In the last two years, receiving an extortion letter threatening to “pay us in bitcoins or your site will experience a distributed denial-of-service (DDoS) attack” has become nearly routine.
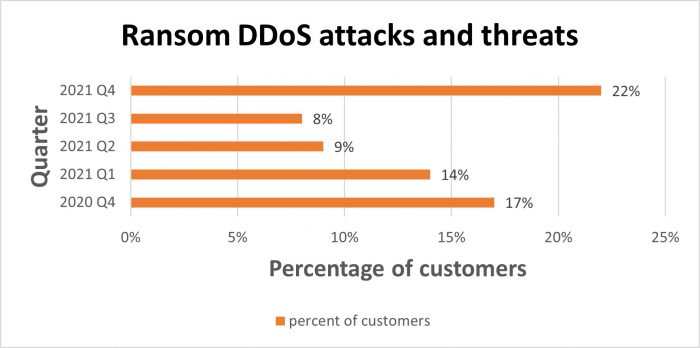
According to InfoSecurity Magazine, the 11 most enormous ransom DDoS assaults of 2020 cost the attacked firms almost US$144 million to pay the ransom, investigate, and repair their applications. In the third quarter of 2020, cybercriminals used more sophisticated and diverse attack vectors to carry out 50 percent more ransom DDoS attacks than in the same period of 2019.
DDoS attacks show no indications of going away anytime soon. Let’s see how cloudbric solutions can help.
Ransom DDoS vs. DDoS
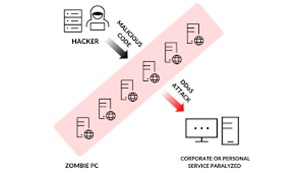
A ransom DDoS (RDDoS) assault occurs when malevolent parties threaten an individual or organization with a distributed denial-of-service (DDoS) attack to extract money from them.
The wicked party in question may start a DDoS attack and then demand payment to stop the attack, or they may send the ransom note first, threatening a DDoS attack.
A DDoS attack attempts to deplete the resources of an application, website, or network, preventing legitimate users from receiving service. DDoS attacks overwhelm their targets with trash network traffic, much like a traffic jam on a highway.
Types of Ransom DDoS Attacks
The following DDoS attack types are among the most common and possibly destructive. Knowing about them will aid security teams in developing proper defensive and mitigation tactics.
DNS amplification
This is a form of “reflection” attack in which the perpetrator begins by sending small queries to the intended victim’s faked IP address. The responses inflate into significantly bigger UDP packet payloads and overwhelm the targeted servers by exploiting weaknesses on publicly available domain name system (DNS) servers.
UDP Flood
The offender deluges arbitrary ports on a target network with a UDP datagram–containing IP packets in this attack. The harmed system tries but fails to match each datagram with an application. As the system handles the UDP packet reply volume, it quickly becomes overwhelmed.
HTTP Flood
This attack targets an application or web server by sending a considerable number of seemingly simple HTTP GET or POST requests. These requests are frequently written in such a way as to prevent detection, with the perpetrator having gathered helpful information on a target before the attack.
SYN Flood
A three-way handshake is required for every TCP session between the two systems involved. An attacker uses an SYN flood to bombard a victim with so many connection requests that it can’t keep up, causing network saturation.
It isn’t simply the increase in DDoS attacks that makes them disruptive; cybercriminals are using new ways to develop their attacks to overcome cloud-based and on-premises defences.
“Over the years, the toolset underlying these attacks has matured”
Hardik Modi, Netscout area vice president of engineering, threat, and mitigation solutions, said.
For example, cybercriminals increasingly employ multi-vector DDoS assaults, which intensify attacks by directing traffic towards the victim across multiple channels.
Multi-vector attacks are becoming more diverse, according to researchers. The greatest of these attacks in 2020 involved 26 vectors. Several attacks were used between 27 and 31 separate vectors during the first half of 2021, and an attacker can switch between them to make the attack more difficult to disrupt.
Major Events of Ransom DDoS Attacks
Some of the major events of ransom DDoS attacks are as follows;
New Zealand Stock Exchange
In August 2020, the New Zealand Stock Exchange (NZX) halted trading for four days giving consumers only a fraction of the availability needed to conduct business. The attackers first overwhelmed the NZX with a torrent of offshore digital traffic, then began targeting the exchange’s individually listed companies after switching to cloud-based servers.
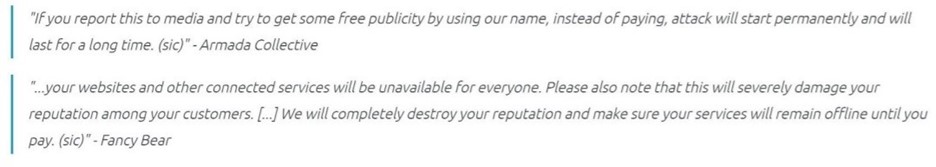
A DDoS attack was the source of the problem, accompanied by a ransom message. The damage to their clients and reputation was significant, and attackers have used the episode as an example of what to expect from an RDDoS attack.
