In the last of our three-part series discussing WAF dissatisfaction among WAF customers, we will focus on why managing a WAF is often considered to be difficult, resource-draining, and expensive. WAFs don’t come out-of-the-box ready, so some configuration will likely be needed.
The burden of managing a WAF deployment falls upon your security team. This can be a complex and time-consuming effort. Even if you have a security team, they may not have the time to focus solely on WAF.
Ponemon Institute found that the average organization hired 2.5 security administrators, who spent 45 hours per week processing WAF alerts and an additional 16 hours per week writing new rules for the WAF. To manage a WAF, users are required to have an average headcount of 2.5 full-time employees, and an annual budget in excess of $400,000 USD. Since a WAF is complex to maintain and licenses are costly, maintaining a WAF is resource-heavy for organizations.
Take for example a common cybersecurity engineer job posting:
Job Description
Candidates will develop, support, tune, and deploy Web Application Firewall security solutions. Primary day-to-day job duties involve –
- Web Application Security: Engineering, deployment, and operations of Web Application Firewall security solutions and integration of those platforms with other security solutions as required.
- Performing hands-on Web Application Firewall deployment, configuration, policy fine-tuning, and maintenance
This is a hands-on technical job. Looking for an experienced candidate with extensive experience in WAF policy fine-tuning and administration.ResponsibilitiesWeb Application Security:
- Engineers configures, deploys, and maintains Web Application Firewall solutions
- Develops advanced alerts/reports to meet the requirements of key stakeholders
- Develops automation for security tools management and workflow integration
- Collaborates with key stakeholders within Information Security and Engineering teams to develop specific use cases to address specific business needs
- Creates WAF rules/signatures to mitigate threats and implements best practices
- Creation and implementation of custom alerting dashboards in SIEM for investigations
- Works extensively with different stakeholders across the company for tuning WAF policies or creating custom signatures
- Aids in gathering metrics for measuring Performance and Risk
- Provides ongoing support to existing monitoring capabilities and data collection systems.
- Provides development support for the expansion and implementation of new systems.
Not all organizations have the budget to hire an engineer or group of engineers to fulfill the responsibilities outlined above. Luckily, if you lack the resources (time or IT staff), then there are solutions for you within the WAF market, which will be discussed later. First, let’s explore the tasks that must be fulfilled by the security team for proper WAF configuration.
Set-Up
WAF setup really depends on the type of the WAF your organization requires. For example, an appliance-based WAF (sometimes called on-premise or hardware WAF) and a cloud-based WAF will have very different setups. WAF deployment also depends on where your applications are located, what services you need (e.g. load balancing), and how or who will manage the WAF. Your WAF vendor may or may not handle the set-up for you – for free or for an additional setup/installation fee.
Processing WAF alerts
 Once a WAF is successfully set up, your tech specialist or security team will be in charge of processing WAF alerts. What does this mean? Web-based threats that are detected by the WAF engine are recorded on a log of raw data. A WAF vendor may provide the user – you – with a console or a dashboard where the raw log data is processed and displayed. For WAFs that do not come standard with a console/dashboard, the security team within the organization will need to analyze the raw data.A good WAF should, therefore, provide you with an intuitive console, an insightful dashboard, and a comprehensive report. Your security team will save valuable resources if the WAF vendor can provide you with the above features. Time and personnel resources will be wasted if you need to analyze all the raw data to implement security policies and rule sets, especially if it’s even more difficult to navigate through a non-user-friendly console.
Once a WAF is successfully set up, your tech specialist or security team will be in charge of processing WAF alerts. What does this mean? Web-based threats that are detected by the WAF engine are recorded on a log of raw data. A WAF vendor may provide the user – you – with a console or a dashboard where the raw log data is processed and displayed. For WAFs that do not come standard with a console/dashboard, the security team within the organization will need to analyze the raw data.A good WAF should, therefore, provide you with an intuitive console, an insightful dashboard, and a comprehensive report. Your security team will save valuable resources if the WAF vendor can provide you with the above features. Time and personnel resources will be wasted if you need to analyze all the raw data to implement security policies and rule sets, especially if it’s even more difficult to navigate through a non-user-friendly console.
Altering WAF security policies
For maintenance, it doesn’t just end with just tracking and analyzing WAF alerts. Security teams are also tasked with creating new rulesets or altering existing WAF policies. The most basic WAFs are designed to let you have control over the traffic that can be allowed as determined by predefined security/WAF rules.WAF rule sets can be configured specifically to target certain attack patterns or provide higher protection levels for certain applications. This can certainly enhance your web security though it may be a complicated task. According to a study by the Neustar International Security Council, approximately 30% reported that they have difficulty altering WAF policies to guard against new application-layer threats.Custom rules are sometimes necessary; for example, web applications that need protection may require a set of unique security requirements not covered by the existing rulesets. For example, if there is an “organization-level” process that resembles an attack, the WAF may mistakenly block it if no special rules are set up. As such, some WAF vendors may already have a well-designed ruleset that requires minimum effort from the user in configuring personalized policies.
