Chinese Hacker Group Breaches U.S. Government Agencies’ Email
 In the ever-evolving landscape of global politics, the United States and China find themselves locked in a non-physical conflict where cybersecurity competition has taken center stage. Recently, a concerning incident unfolded, shaking the very foundations of the White House and its security apparatus.
In the ever-evolving landscape of global politics, the United States and China find themselves locked in a non-physical conflict where cybersecurity competition has taken center stage. Recently, a concerning incident unfolded, shaking the very foundations of the White House and its security apparatus.
U.S. Government Agencies’ Email Accounts Breached
On July 11, Microsoft announced that it had taken countermeasures after hacking into the email accounts of 25 organizations, including U.S. government agencies.
The U.S. White House confirmed that security authorities had detected alarming indicators of hackers breaching Microsoft’s cloud security system during the previous month. Consequently, they urgently requested Microsoft to conduct a thorough investigation into potential vulnerabilities in their cloud security infrastructure.
Microsoft has officially confirmed that a highly skilled Chinese-based hacker group, known as Storm-0558, has successfully infiltrated the email accounts of approximately 24 agencies, including several U.S. government agencies. Operating covertly, these hackers have managed to evade detection while carrying out their malicious activities.
The U.S. has raised suspicions that Chinese spies orchestrated the relentless attack targeting the U.S. Department of State with the specific purpose of obtaining military secrets and advanced technology. However, China strongly refutes these allegations, asserting them to be completely baseless.
Methods of Attack by the Chinese Hacker Group

Storm-0558, a Chinese hacker group, exploited a security vulnerability within Microsoft’s cloud computing environment, resulting in a breach of the targeted agency’s email account. This intrusion persisted for approximately one month, spanning from May 15 to June 16, until Microsoft initiated an investigation.
The hackers gained unauthorized access to the email system by replicating the required authentication token for logging into Microsoft accounts. In addition to utilizing traditional malicious link methods, they took advantage of security loopholes present in Microsoft’s cloud infrastructure, enabling easy access to accounts and emails. However, due to the exploitation of these specific vulnerabilities, the impact of the hacking attacks was limited to users of Microsoft’s email services.
The Widespread Impact of the Hacking Attack
The severity of the situation came into full view following Microsoft’s comprehensive investigation, leading to a significant shift in awareness. This hacking incident displayed a higher level of sophistication and precision compared to the SolarWinds breach, leaving a profound impact on the global security and software industries.
In December 2020, a group of Russian hackers successfully breached SolarWinds’ network management tool, “Orion,” by injecting it with malicious code. The repercussions spread widely, affecting numerous public institutions and companies worldwide that relied on SolarWinds’ Orion software. Notable targets included government agencies such as the U.S. Department of Treasury, the Department of Commerce, the National Telecommunications and Information Administration (NTIA), the U.S. Department of State, the Department of Defense (DoD), and the U.S. National Aeronautics and Space Administration (NASA). Major corporations like Microsoft and FireEye also experienced significant impacts.
This incident emphasizes the urgent need for systematic countermeasures at both the national and corporate levels to mitigate the potentially exponential damage that can occur in such hacking attacks. Implementing comprehensive security measures across organizations is essential to minimize the adverse consequences of such incidents.
Implementing Zero Trust

In May 2021, the Biden administration of the United States announced its intention to construct a zero-trust infrastructure for all government agencies by 2024, drawing insights from the SolarWinds crisis. As a year has passed since then, it is anticipated that the recent hacking attack by the Chinese hacker group will further expedite the prioritization of security measures.
The U.S. cybersecurity market is currently witnessing active discussions regarding the implementation of “Zero Trust Architecture.” These developments in the United States have also generated considerable interest in Korea. In order to stay abreast of the evolving security paradigm of zero trust, numerous companies are intensifying their focus on research and development. They are actively reviewing and enhancing their solutions to align with the principles of zero-trust architecture.
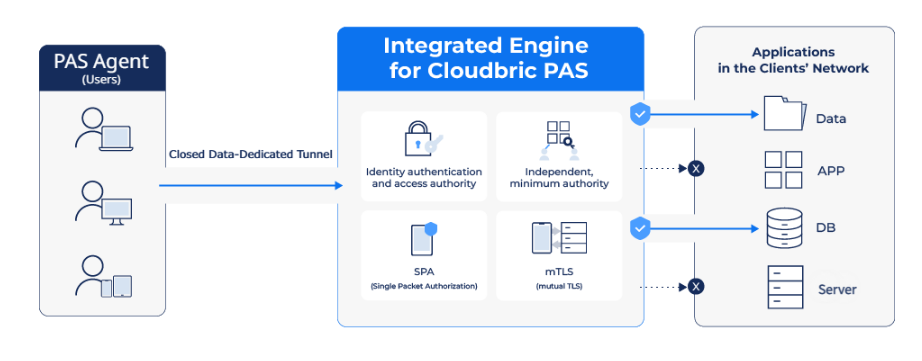
Cloudbric Private Access Solution (PAS) offered by the cloud security company Cloudbric is a robust zero-trust network access (ZTNA) solution that leverages Software Defined Perimeter (SDP) technology. By providing access control across various protocols, Cloudbric PAS ensures the protection of corporate or institutional networks against external threats by implementing a zero-trust network environment.
📌 Learn more about Cloudbric PAS
In cloud-based IT environments, the traditional concept of physical network boundaries is becoming more challenging. Consequently, more businesses and organizations are adopting Zero Trust Network Access (ZTNA) solutions to safeguard their on-premises systems against potential security threats.
Cloudbric PAS is an agent-based Zero Trust Network Access (ZTNA) solution that is designed to establish secure network environments. By implementing strict authentication and granular policies, Cloudbric PAS enables businesses to grant access to specific programs or resources exclusively to authenticated users, ensuring a robust security framework for protecting networks effectively. Explore Cloudbric PAS to empower your organization with enhanced network security measures.





