What are the security measures for the web application attacks, the No. 1 information leakage accident

It is no longer an exaggeration to say that more than half of daily life is done through the web, such as shopping at the Rakuten market or researching necessary information on Google. In the case of companies, online business is essential now. However, the web doesn’t just bring benefits. Cyberattacks targeting the Web, especially “Web applications”, are on the rise, and no matter when an accident occurs, it’s not strange anymore. Therefore, this time, I will explain the reason why web applications should be protected and the “Cloud-based type WAF” which is a security measure that companies can easily adopt.
The security of the application layer is essential for the safety of IT systems.
The web application that belongs to the application layer is the closest layer to the user in the IT system. Therefore, it is a good target for hackers. In fact, even in the “IPA Information Security White Paper” released in 2019, ‘web application attacks’ are ranked No. 1 in information leakage accidents, so more robust security is required.
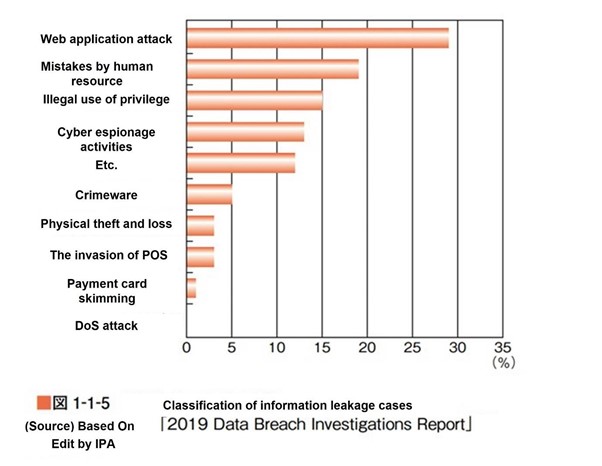
Source: IPA Information Security White Paper 2019
First, Let’s take a look at the security of IT systems in general. In the network area where data is transmitted and received, security measures such as controlling access to IP / Port and detecting harmful traffic are applied. The system area contains familiar operating systems such as Windows and acts as a platform for running applications. In the system area, measures such as application of security patches and detection of illegal codes in the system are generally taken.
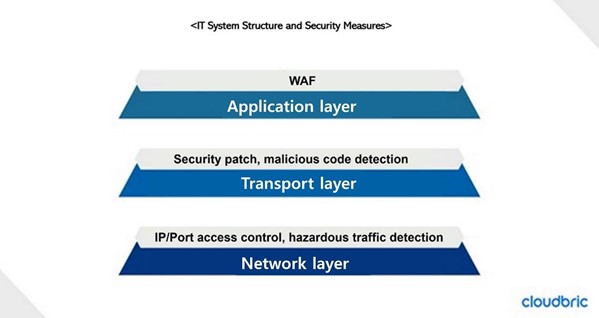
If so, what security measures should be taken for the application area? In the application layer, commonly used functions and services such as websites and applications are operating, so there are many cases where data is stored and used. In particular, web applications often accumulate a large amount of data. Therefore, there are many cases that hackers target which lead you to have stronger security measures. However, it cannot be said that security awareness is still infiltrating compared to the network or system area. A representative security measure that companies are taking is WAF.
WAF in charge of web application security
WAF (Web Application Firewall) is, as the name implies, a security measure that protects web applications. In addition to preventing direct attacks, it also prevents information leakage and website forgery. Currently, various WAFs are on the market, but they are roughly divided into three types, “appliance type WAF”, “software type WAF”, and “Cloud-based type WAF”.
Appliance type WAF
The appliance type WAF is operated by hardware. It can be said that it is the basic form of WAF. Since it is installed right next to the server, it boasts fast processing speed and high performance.
Software type WAF
Software-based WAF is operated in the form of a virtual machine (VM) without using physical hardware. The cloud-operating system is drawing attention, but it is a WAF that is suitable for VM.
Cloud-based WAF
Cloud-based WAF is a form that uses WAF installed on the cloud as a service. In other words, it’s a WAF subscription service. Since it is not necessary to use physical equipment and hardware, it is easily used by users who want to use WAF. For instance, Cloudbric WAF+ is equipped with Asia No.1 detection engine.
Among them, Cloud-based WAF is attracting attention from many companies as it has the characteristics of “convenience” and “reasonable price”. Unlike appliance-type WAFs and software-type WAFs, it can be easily installed by simply changing the DNS, and it does not require additional costs such as cost of management and update, so in fact, it is used by many companies. Cloudbric also protects more than 700,000 sites all over the world.
Cloudbric keeps you secure with a logic-based detection engine
Cloudbric WAF+ is a cloud-based WAF that is equipped with the engine of “WAPPLES”, which has the largest market share in the Asia-Pacific market. It has been highly evaluated by many customers through its features of “convenience” and “reasonable price”. You can use the service just by simply changing the DNS, and Cloudbric offers various pricing plans according to the user’s situation. But that’s not the only feature of Cloudbric WAF+. The greatest weapon of Cloudbric WAF+ is the function of “logically analyzing, understanding and defending attacks”.
Most WAFs have this technology called “signature matching”. This is a way to find a pre-written list and inspect traffic. However, Cloudbric has a logic-based detection engine that detects attacks according to the rules. In the case of WAF that uses signature matching, there are cases where it is not possible to prevent attacks that are not on the list. However, Cloudbric analyzes attacks thoroughly on a logical basis, so it can respond appropriately to unknown attacks such as zero-day attacks. In addition, it provides all-in-one package to safely protect the website, such as blocking DDoS and issuing SSL certificates for free.
Last but not least
In the near future, Web applications will be used for various purposes. However, web applications that have not taken security measures are just food for hackers. Cloudbric is highly evaluated by many customers as they “work intelligently” in addition to the convenience and reasonable price that are the advantages of Cloud-based WAF+. Try out Cloudbric’s free trial now when security measures are needed to protect customer information and protect the company’s reputation.
Check out Cloudbric’s product lines:
No.1 in the Asia Pacific – WAF with A.I & Logic-based detection engine: Cloudbric WAF+
Cloud-based DDoS attack defense service with edge computing: Cloudbric ADDoS
Zero Trust Network Access-based Remote Access Solution: Cloudbric RAS
Blockchain: Blockchain Security Solution
Click here for inquiries regarding the partner system





