 DDoS attacks are evolving. Their level of sophistication and massive scale has become too complex to imagine.
DDoS attacks are evolving. Their level of sophistication and massive scale has become too complex to imagine.
What started with a couple of hundred Mbps scaled to Gbps. Now, volumetric attacks are reaching a whole new level as DDoS attackers or DDoSers continue to flood networks and break services with Tbsp-size traffic.
How are These Massive DDoS Attacks Possible?
Today there are larger botnets and easier accessibility to DDoS. The latter rise of DDoS attacks is correlated to the increase of unsecured IoT devices and the availability of DDoS-as-a-Service, Stresser tools, or Botnet-for-hire. One of the best examples is the Mirai Botnet. Vulnerable IoT devices such as printers, IP cameras, and home routers, transformed into bots ready to be commanded. According to a journal published in Hindawi, the Mirai Botnet can be used to perform a wide range of attacks, from the basic TCP SYN Floods to sophisticated DNS Water Torture.However, recruiting bots for a Botnet does not always require malware. By simply exploiting vulnerabilities found in certain protocols, DDoSers can bring down services. A clear example is the popular reflection and amplification attacks. Vulnerabilities found in UDP Portmap, DCCP, DNS, SNMP, NTP, and others can be used to amplify requests to 10X or even 100X and perform a powerful DDoS.
The Most Notorious DDoS Attacks in History
DDoS attacks can be measured in volume based on the number of packets per second (i.e., Million PPS) or bits per second (Gbps to Tbps), coming in.Clearly, size matters, as not everyone is ready and able to mitigate a one Tbps DDoS attack. Still, the “how” also matters. A series of smaller DDoS attacks with strong motivation and sophistication can be detrimental factors as well.
Timeline of the Most Notorious DDoS Attacks:
- February 2000 – The MafiaBoy DDoS Attack
- April 2007 – The Estonia Attack
- September 2012 – The Six Banks DDoS Attacks
- March 2013 – The Spamhaus Attack
- February 2014 – The Cloudflare Reflection Attack
- March 2015 – The GitHub Attack
- September 2016 – Krebs and OVH DDoS Attacks
- October 2016 – The Dyn DDoS Attacks.
- 2017 – The Google Amplification DDoS Attack
- February 2018 – The GitHub DDoS Attack
- February 2020 – AWS DDoS Attack
- Other DDoS attacks worth mentioning
February 2000 – The MafiaBoy DDoS Attack
In 2000, a 15-year-old known as the “MafiaBoy” brought down some of the world’s largest websites at that time, including Amazon, CNN, Dell, eBay, E-Trade, and Yahoo!. The DDoS attack not only led to customers being unable to access these sites but also to negative consequences on the stock market. The MafiaBoy DDoS attack caused an estimated $1.2 billion in damage.According to Wired Magazine, MafiaBoy implemented the DDoS attack by compromising various university servers to wreak havoc. He created and gained control of a botnet and flooded those websites with an overwhelming amount of traffic. MafiaBoy was later found to be a high-school boy named Michael Calce, who’s now a white hat hacker.
April 2007 – The Estonia Attack
The Estonian DDoS attacks began on April 27, 2007. It targeted a series of Estonian websites, including the parliament, ministries, banks, newspapers, and financial institutions. The attacks ranged from single individuals performing ping floods to botnets, which were used for spamming at that time. Today the Estonian DDoS Attack is studied by countries as one of the first-ever and largest instances of cyber-warfare. Experts say that the DDoS attack came as a response to a political conflict with Russia. This attack led to the creation of NATO’s Cooperative Cyber Defence Centre of Excellence in Tallinn, Estonia.
September 2012 – The Six Banks DDoS Attacks
In September 2012, many frustrated customers from six major US banks were unable to access their accounts and pay bills online. Banks, including Bank of America, JPMorgan Chase, Citigroup, U.S. Bank, Wells Fargo, and PNC, were the target of a series of +200 DDoS attacks. A hacktivist group, calling themselves Izz ad-Din al-Qassam Cyber Fighters, took credit and threatened to keep DDoSing if an anti-Islamic video wasn’t removed from YouTube. Although the banks had cybersecurity systems in place, none of them were ready to receive such an unprecedented amount of traffic. According to an FBI report, the source came from a botnet called Brobot with hundreds of hijacked web servers with vulnerable content management systems. The DDoS attack generated close to 60 Gbps of traffic.
