Due to the current pandemic situation, it seems like working remotely will prevail. Remote work has a range of benefits for both employers and employees.
For some employees, it renews their passion for work and makes them more productive (at least, 77% of employees believe so), as they are more inspired by their surroundings and the absence of traffic jams.
Employers obviously benefit from increased productivity. But what about security?
Regardless of a pandemic is there is connectivity, privacy, and management from non-corporate devices to worry about. If you do not have MDM (Mobile Device Management) or BYOD (Bring-Your-Own-Device) policy solutions yet or do not know what these words mean, this guide is for you in starting to look at endpoint security.
You might stop wasting the opportunities that working remotely brings and be confident about the security of your employees’ devices at the same time. It will take at least three steps which we are going to discuss in this article.
Conduct A Security Risk Assessment in The Context of Mobile Devices
Mobile devices become a real threat when it comes to the company’s sensitive data. With BYOD policy, people tend to neglect the fact that it’s not just their data on the mobile device but the company’s as well. So they might download the app that asks for specific data but an employee will never know because they do not bother to read all the requirements.Data can be hacked through user error, malicious intent, phishing attempts, social hacking, public Wi-Fi, outdated devices, and so on.The IT department is usually responsible for a security risk assessment. While conducting it, they go through three stages:
- finding out which data is really important for every team and what data must be protected
- what are the sources of danger, how likely they are to attack the mobile devices, and how often they might do so
- what is the best way to eliminate the risk: anti-malware services, best VPN, education for employees on data safety, etc.
Security risk assessment is widely used to decide on whether it is really safe to start using MDM. If the IT department claims that they will not be able to secure your data properly, then it is best to stop there and not do any further steps.
Implement BYOD and Remote Access Policies
As we have already discussed, employees who use their own devices might be a problem for data security. In order to define the process of using non-corporate devices, BYOD and remote access policies are developed by IT departments. Bring Your Own Device is an obvious trend in the corporate world that allows employees to use their own devices that they are accustomed to using. Employers do not have to provide everyone with corporate devices which drops the costs of the office. However, it is a pain for the IT department. BYOD requires a document that educates employees on how they should use their devices so that sensitive data will not be leaked. BYOD policies include:
- what devices are allowed to use and which ones are not
- security and data ownership policies
- available IT support
Remote access policy defines the methods that can be used to gain access to the internal network. It also outlines employees who can get access to it and the situations when third parties may get into the internal network.Both of these policies are necessary in order to ensure safe usage of the internal network. It has the purpose of educating the employees on possible threats and giving strict guidelines on establishing secure connections.
Launch Enterprise MDM Platform
Mobile Device Management is used by IT administrators to manage, protect, and strengthen policies on mobile devices. Overall, it ensures the safety of the company data along with BYOD and remote access policies. It is not only used within remote workers but within employees who work in an office but use their personal devices. MDM allows organizations to control employee smartphones, tablets, etc. It can track the location of the device, the applications that are being installed, enforce data encryption and passwords. However, users are often concerned about the IT department watching them all the time. Some modern MDM systems enable app wrapping, separate personal and company data, and give IT admins control over the company data only. These features might help your workers to be more confident while using BYOD and working remotely. 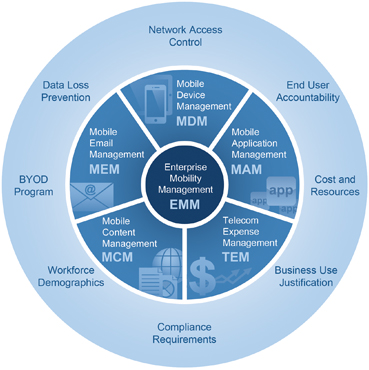
Source: notifycorp.com
Conclusion
With endpoint security, organizations must keep tabs on all the devices connecting to corporate networks. New connections mean new threat risks that must not be overlooked. Mobile devices in the workplace are becoming the norm, and therefore we must adapt to the changing times and assess the new threats that come with it. Follow these three easy steps is a great start to keep your remote workers’ devices will be safer than ever. Do you have employees working remotely? Make sure they are accessing files and apps securely! Learn more about our Remote Access Solution.






