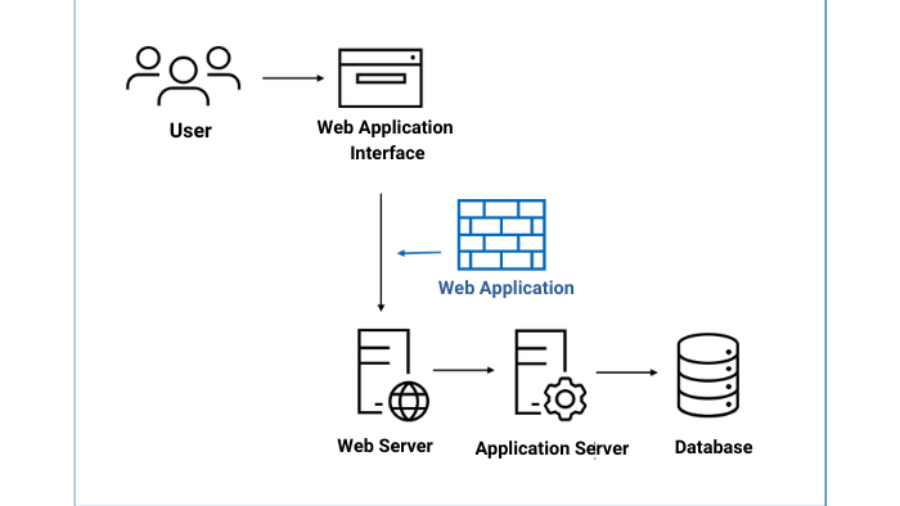
Depending on your business environment and purpose, you can build a more effective security system by using a web application firewall that is suitable for you. Today, we will look at the features and advantages, and disadvantages of hardware, software, and cloud-type web firewalls. Let’s take a look at how web application firewalls are hosted and where they are located within t ...
A Closer Look at 3 Major Aspects of The Future of Cybersecurity
Cybersecurity is a field in high demand. With the modern shift to virtual systems and work processes, data security professionals have never been more needed. But these professionals are hard to find. An estimated 3.5 million unfilled cybersecurity positions are expected to be on the market in 2021. Soon, we will see developments in cybersecurity that alter the prospects and roles ...
3 Ways to Minimize Data Exposure When Surfing the Web
Smartphones, laptops, smartwatches, and other various IoT devices available and used by people has led to a rapid increase in the amount of data generated by each individual. Consequently, the technology of data collection, analysis, and utilization has evolved leading to an ever-importance of user data. Even with regulations with regards to personal data such as GDPR, companies ...
Five Ways to Keep Your Website Safe from Bots
Did you know that more than half of the traffic on the Internet are bots? Bots can play a beneficial role but can also be used to execute deadly attacks. Bots, which can be utilized to play for both sides, need to be a concern for Internet users-- who in turn need to understand what a bot is capable of doing and ways to block malicious bots. Typical examples of ‘good’ ...