With the recent COVID-19 pandemic, many companies have shifted to remote work environments. This has allowed employees to work from home or at least partly obtain a flexible schedule. But this shift has triggered cybersecurity concerns due to an increased reliance on cloud-based applications and services.
The rising cybersecurity threats have caused companies to encourage their remote workers to use VPNs for secure connections to company networks, data, systems, and applications. But are VPNs safe and effective enough for remote work?
VPNs were developed almost two decades ago to provide a secure connection to organizational networks. They were not designed for today’s cloud-based work environments like the hybrid, private, and public models. Using a VPN in today’s work environment is akin to entering the modern battlefield with an old canon to fight enemies armed with advanced weapons. Not to mention the latency issues found in most VPNs, affecting worker productivity and efficiency.
So, is there a better alternative to a VPN? Enter the zero-trust network access (ZTNA) model! ZTNA solutions like Cloudbric Remote Access Solution offer users an easy and secure way to access corporate networks from various devices, whenever and wherever they like. These solutions provide a cloud-based channel for users to securely access data and resources within a private network.
As remote work becomes the norm for most companies, it is essential to be realistic about how your company views cybersecurity. The first step is to decide if VPNs or zero trust should be at the heart of your company’s cybersecurity policy.
Is VPN Reliable for Granting Remote Access to Corporate Networks?

VPNs are the traditional tools for protecting your privacy, data, and identity online. They create a secure tunnel between your device and the internet, keeping your data safe from prying eyes. But not all VPNs are the same though. Some offer better encryption than others or have more servers worldwide to bypass geographic restrictions.
But are VPNs robust enough to protect the modern work environment? The short answer is NO! VPNs are designed for the conventional perimeter-based security frameworks. They have many shortcomings, including the following, that make them unworthy of the modern remote work settings.
- Unlike ZTNA platforms like Cloudbric RAS that secures a flat network with linear access, the legacy perimeter-based security model of a VPN gives malicious actors a large attack surface. Attackers can exploit vulnerable VPN credentials or use compromised credentials to gain full access to the entire network, causing significant damages.
- VPN provides excessively-liberal access to users, allowing them to acquire or modify data stored in different applications. That’s because it is developed for network-level visibility without control over the application layer.
- VPNs offer limited or no support for cloud infrastructures because they are typically developed for on-premises networks.
- VPN security isn’t adaptable to the ‘bring your own device’ (BYOD) trend. This increases the risk of malware infections and network intrusions.
- VPNs are slow and experience latency problems because, in most cases, network traffic is routed via a data center before being sent to a user through the VPN. This can be pretty frustrating during video meetings.
- VPNs are expensive to manage and maintain, besides being time-consuming to configure. You have to configure them manually on your on-site corporate servers.
Given the limitations of VPNs, it is always a good idea to switch to the ZTNA remote access model. But how is a ZTNA better than corporate VPNs? Let’s have a look!
Zero Trust Network Access (ZTNA) is Better Than VPNs
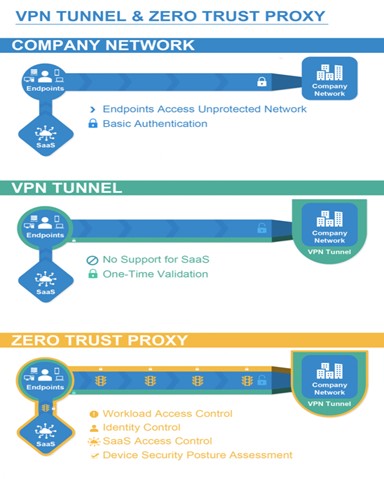
Based on zero-trust principles, ZTNA solutions moderate access to all users by executing cyber security policies at the identity level. Unlike VPNs, ZTNA is focused on application-specific permissions. It establishes an access control system where every device has to prove its identity before accessing any resource on the network.
Zero Trust Network Access is the best and secure way to modernize legacy networks with cloud-based computing environments. The role-based access controls enhance security by enabling greater visibility into what devices are connecting to your network. As such, it improves your security posture through more vigorous enforcement of policies.
Here’re more reasons why the ZTNA approach is better than a corporate VPN:
- ZTNA is software-defined, which allows it to execute the perimeter as a virtual barrier rather than an actual physical network boundary. As such, you can use it to perform micro-segmentation, and secure resources left vulnerable by a VPN.
- ZTNA manages access attempts on a case-by-case basis. As such, you can rest assured users will not get access to assets outside their roles or privileges.
- Web-based ZTNA doesn’t require software installation on the devices of users. That means remote workers can easily and securely access organizational networks and assets.
- Users (or hackers) will not gain full-fledged access to your entire network, thanks to the role-based access model. This also helps reduce the risk of DDoS attacks.
A ZTNA keeps logs of how users interacted with an organization’s digital resources and assets, making the audit process super easy.
Switch to ZTNA With Cloudbric
As you can see, ZTNA solutions overcome the limitations of VPNs, besides offering an array of advanced security features. If you want to take your remote work model’s security to the next level, Cloudbric Remote Access Solution has your back.
Grounded in ZTNA architecture with three-layer security comprising traffic monitoring, user authentication, and hack prevention, our remote access solution is the best alternative to the traditional corporate VPN.
Why Choose Cloudbric?
Our in-house solution is backed by next-gen technologies to provide 360-degree protection to your network and digital resources.
Here’re some solid reasons why Cloudbric RAS is better than VPNs or other ZTNA solutions:
1. Quick and Easy to Get Started
is a software-as-a-service product that requires no additional hardware or software installation. Using a web browser, authorized users can access your corporate network anytime and anywhere.
2. Infallible Security
continuously monitors and identifies cyber threats, including Cross-Site Scripting (XSS), SQL injection, and DDoS attacks. The best part: it uses two-factor authentication to allow authorized users to access your company network, which goes a long way toward reducing threats.
3. Traffic Monitoring
Unlike VPNs, Cloudbric RAS stops unapproved users from accessing your network. Plus, it monitors and blocks threats originating from within your network.
4. More Powerful Features
comes loaded with all the features of an excellent ZTNA solution. That means our RAS provides secure, role-based access to your remote workers to the data, apps, and other digital resources on the web server within your private network.
Check out more reasons why it is a good idea to switch to Cloudbric Remote Access Solution.
Contact us for more information.