Australian Banks DDoS Extortion
On February 25, 2020, it was revealed that the Silence gang was using DDoS attacks to extort money from Australian banks and other financial institutions unless they paid a ransom.
The Silence group has also been associated with bank thefts in Eastern Europe, South and Central Asia, and Sub-Saharan Africa. To stop the attack, the group requested payment in the cryptocurrency Monero.
Greek Banks Ransom DDoS Attack
Hackers threatened to shut down three Greek banks’ systems unless they paid a bitcoin ransom in late 2015. The banks’ websites were continuously knocked out for many hours when they refused.
Although some investigators suspected it was a copycat attack using the same name, the organization claiming responsibility for the extortion said it was part of the Armada Collective, which had previously targeted multiple businesses.
How Did it All Start?
In the history of computing, July 22, 1999, is a scary date. On that day, a computer at the University of Minnesota was unexpectedly attacked by a network of 114 additional computers infected with the Trin00 malicious software.
This was the first distributed denial of service (DDoS) attack in history. But it didn’t take long for the strategy to catch on. Several more websites, including Yahoo, Amazon, and CNN, became victims in the months that followed.
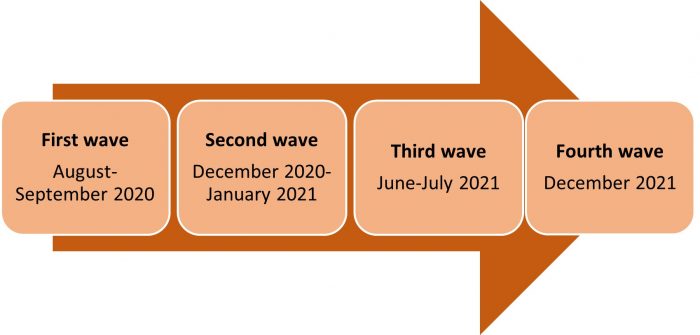
First Wave
The first wave of ransom DDoS attacks occurred in September 2020, with a significant increase in ransom DDoS attacks affecting thousands of large business enterprises worldwide. The extortionists claimed a link to the infamous Threat Actor Groups Fancy Bear and Lazarus in this first wave.
Second Wave
Then, between December 2020 and January 2021, the second wave of ransom DDoS attacks appeared, striking without warning and inflicting havoc on their targets.
Third Wave
In the summer of 2021, ransom DDoS attacks resurfaced for the third time, with corporations discovering once more how, for a minimal cost, ransom DDoS extortionists may target crucial network infrastructure to damage their businesses.
Fourth Wave
To distinguish this fourth and most current wave from the others, targets got the threats as a request on their Web Application Firewall (WAF) platform or as a SIEM request. While only online forms were seen to be used to express ransom demands in the past, this was the first-time threats were sent through a SIEM.
What Should be the Defence Strategy against Ransom DDoS?
How should a business respond? The three tactics outlined below detail how to avoid or react to DDoS assaults on networks:
Use a Content Delivery Network (CDN)
This strategy reduces the visibility of company infrastructure because IT teams can hide it behind a CDN. These networks are broad and diverse, and they can safeguard e-commerce sites and the corporation itself if the organization subscribes to DNS and DDoS mitigation.
Keep it in-house and DIY
Organizations can utilize an intrusion prevention system, firewall technology, and specialized hardware to prevent and respond to DDoS attacks in-house.
This strategy is best suited to organizations with equipment in colocation facilities, where traffic reaches ISPs via a cross-connect, protecting downstream bandwidth that goes to the rest of the company.
Buy a Service from an Internet Service Provider
Many ISPs provide DDoS mitigation services such as cloudbric. However, when a corporate network is attacked, the organization must report the issue to the ISP to commence mitigation.
Cloudbric ADDoS responds to a wide spectrum of advanced DDoS attacks, from frequent DDoS attacks to multi-vector attacks and application attacks, at rates of up to 65 Tbps via global edge computing nodes.
While Cloudbric WAF offers an essential DDoS detection service, Cloudbric ADDoS provides even better DDoS protection. This web application security company specialized in attacks on application layer (L7), utilizes a logic based intelligent WAF engine that was voted as Asia Pacific’s no.1 for consecutive 5 years.
Conclusion
Enterprises must protect themselves with the rising frequency and severity of DDoS ransom assaults. Cloudbric’s fully managed web application security solutions aid in efficient protection against DDoS ransom attempts.
To discover more about how we can assist your business and which deployment is appropriate for you. Please visit cloudbric.com/website-security and contact us here.