March 2013 – The Spamhaus Attack
Spamhaus, a non-profit anti-spam organization, is responsible for directly (or indirectly) filtering a large percentage of daily spam email messages. Although they had been already threatened and DDoSed before and had some DDoS protection services in place, the 2013 DDoS DNS reflection attack brought down their website and a portion of their email services. The DDoS attack used 30,956 Open DNS resolvers that generated an estimated 300 Gbps traffic. The attack was traced back to Cyberbunker, an employee of a Dutch company, which was blacklisted for spamming by Spamhaus. Cyberbunker orchestrated and performed the DDoS attack for about two weeks.
February 2014 – The Cloudflare Reflection Attack
In February 2014, Cloudflare received a massive DDoS attack aimed at one of its customers. Attackers exploited a newfound NTP Servers’ vulnerability. Even though the attack was directed at a Cloudflare customer, it indirectly impacted the entire network and congested the Internet in Europe. Matthew Prince, CEO and founder of Cloudflare, wrote about the attack on Twitter:
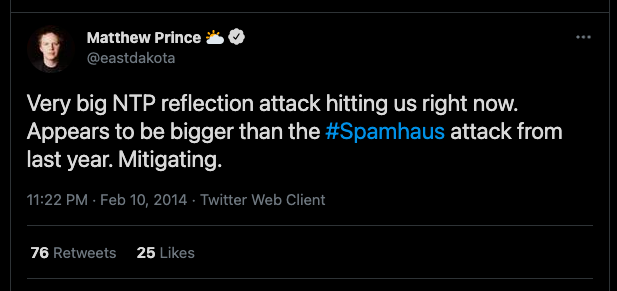 How did it happen?
How did it happen?
Attackers used the Network Time Protocol (NTP) DDoS amplification attack. First, they scanned and found NTP servers with amplification potential. The NTP servers with the MONLIST command were highly vulnerable. Consequently, the attackers crafted UDP packets, by spoofing the source address (in this case to CloudFlare’s customer) and setting the destination of the vulnerable NTP servers. The UDP response was amplified by NTP (MONLIST) and reflected to Cloudflare. The attack was estimated at 400Gbps of traffic.
March 2015 – The GitHub Attack
In March 2015, GitHub suffered the most sophisticated and largest DDoS attack in the site’s history. The DDoS attack targeted the URLs of two GitHub projects that were helping Chinese citizens circumvent China’s state censorship. It is believed that the purpose of this attack was to push GitHub into closing down these two projects. The DDoS attack vector evolved gradually, during the six days of the attack.
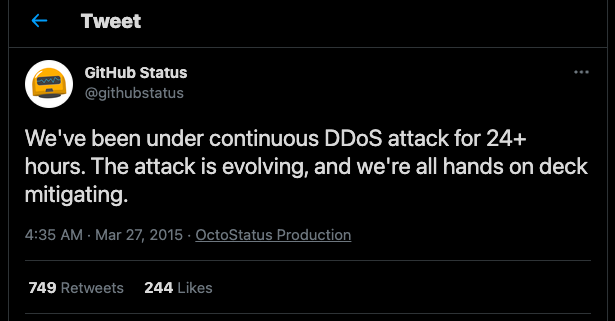 How did it happen?
How did it happen?
A large percentage of Chinese websites use Baidu Analytics to keep track of their visitors. When a visitor views one of these sites, the browser normally loads a JavaScript file to keep track of each user. It is believed that the attackers gained access to a highly authoritative data center. Additionally, all the traffic to Baidu Analytics is unencrypted. Thus, the attackers leveraged these weaknesses. They were able to replace the “normal” JavaScript file with another “obfuscated” file— one which instructed the user’s browser to continuously reload those two specific GitHub HTTP requests. When thousands of users were opening Chinese sites, they were unwillingly participating in the attack. A rogue JavaScript was injected into their client.
