bot (via Trojan) to participate in attack of larger targets.
2. AI Pushes More Persistence and Control to the Bots.
“To know your enemy, you must become your enemy.” — Sun Tzu.A DDoS attacker still has a pain point: mitigation strategies. The attacker might spend hours gathering intelligence and scanning the target. If they are not successful, they are likely to think about how and when to change the attack to bypass the mitigation strategy. A DDoS attack by itself is already scary as it is. But when you add AI into the equation, things can go wrong. A fully AI-based DDoS attack removes the human DDoSer from the equation, which isn’t good for many reasons:
- It makes the source of the attack difficult to trace.
- Available 24×7. The machine does not get tired.
- The error rate is non-existent.
- Fast and efficient decision-making.
- It helps the attacker make more automation (repetitive tasks).
- Predict outcome (predict defensive strategy).
The AI-based DDoS Attack: How Does It Look From the Other Side?
Generally, AI is composed of three main elements: Data > AI algorithm > Outcome. AI and ML models need as much data as possible to work. So at the beginning phase, attackers try to gather as much data (or input from their expertise) from failed attempts, scans, recon, etc. With data, attackers can start teaching their machine via supervised or unsupervised ML. Then, they build the AI/ML model, which replicates the decision-making process and enables a high degree of automation. 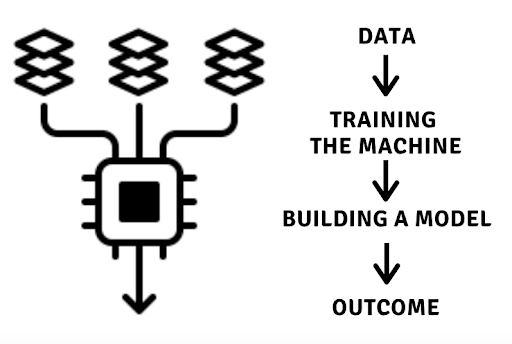 It is the DDoS’s command/control center that will run these models. The human-attacker might only need to step in (via encryption mechanisms) to set instructions. But the model is the one performing tireless decisions to automatically control bots and adapt their attack strategies. AI-based DDoS attacks are capable of automatically adapting their attack strategy based on the defensive side’s response. If an attack does not work, the system automatically changes to a new attack signature. For example, if a DDoS attack at the transport layer (TCP, UDP) is easily stopped by the target, the controller would make the botnet change to an application-layer attack.
It is the DDoS’s command/control center that will run these models. The human-attacker might only need to step in (via encryption mechanisms) to set instructions. But the model is the one performing tireless decisions to automatically control bots and adapt their attack strategies. AI-based DDoS attacks are capable of automatically adapting their attack strategy based on the defensive side’s response. If an attack does not work, the system automatically changes to a new attack signature. For example, if a DDoS attack at the transport layer (TCP, UDP) is easily stopped by the target, the controller would make the botnet change to an application-layer attack.
3. The Friendly Force has Better Tech!
“Every battle is won before it is fought.” — Sun TzuBy itself, an efficient DDoS attack needs resources. Plus, putting DDoS to work with AI is something that not anybody can do in terms of money, time, and expertise. If there is a sophisticated attacker with access to good state-of-the-art AI weapons, then the best mitigation strategy is to:
- First, protect your data (even publicly available data). Set rigorous data protection policies and train employees.
- Set HTTP and web monitoring and filtering systems.
- Fight AI with AI. Cloudbric’s WAF includes AI capabilities that allow the well-established filtering system to make more intelligent blocking decisions.
The source of data is key. Defensive machines can be trained with data obtained from cybersecurity expertise, updated libraries from open or closed sources, and even ML-powered automated tasks may also be used to learn the newest threat data.Massive access to the right data will ultimately help identify attack signatures faster and with more accuracy. Additionally, the newest Web Application Firewalls (WAFs) are integrating application learning/behavioral analysis methods, signature-free methods, and of course, AI.
How can advanced AI stop AI-DDoS attacks?
Artificial intelligence can:
- Classify data sources more accurately.
- Identify between legitimate vs. illegitimate threats. Keep false positives and negatives to a minimum.
- Use AI/ML models to help identify and stop the oldest and newest DDoS attack signatures.
- Use ML to build predictive models to discover unknown attack patterns.
- Integrate with the newest cloud WAF technology to include an automated calculation of the probability based on the user/application behavior.
- Integrate with AI-based WAF helps identify randomized DDoS attack signatures.