
As we all know, many data breaches are caused by web attacks. A large majority of web attacks aim to access or send unauthorized requests to a web server in order to disclose outgoing sensitive data coming from the web server. To protect against these attacks, Cloudbric works hard to not only monitor incoming website traffic, but to also analyze all outgoing information coming from an internal source. Hackers can launch various types of attacks to steal a website’s sensitive data; however, Cloudbric can help prevent these attacks from happening in the first place. As we briefly outlined earlier, protecting outgoing sensitive data is just as, if not more, important than protecting against suspicious incoming web visitors. This could be the difference between being a company that properly protects its customers’ data or having it all surrendered to a web hacker at the click of a mouse.
As part of a data leakage prevention series, we will focus on how Cloudbric can protect against a particular type of data exploitation attack called Parameter Tampering. According to OWASP, parameters are set on websites to help exchange information between a user and a web server. Typically, this information is stored within cookies, hidden forms/strings of code, or within a URL. This ultimately increases a specific web application’s functionality and overall user experience with the website, such as inputting login credentials, reviewing price and quantity of products, etc. Hackers frequently work to exploit these website parameters in order to perform identity theft, website manipulation, or simply access user information. These can all lead to more serious forms of web attacks, such as Cross Site Scripting (XSS) or SQL Injections.
What Are My Options?
One way to effectively monitor web traffic data is to utilize a powerful web application firewall (WAF). WAFs are well known for meticulously filtering malicious incoming web traffic to a web server based on predefined detection rules or algorithms. However, WAFs can also be just as effective in analyzing outgoing traffic from a web server as we discussed above. In the case of a potential hacker manipulating web parameters, outgoing traffic from a web server must also be properly secured in order to prevent sensitive customer data leakage. One of the strongest WAFs that you can use on the market is Cloudbric’s enterprise level security. Cloudbric’s state of the art detection technology is designed from Penta Security Systems’s WAPPLES web application technology, which is considered the no. 1 WAF vendor in the entire APAC region by Frost & Sullivan.
How Does Cloudbric Protect My Website?
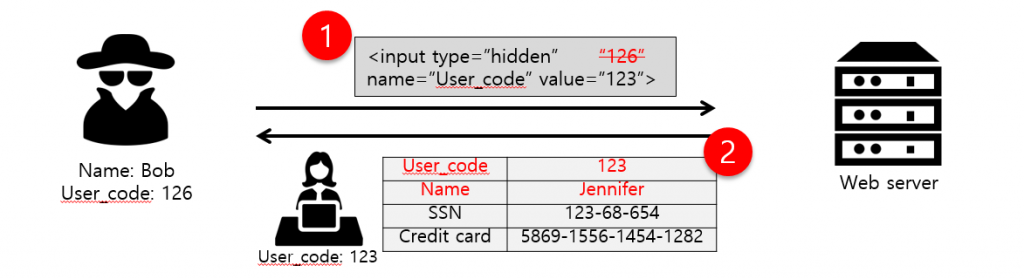
Cloudbric technology logically categorizes the specific behavior of users that interact with web servers into specialized detection rules. This helps WAPPLES utilize its patented self-learning engine to effectively distinguish between trustworthy and untrustworthy users. Additionally, Cloudbric’s self-learning engine can be used to analyze outgoing data transmission and requests between a user and an internal web server. Cloudbric applies web traffic encryption going to and from a web server to help recognize whether certain requests or website parameters are legitimate.
As mentioned earlier, there are many reasons why hackers want to manipulate website parameters. For instance, hackers can either manually or use what are known as proxy tools to modify URL parameters in order to access user account information. Proxies typically act as an intermediary to pull sensitive data from a website to communicate to the end user. In the event of proxy usage, Cloudbric detection rules can monitor such activity under its “Request Header Filtering” rule, which blocks proxy tools that do not have approved header information or does not have a certified username. This can ultimately help prevent identity theft issues such as stealing and selling customer information.
Furthermore, hackers can also manually input or utilize automated tools to alter parameter values. In the case of an eCommerce website, a hacker might notice a site that lists their products at certain price points and is able to manually change parameter values that correlate with that product. This artificially communicates to the web server looking for the user request to communicate back and execute an order at a lower price point. Hackers can use this form of attack to vandalize a website or to take advantage of unauthorized discounts—at the expense of the website owner. In order to prevent this form of web attack, Cloudbric blocks automated tools with its detection rule known as “Suspicious Access Block”. Cloudbric will only allow access to a secured website from a normal web browser. To understand if the access is via a normal web browser, the first time visitor is required to send a cookie—that can be only processed by a browser—to Cloudbric. If Cloudbric receives this cookie, it considers the access as trustworthy and does not block it. This can help prevent issues such as website defacement, vandalism, or manipulation.
The advent of web applications and respective website parameters have helped improve the line of communication and interactivity between a potential user and a website. However, this has also opened the door to various methods of cyber attack, such as web parameter tampering. It is important to stay vigilant of website security, especially when the exchange of personal or private information of users takes place. In order to learn more about Cloudbric WAF services and its enterprise level protection, contact us at global@cloudbric.com or submit an inquiry.