September 2016 – Krebs and OVH DDoS Attacks
On September 16, 2016, the cybersecurity blog KrebsOnSecurity was taken down by the largest volumetric DDoS attack at that time. The excess traffic was measured to be 620 Gbps. The source of this attack came from the Mirai botnet, which at that time consisted of roughly 600,000 compromised IoT devices. Before the Krebs DDoS Attack, Mirai Botnet was already popular, but when it hit the Krebs website, it became a major concern. A few days later, on September 19, the Mirai botnet attacked OVH, a large European hosting provider. According to the OVH founder, Octave Klaba, the OVH server received one Tbps DDoS attack— the largest at that time. Klaba stated publicly over Twitter that their servers received multiple DDoS attacks exceeding 100 Gbps simultaneously, adding up to one Tbps DDoS attack.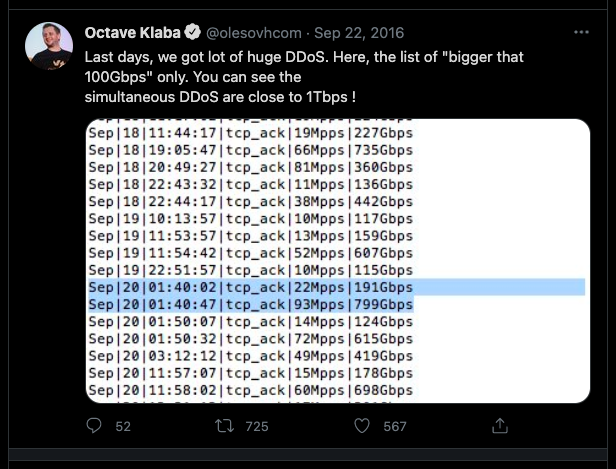 The most critical single attack documented by OVH, according to the same source, reached 93 MPPS and 799 Gbps. It came from an estimated 145,600 Mirai-infected bots, where each could send from 1-30 Mbps per IP. The Mirai DDoS attack against OVH lasted about seven days.
The most critical single attack documented by OVH, according to the same source, reached 93 MPPS and 799 Gbps. It came from an estimated 145,600 Mirai-infected bots, where each could send from 1-30 Mbps per IP. The Mirai DDoS attack against OVH lasted about seven days.
October 2016 – The Dyn DDoS Attacks
In October 2016, a series of massive DDoS attacks targeted DNS provider Dyn. The attack affected major Internet services. Users had difficulty accessing high-profile sites like Airbnb, Twitter, Visa, PayPal, CNN, BBC, and Netflix.
How did the Dyn DDoS attack happen?
Similar to Krebs and OVH, the source of this attack came from the Mirai Botnet. At that time though, the Botnet had grown to tens of millions of Mirai-infected IoT devices. The bots started to send malicious requests towards Dyn’s servers. The Dyn DDoS attack consisted mainly of TCP SYN floods towards port 53 of Dyn’s servers. The size of the DDoS attack against Dyn ranged between 1Tbps and up to 1.2Tbps, With the attack leaving a huge portion of North America and some parts of Europe without Internet. 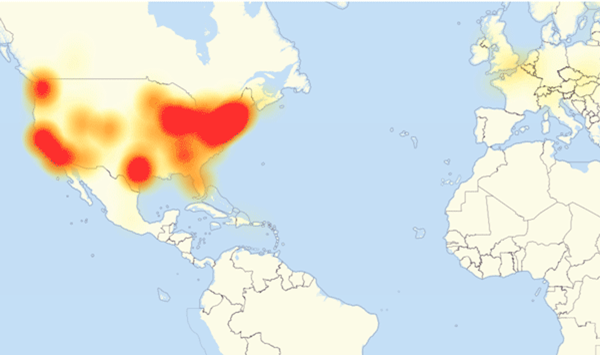
Image Source: DownDetector Level 3 Outage Map – CC BY-SA 4.0
2017 – The Google Amplification DDoS Attack
Although people thought that the Mirai botnet attacks could never be surpassed, a year later Google received a 4x larger DDoS attack. According to a 2020’s blog post from Google’s Threat Analysis Group (TAG), back in 2017 they measured a record-breaking UDP amplification attack coming from several Chinese ISPs. The attack targeted thousands of Google’s IP’s with various techniques, with the assault on their systems lasting about six months. The Google DDos Attack is probably not the most famous, but it is the largest. This attack was never made public until 2020. Up until this year (2021), TAG still calls it the largest DDoS attack ever reported in history.
How did it happen?
