
Raising security awareness nowadays is more important than ever considering the fact that anyone who has a device connected to the internet can fall victim to malicious attacks. While it may bring certain inconveniences for individuals, business owners can lose everything when a successful security breach takes place; a damaged reputation and relationship with customers can ruin a business.
Investing in a good security specialist as well as organizing cybersecurity training courses or other educational programs for your staff is crucial as these measures increase the protection of sensitive information and the integrity of internal resources.
However, you don’t need to wait until someone tries to compromise your security to assess your protection. Instead, you can do it yourself now.
Most often penetration testing (or shortened pen-testing) is used for these purposes. The core of pen-testing lies in discovering security issues and vulnerabilities of a network, website, or application by breaching it. In a nutshell, it’s a real hacking attack with the only difference from the malicious one – you are the initiator of this attack, you receive the report with the results, and you pay to get hacked. Various ways of launching these attacks exist depending on the aim of this testing.
The most commonly used cases are blind testing when a company that performs pen-testing is not given any information apart from your website name, and double-blind testing when in addition to that your security specialists have no idea that the attack is planned. Also, the tests can be external (when only publicly available resources are targeted) and internal (simulating the attack made by an employee or having the employee’s credentials to corporate resources).
Why may you ever need this?
Here are 3 solid reasons why hacking your own network is not such a crazy idea as it may seem from the first sight.
Reason 1: To discover and oust vulnerabilities in the system
Regardless of the software you use, certain vulnerabilities still exist. According to recent security reports, almost half of web applications have serious security issues, while the medium and low-risk issues were found in more than 80% applications.
In the course of pen-testing, ethical hackers try to simulate the most common practices to gain access to your system, upload malware there, or to steal information. They use XSS attacks, MySQL injections, various PHP exploits, and other common vulnerabilities to upload malware and ransomware on working machines. It’s also possible to simulate the DDoS attack to see whether your network can sustain it.
As a result of pen-testing aimed at discovering the weak system points, you will be able also to pick up additional security solutions you may want to implement in your organization.
Reason 2: To develop security policies within your company
Unfortunately, most often the security policies within a company start after a security incident.
In case of a successful hacking event that was initiated on your end, you will end up understanding the imperfections and backdoors in your procedures, i.e restricting access to sensitive data, launching automatic regular password changes, adding additional authentication such as 2FA or OTP, and initiate logging activity of your employees inside the corporate network.
Also, it can involve updating security tokens within the system within shorter intervals, conducting a regular access audit, and implementing immediate account deactivation once an employee leaves the company.
These things are especially important as the regular means can save sensitive data from leakage. And according to the recent statistics, the number of exposed records at the beginning of 2020 due to data breaches was higher than eight billion, which is four times bigger than the beginning of any other year.
Reason 3: Check if your company is an easy target for social engineers
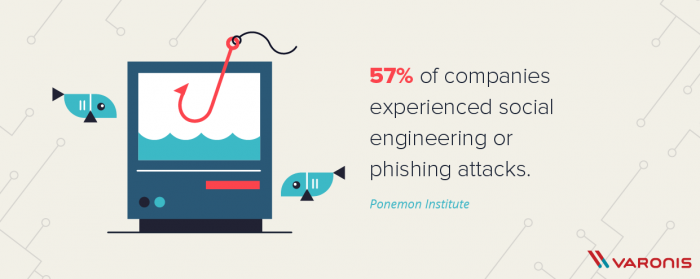 (Image by Varonis, © 2020 Inside Out Security)
(Image by Varonis, © 2020 Inside Out Security)
Unfortunately, there is no ultimate protection for the social engineering attacks since humans are not machines and they cannot block the incoming threats by default. This makes people the easiest target for hacking. Modern social engineers are great manipulators and can use people’s emotions and feelings such as compassion, fear, or desire to help to gain the necessary info.
They can pretend to be a boss requiring a banking account or a customer who forgot their password, or even non-tech savvy people asking you to help them open a tutorial which masks an attempt to force you to download some malware. Even the big technology companies are suffering from these kinds of cyberattacks.
To avoid this, it’s recommended to raise the security awareness of your employees, implementing the verification procedures for customers, setting up a strict policy of internal info sharing, and make sure that employees are reporting all the suspicious situations. In addition, the regular checks involving social engineering can help to estimate the current threats and indicate the learning gaps of your employees.
Wrap up
Based on this information, one can see the benefit of conducting different tests and simulating external attacks (pen-testing) to check the security potential of a business, what information is the least protected and vulnerable to leakages, what flaws exist in the current procedure, and the readiness of your systems and people to counteract security threats.
The results obtained after the application of one strategy or multiple strategies will provide you with the current protection level and the chances of suffering from a given type of real attacks. They also provide the direction your company should take to improve the security, what backdoors need to be closed, and other measures to strengthen the security of your business.
If it is one of those rare cases that the test passed successfully and the security audits did not discover any potential threats, it does not mean that you made your system secure once and for good. Security is like health that requires constant monitoring and regular checkup to make sure everything is working smoothly and avoid unexpected emergencies.





