Last time on our blog, we explored what made fileless ransomware so different from other malware and how it might just be the new trend within the hacker community. In this guest blog post, we break down how end-to-end fileless attacks occur.
Malware makers are always looking for an edge, a new way to breach corporate networks or compromise personal devices. Ransomware is one popular vector — victims find themselves locked out of critical files and services, and are forced to pay or risk losing their data forever.
Security firms and antivirus (AV) tools are getting wise to ransomware tactics, however, prompting hackers to pursue a new tactic: End-to-end fileless attacks.
Fileless Fears
The threat of fileless attacks is on the rise. Attackers were recently able to store fileless malware on compromised government servers and create a targeted phishing campaign that masquerades as the SEC’s Electronic Data Gathering Analysis and Retrieval (EDGAR) system. So it’s no surprise that 78 percent of organizations are worried about fileless malware, and 83 percent of security pros want more information about these attacks.End-to-end fileless attacks are designed to evade AV services. They accomplish this aim by leveraging applications already present — and whitelisted — by devices, rather than attempting to sneak malicious software payloads through defenses. Often, these attacks rely on command-line apps such as PowerShell, but others may download commonly approved services such as Flash, which has known vulnerabilities but is often part of corporate IT whitelists.Without any unknown software to analyze, AV solutions are silent, allowing hackers to carry out their work undetected and unimpeded. The result? One in three infections now has a fileless component, and more than half of all successful attacks are fileless as security teams struggle to keep pace with this emerging threat vector.
Breaking It Down
How exactly does an end-to-end fileless attack occur?Phishing emails remain the most common starting point. Users receive a message that looks legitimate, but contains an attachment or asks them to click on a spoofed link. Then, attackers exploit web browser vulnerabilities or weaknesses in already-whitelisted apps to start a PowerShell script, and issue commands that authorize the download of malware packages. Since the initial download happens behind firewall and AV lines, most devices won’t recognize this behavior as suspicious, giving attackers time to fully compromise systems.
Why It Matters
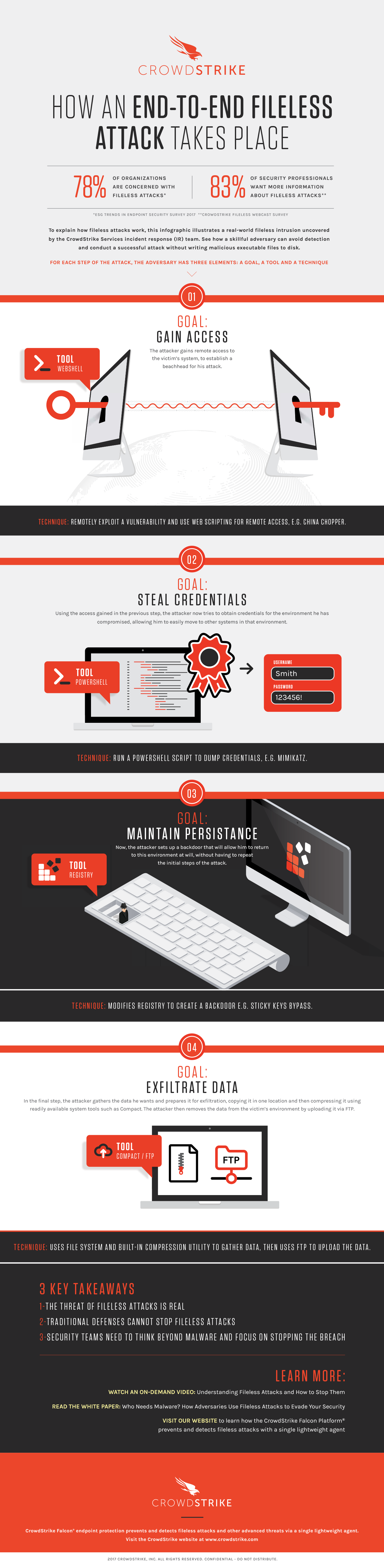
Typically, attackers have four main goals when it comes to fileless infections:
- Gain Network Access — Once inside your network, attackers can lie in wait or build a foundation for future attacks.
- Steal Credentials — From banking information to online retail accounts, payroll data and sensitive employee information, hackers are looking to leverage what they find.
- Maintain Persistence — Not all attacks happen right away. Cybercriminals may use fileless methods to gain persistent access, and then continue to compromise networks over time.
- Exfiltrate Data — With undetected access to files, malicious actors use common compression tools to reduce data sizes and transmit information via FTP.
Using multiple tools and techniques such as web shells with compromised web scripting or registry modification to create a persistent back door, attackers can breach systems in a way that both evades typical attack detection and puts them in a position of power — instead of trying to break down the door, they’re working from the inside.How do users handle a no-software security breach? Start by changing what you’re looking for — instead of checking whitelists or zeroing in on specific malware packages, effective defense requires a solution that seeks behavioral indicators of a potential attack, then blocks malicious activity before it breaks network barriers.Fileless attacks are on the rise. Fight back with a new perspective on protection.