The DDoS attack peaked to a scary 2.5 Tbps. According to Damian Menscher, a Google Engineer: “The attacker used several networks to spoof 167 Mpps (Million of packets per second) to a combination of 180,000 exposed CLDAP, DNS, and SMTP servers, which would then send large responses to us.”
February 2018 – The GitHub DDoS Attack
GitHub was the target of a large volumetric attack in February 2018. The DDoS attack sent packets at a rate of 126.9 Mpps and reached 1.35 Tbps. According to GitHub, “the traffic was traced back to over a thousand different autonomous systems across tens of thousands of unique endpoints.” Fortunately, GitHub already had anti-DDoS systems in place, so they were able to detect the attack within 10 minutes and mitigate in 20.
How did it happen?
The 2018 Github attack is known as a Memcached DDoS attack. The attackers exploited a vulnerability on a command from the database caching system known as Memcached. The attackers spoofed the source within UDP packets to the GitHub servers and set the destination to vulnerable Memcached servers. The attackers were able to amplify the response size to more than 50,000x. 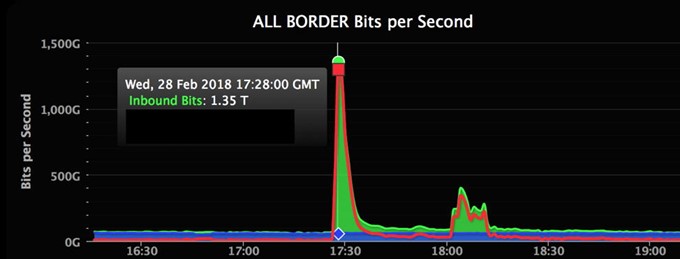
The February 2018 DDoS attack on GitHub. Source: Wired
February 2020 – AWS DDoS Attack
In February 2020, AWS reported mitigating a massive DDoS attack targeted at an undisclosed AWS customer. The attack lasted for three days and peaked at 2.3 Tbps. The AWS DDoS attack was quickly mitigated and didn’t do much damage. Still, that magnitude of traffic targeting a customer of the largest cloud computing provider, made cybersecurity experts jump from their seats.
How did it happen?
The attacker used a Connectionless Lightweight Directory Access Protocol (CLDAP) Reflection DDoS attack. CLDAP is based on UDP, which is an older alternative to TCP-based LDAP. The attackers scanned for and identified a large number of vulnerable third-party CLDAP servers. These servers have the capability of responding to requests with an amplification factor of 56x to 70x of the original CLDAP request.
Other DDoS Attacks Worth Mentioning
- The 2014 Occupy Central, Hong Kong DDoS Attack. This DDoS attack brought down Hong Kong’s pro-democracy websites, including Occupy Central, PopVote, and AppleDaily. The attack targeted DNS infrastructure and resulted in peaks of 500 Gbps.
- The 2015 BBC DDoS Attack. It was a 600-Gbps DDoS attack that took down BBC’s websites and services for about three hours. The tool used for this attack— the BangStresser, was using AWS’s resources to launch the attack.
- The 2017 Czech Republic’s Parliamentary Elections DDoS Attack. The Czech statistical office website was the target of a DDoS attack during the vote counts. Attacks like this one can have negative consequences on democratic processes.
- The 2018 NetScout DDoS Attack. NetScout reported that one of their customers was targeted with a 1.7 Tbps Memcached amplification DDoS attack. This attack is extremely similar to 2018’s GitHub Memcached DDoS attack, but done on a larger scale.
- The 2019 Imperva DDoS Attack. In January 2019, Imperva reported an SYN DDoS attack targeted at one of its customers. It resulted in 580 million PPS (ranging from 800-900 bytes), considered to that date the largest by packet volume.
- The March 2021 DDoS Extortion to a Gambling Company. The most recent significant DDoS attack targeted a European gambling company in March 2021. The attacker used the Datagram Congestion Control Protocol (DCCP) or protocol 33, to launch the DDoS attack. The DDoS attackers abused DCCP-Request packets to perform an SYN Flood DDoS attack. The attack peaked at more than 800Gbps.
Final Words
Do not be the next victim on this list. It is challenging to stop an ongoing DDoS attack with protection. Imagine how virtually impossible it is to put to an end without any security in place. Start your DDoS mitigation plan today!To learn more about how Cloudbric can help against DDoS attacks, contact the Cloudbric team or read this.





