3 Core Principles of Zero Trust;
Enhanced Authentication, Micro segmentation, and Software Defined Perimeter(SDP)

On July 9th, 2023, the Ministry of Science and ICT of South Korea unveiled “Zero Trust Guidelines 1.0” to strengthen security in domestic companies and institutions. These guidelines aim to enhance security measures, minimize trial and error, and facilitate the adoption of Zero Trust.
Learn more about “Zero Trust Guidelines 1.0” 👉 ZERO TRUST vs ZTNA vs SDP
The guideline offers a comprehensive framework that covers the basic concept, security fundamentals, reference models of zero trust, and detailed procedures for planning and implementing Zero Trust deployments. Moreover, it emphasizes core principles of Zero Trust, such as enhanced authentication, microsegmentation, and Software Defined Perimeter (SDP) for the local environment.
Enhanced Authentication
Zero Trust strongly emphasizes the implementation of robust authentication policies and advanced authentication technologies for users and devices to secure enterprise system access. Its primary goal is to shield users from sophisticated online attacks by introducing Multi-Factor Authentication (MFA) which is a robust security measure again various attacks, especially phishing.
The commonly used ID and password-based authentication can be vulnerable to security breaches due to its low level of protection and the potential use of compromised passwords. However, these weaknesses can be effectively addressed by implementing multiple authentication methods, such as email-based authentication codes or One-Time Password (OTP) codes
Micro Segmentation

Granting uniform access to all data carries substantial risks. To effectively avoid these risks, it is crucial to adopt a differentiated and granular access management system for authenticated users, based on their specific ranks and permission levels.
In legacy-based on-premises environments like Unix and Windows, as well as in cloud-based corporate server systems, it is crucial to exercise caution regarding lateral movements. Lateral movement refers to unauthorized attacks that infiltrate the internal network and subsequently attempt to access and steal other data.
To safeguard against lateral movement attacks, organizations should implement micro segmentation configurations, providing granular access to key server systems based on their security levels. This proactive measure significantly mitigates potential hacking damage and enhances overall cybersecurity.
Software Defined Perimeter (SDP)
Software Defined Perimeter (SDP) is a fundamental technology for implementing Zero Trust Network Access (ZTNA), offering a network solution designed around user identity, and enabling micro segmentation.SDP is composed of agents, controllers, and gateways. It protects sensitive information resources by concealing them with gateways, and verifies user identity, and controls resource access with a controller.When a user who installed an agent accesses the corporate system, the security policy configures a dynamic network to grant resource access only to trusted users and devices. This ensures that authenticated users and devices can access applications through dedicated data communication tunnels that are not exposed to the outside, effectively securing enterprise resources.
These are the five key security elements of SDP.
✅ Hide the protected assets.
✅ Defend each other in both directions.
✅ Process only what is approved in advance.
✅ Apply access rules in real time.
✅ Extend access control to the application layer.
Then, which security technologies are required to implement the core security elements of SDP?
3 Core Technologies of SDP
 ① Single Packet Authorization (SPA)
① Single Packet Authorization (SPA)
Single Packet Authorization (SPA) is one of the fundamental technologies of SDP, an authentication protocol that leverages encrypted data for secure communications. Every communication between the agent, gateway, and controller(components of SDP) is authenticated with SPA, the method of delivering encryption key and encrypted information.
A single packet is sent from the client to the gateway, which awaits its reception. The gateway then decrypts the encrypted packet and proceeds to validate its contents. Upon successful validation, the gateway responds by sending back a response packet that grants access to the user. Additionally, the gateway adds rules to the firewall to establish mutual TLS (mTLS) for the requested service.
Through this process, it is possible to verify the accessibility of the corporate system and manage all connections using Single Packet Authorization (SPA). Trusted users who have successfully passed the authentication process can access the resources granted to them while denying responses to connection attempts from users who do not have access authority.
All authentication transitions to a black cloud environment where the network’s attack surface is not externally detectable, providing protection against DDoS(Distributed Denial of Service) attacks and eliminating risks such as IP exposure and port exposure.
Thus, single packet authorization (SPA) is highly efficient because it does not require separate authentication procedures or the storage of sensitive data during user authentication and authorization. Moreover, encrypted packets cannot be intercepted or decrypted during transmission.
② Mutual TLS (mTLS)
Mutual TLS (mTLS) is a communication method that is well-suited for the zero-trust architecture. It facilitates a mutual authentication process, ensuring that both parties verify each other’s identity before establishing communication at endpoints within the network.
Traditionally, TLS provides one-way authentication to verify that a client is connecting to a trusted server. In contrast, mTLS performs two-way authentication using information from TLS certificates, establishing trust not only for clients but also for users, devices, and servers within the organization. This enables a more secure network environment by encrypting the public network connectivity section between users, controllers, and gateways with mutually validated TLS.
③ Access Control
Access control is required when building micro segmentation that manages differentiated access rights based on the user’s position and permission level.
Unlike network-oriented security, which is controlled based on IP addresses, Software Defined Perimeter (SDP) is a framework that controls access based on identity. It grants access only to authorized users and devices by verifying network devices, terminal status, and user IDs.
Even when the user has permissions, by limiting access authority on an application unit basis and allowing access only to authorized network resources, it is possible to protect the data and reduce the risk of data leakage caused by user misuse.
Security experts both in Korea and around the world emphasize the importance of implementing zero trust. However, they also acknowledge the challenges involved in organizations’ adoption of zero-trust technology. In response to these concerns, Cloudbric Private Access Solution (PAS), a SaaS-type SDP-based Zero Trust Network Access (ZTNA) security solution, has been launched.
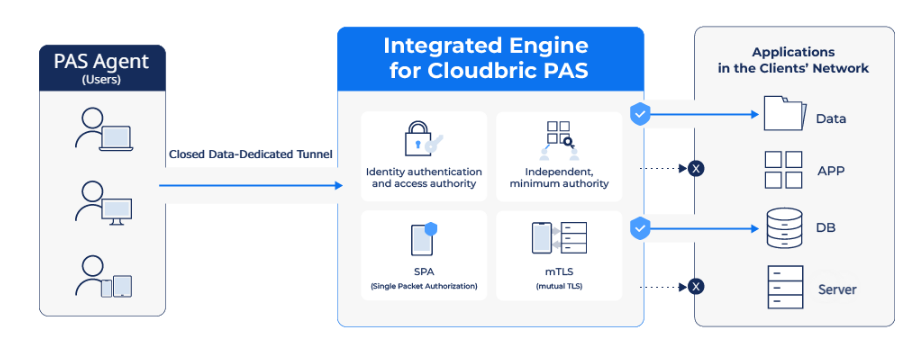
📌 Learn more about Cloudbric PAS
Experience Cloudbric PAS, offering the highest levels of network security with unparalleled flexibility and agility to adapt to enterprise changes. Benefit from rapid identification and defense against potential failures, swift deployment, and cost efficiency.





