What is DDoS? DDoS Attack Status and Countermeasures
Distributed Denial of Service (DDoS) attacks have become increasingly prevalent in our society, occurring frequently for financial and political purposes. These attacks create social chaos by bombarding critical infrastructures, including manufacturing, with overwhelming DDoS attacks. The consequences for targeted institutions and companies are devastating, resulting in business paralysis, financial losses, and a decline in their brand image.
So, what exactly is DDoS, and what measures should we take to combat it?
—
Distributed Denial of Service (DDoS)
DDoS, an acronym for Distributed Denial-of-Service attack, occurs when multiple systems are utilized to flood a target web server or network. The objective is to overwhelm the network with a massive volume of traffic, thereby preventing legitimate users from accessing website resources or network services.
In recent years, the size and frequency of DDoS attacks have grown significantly. Moreover, these attacks have evolved and diversified their techniques, including the emergence of Ransom Distributed Denial of Service (RDDoS) attacks that demand monetary compensation.
While traditional DDoS attacks employing massive traffic volumes remain a serious concern, special attention should be given to attacks that exploit application vulnerabilities, potentially leading to data deletion or leakage on web servers. Therefore, it is of utmost importance to conduct a thorough analysis of attack techniques and proactively respond to mitigate their impact.
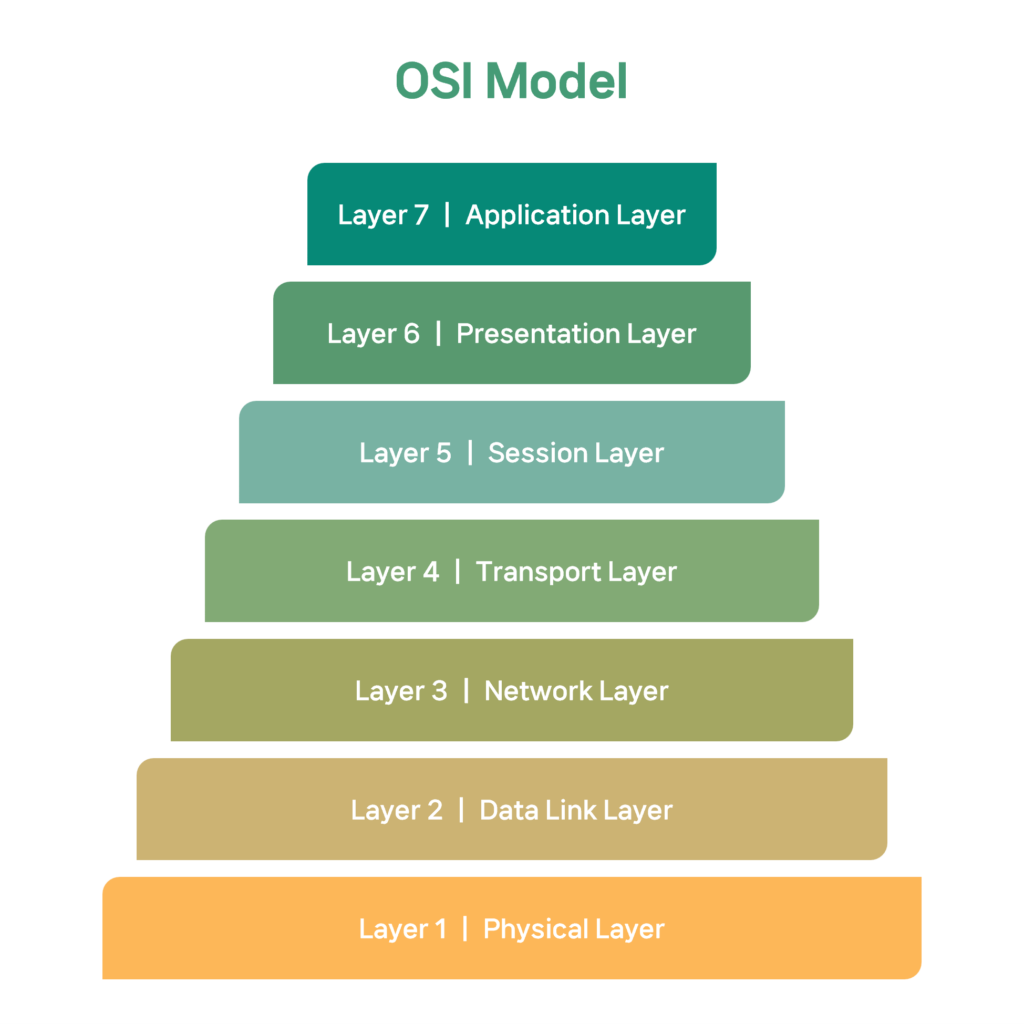
DDoS attacks typically occur in Network Layer (L3), Transport Layer (L4), and Application Layer (L7) based on the Open Systems Interconnection (OSI) model 7-layers of a computer network. As a result, it is necessary to analyze and respond to attacks on specific layers, as well as threats from layers ranging from L3 and L4 in the infrastructure layer to L7 in the application layer.
