When we call somebody a 'professional', we mean he or she is competent or skilled in a particular ac ...
3 Solid Startups You Need To Watch
According to Fortune Magazine, many startups fail because they run out of money or they lack experie ...
Buffer Overflow, a Common Attack Mechanism
Data can exceed a buffer's capacity Not many people may know or have heard about buffer overflow ...
Reflection Attacks and Amplification Attacks
Here are two types of attacks that are intended to monopolize your system's resources. Reflection A ...
What Are Application Level Attacks?
An application-layer attack targets the layer of the internet that essentially faces the end user. T ...
Attack Agents and Bots
Zombie cartoon So, we gave you guys a pretty good overview about DDoS attacks and how they are c ...
Types of Attacks – DDoS Part 2
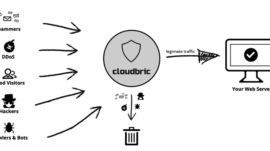
Cloudbric provides comprehensive web security Today, we will continue our discussion based on th ...
Types of Attacks – DDoS Part 1
Hackers can take over the world OK, so we now live in a world where even a 7-year-old can break ...
How Safe is Your Website? – Part 2
Login credentials for computers In this second part of "How Safe Is Your Website?", we wanted to a ...
How Safe is Your Website? – Part 1
When it comes to web security, people really have no idea how vulnerable their websites can be. ...