Difference between self-managed and fully managed WAF
Traditional WAFs that don’t come equipped with any sort of automation or management support rely on administrators to analyze the incoming WAF alerts. It’s up to the organizations using the WAF to determine if an attack occurred.This is also called a self-managed WAF. In this scenario, your security team retains control over traffic management and security policy settings. However, it’s unrealistic to expect that every organization will have the necessary IT resources and website security expertise or budget needed to manage a WAF.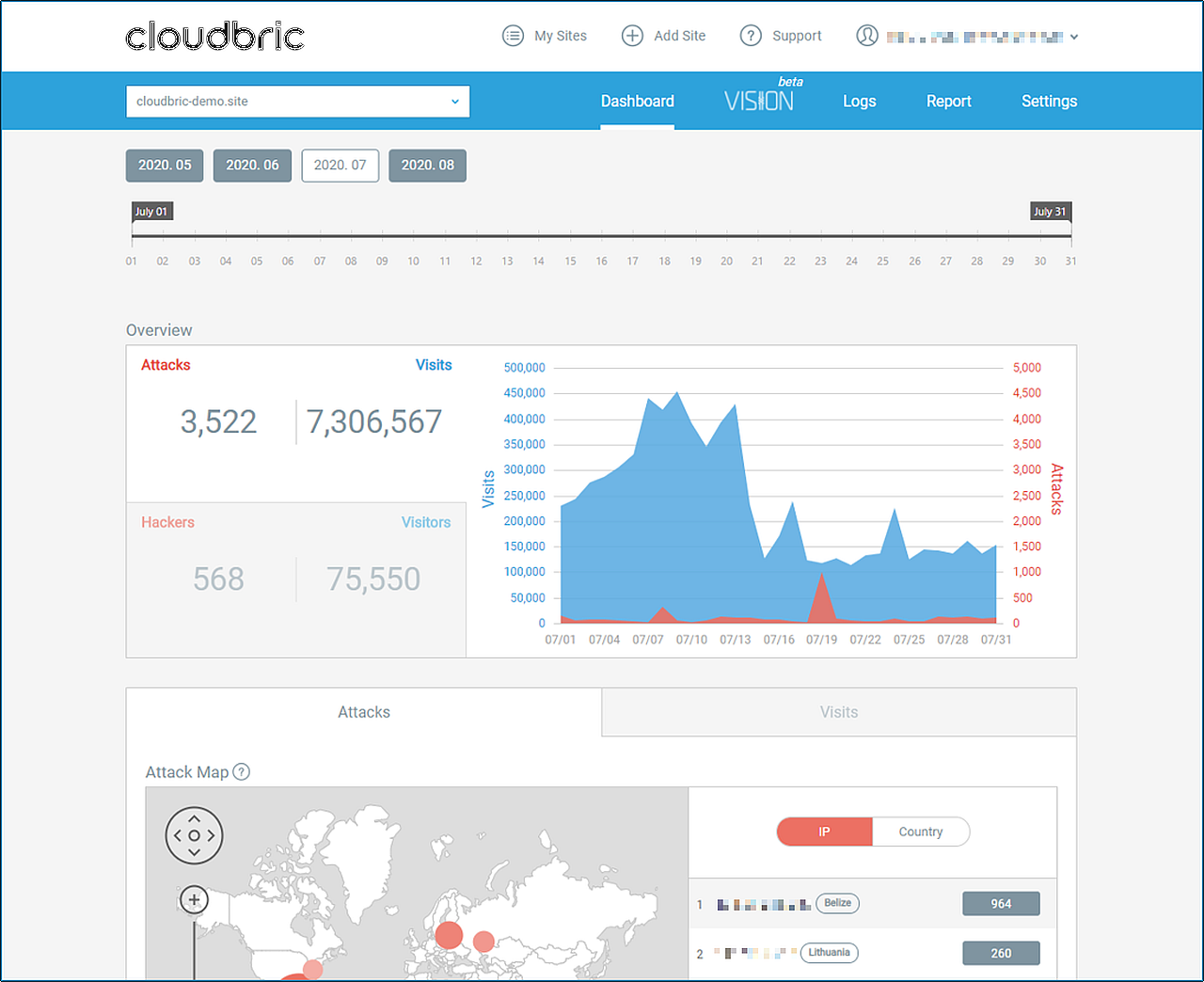 For many organizations, an effective way of managing a WAF is one that provides great visibility into your web attacks and only notifies administrators if any additional threat response is needed. Administrators can log on and see for themselves when, where, and how an attack was executed on their web application with a fully managed WAF.
For many organizations, an effective way of managing a WAF is one that provides great visibility into your web attacks and only notifies administrators if any additional threat response is needed. Administrators can log on and see for themselves when, where, and how an attack was executed on their web application with a fully managed WAF.
Cloudbric SWAP
Cloudbric offers a cloud-based managed service for WAF called SWAP (Smart Web Application Protection). So, what makes SWAP a fully managed WAF service?SWAP removes any WAF management complexity and requires no security policy/WAF rule deployment – greatly reducing any operational expenses. SWAP’s most popular feature might be its 28 unique WAF rules that were developed in-house. These rulesets work together to proactively monitor and track traffic 24/7 and are able to thwart off modified and unknown attacks. In the case of a security event, SWAP will block the traffic and record the event in the logs. To provide transparency, we will send you a report on the attacks that were prevented.System administrators or tech specialists can also log on to Cloudbric’s intuitive console and dashboard further visibility into the security of your web applications. They can also customize their threat responses should they choose.
Conclusion
Have WAFs only survived due to legal mandates rather than their effectiveness for protection? We don’t believe so. While many organizations never put their WAF into active blocking mode, those organizations that do likely see the immediate ROI on their WAFs. To take it a step further, however, ask yourself if your WAF is providing protection against the attacks that matter most to your organization. A WAF with a high price tag or a long list of features won’t always mean you’re in the clear for protection against cyberattacks.