DDoS Attack Status

The frequency of DDoS attacks worldwide has been experiencing a significant increase year after year. In the first quarter of 2013, the number of DDoS attacks stood at 235,000. However, a decade later, in the first quarter of 2022, this figure skyrocketed by an astounding 807%, reaching 2.9 million attacks.
During the latter half of the year 2022, there were staggering numbers of DDoS attacks, with as much as 463 petabits of traffic and over 75 trillion packets being generated in a single day. Additionally, there was a 110% increase in bombarding attacks, which involve overwhelming networks with heavy traffic. Internet Service Providers (ISPs) are the primary targets of these attacks, followed by wireless mobile carriers, who face an increased threat due to the rise of 5G communication at home.
(*A packet is a bundle of data divided into small units to facilitate data transmission.)
A concerning trend in recent times is the notable rise in DDoS attacks driven by political motives, such as the Russia-Ukraine conflict. These attacks aim to instill anxiety or disrupt systems within neighboring rival countries. Furthermore, DDoS attacks are also utilized as a potent means to extort money from companies and institutions by threatening to launch advanced DDoS attacks against them.
How should we deal with DDoS attacks that cause social chaos across borders?
DDoS Attack Protection
DDoS attacks can cause severe downtime for businesses and organizations. Users generally start feeling uncomfortable after just 10 seconds of service disruption, and it takes as little as 5 minutes for a DDoS attack to tarnish a company’s reputation and result in financial losses. Therefore, real-time detection of threats, along with prompt analysis and response, are crucial in mitigating the impact of these attacks. In today’s constantly evolving threat landscape, implementing robust DDoS security solutions is essential to safeguard your business, organization, and users.

(DDoS Attack mitigation – Cloudbric ADDoS)
Cloudbric ADDoS is an innovative DDoS mitigation service that harnesses the power of edge computing technology. With its distributed intelligence collection, analysis, and distribution capabilities, it effectively combats DDoS attacks across multiple edge locations, providing a comprehensive defense strategy against attacks originating from any corner of the globe.
By utilizing 73 globally distributed edge networks, Cloudbric ADDoS offers robust protection against a wide spectrum of DDoS attacks, from large-scale assaults reaching up to 100Tbps to even smaller and more sophisticated attacks. The service intelligently distributes traffic to the nearest edge nodes based on the request location, ensuring an exceptionally swift response time. All traffic is analyzed in real-time and automatically transitions to DDoS mitigation mode within one second when an attack is detected to keep the server safe.
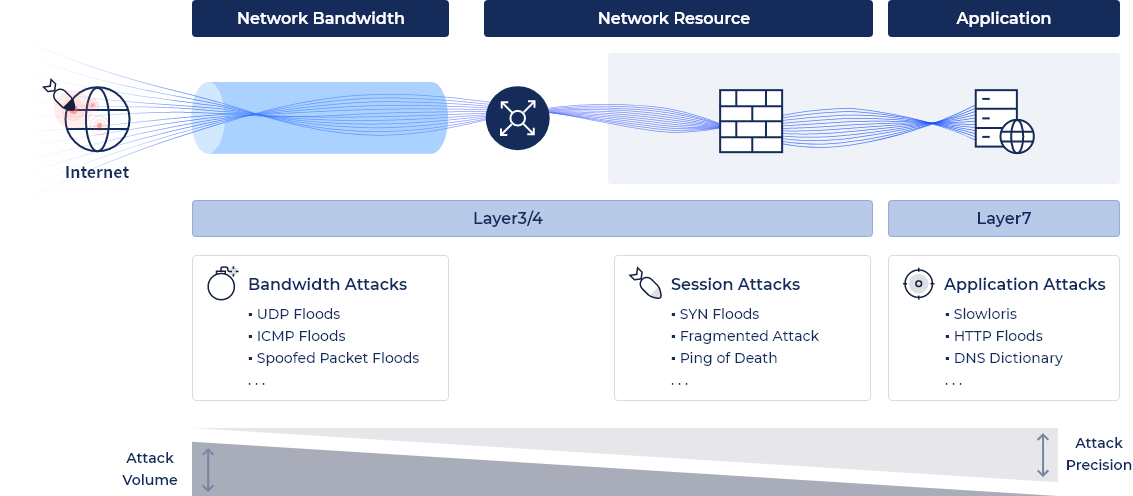
(DDoS Attack mitigation Cloudbric ADDoS)
While traditional measures focus on specific layers of the OSI model, Cloudbric ADDoS is a security service optimized for the defense of DDoS attacks that capture threats against network layers (L3), transport layers (L4), and application layers (L7).
📌 Want to learn more about Cloudbric ADDoS? .. [Click here]
—
DDoS attacks are constantly evolving, becoming more intricate and challenging to prevent. Traditional security measures may not be enough to counter these new threats.
Proactively respond to advanced and intelligent web attacks by adopting Cloudbric ADDoS.





