Can you really track a DDoS attack? Would you be able to find who’s behind the attack? Who’s DDoSing you?
The first “D” in the compound word “DDoS” is the big problem. Tracking a “Distributed” attack coming from thousands of infected machines turned into bots is no easy task. But using a detective’s most popular tools, like back-engineering, mitigation, and forensics, could give you the upper hand.
Remember: DDoS attacks only lead to destruction. Mitigate and control first, and only then trace the attack.

1. Understanding the New Breed of DDoS Attacks
Traditionally DDoS-ers didn’t gain anything other than power and control out of bringing down the service of a site with a DDoS attack. A DDoS is not as lucrative as other types of easier cyber crimes like phishing, spamming, ransomware, cryptojacking, etc.But now, the whole purpose of DDoSing has changed. Now DDoS attackers are using the effectiveness of a DDoS for other lucrative methods, like:
- Ransom. DDoS is being used as a threat for ransom in modern DDoS Extortion campaigns.
- Used as a smokescreen: DDoS can be used to distract IT personnel from a targeted and severe attack, like a data breach. DDoS-ers may only launch a DDoS to install backdoors (via Trojans or Malware) to gain complete control.
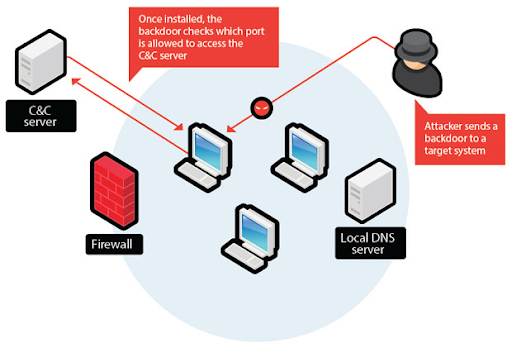 DDoSers install backdoors in compromised servers to later command and control.
DDoSers install backdoors in compromised servers to later command and control.
The new breed of DDoS is also becoming stealthier and harder to trace. DDoS attackers build and control botnets with techniques like onion routing, P2P, and obfuscation. They attempt to create larger smoke screens that conceal their identities and anonymize their cyberattacks.
2. To Uncover a DDoS Attack, Reverse-Engineer it!
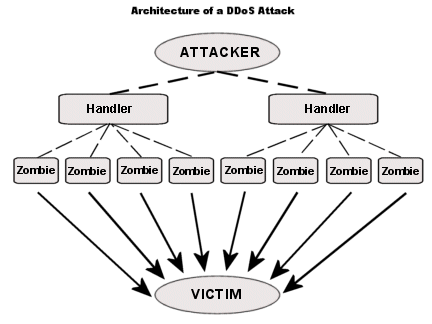
To know how to trace a DDoS attack and identify who is DDoS-ing you, let’s see who is involved in the attack’s architecture. We’ll deconstruct the attack and attempt to reveal its architecture, strategies, actors, or additional “criminal” knowledge. The anatomy of any DDoS is Attacker > Botnet > Victim.Who’s the Botnet? — Bots are global infected machines turned into “zombies” that follow instructions. A botnet is the network of bots. Without a botnet, the attack is just a DoS, which is weak, much easier to stop, and can be traced back. But adding a botnet into the mix steps up the attack’s efficiency and power, plus it hides the source. Although it is possible to identify the source IP of these bots — most of the time, it leads nowhere. These IPs are often traced back to malware-infected machines owned by clueless and innocent people.How DDoS-ers control Botnets? — Via the Client-server or P2P method.
a. Centralized Botnets: Client/Server.
The DDoSer has an entire army of bots at its disposal. The attacker may control bots using the server/client method. But the attacker stays outside of this equation; it just steps in to set instructions in the central handler (or handlers), which act like proxies. These bots (clients) connect to a handler’s resource like IRC or web domain (HTTP) to get the new instructions. The problem for DDoS-ers with this approach is that it creates a single-point-of-failure. If the command and control (handler) gets identified, a big portion (or whole) of the army can be traced and shut down.
b. Distributed Botnets: The P2P method.
Botnet malware developers identified the single-point-of-failure with the server-client method, so they decided to decentralize command. The Peer to Peer (P2P) communication method used in file sharing and torrents makes everybody a client and server— in other words, a bot and command and control server. With P2P, botnets are even more challenging to trace. P2P bots use digital signatures to prevent anybody within the P2P network from gaining control over the botnet. Only one with the private key can control the botnet. Examples of P2P botnets are Gameover ZeuS and ZeroAccess botnet.
3. When Botnets are Hired.
The DDoS scene changes, when botnets are hired. Back in 2016, the botnet Mirai, with close to 400,000 bots, took down the most popular sites on the Internet. A couple of months afterwards, the botnet was offered as a service. Now, a simple search on the dark web can lead you into hundreds of these types of DDoS booters and Botnets-as-a-Service criminal offerings.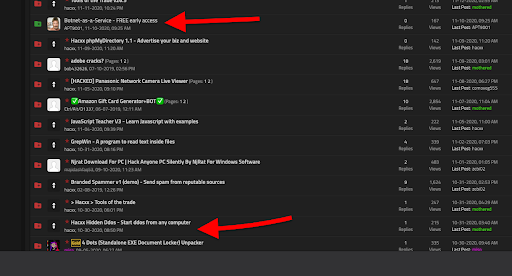 Advanced DDoS booters offer a front–end service (HTTP) to hire using untraceable cryptocurrency. The same frontend is used to send instructions to an entire army of bots. These services own their bots or often use banks (Bot services like Zeus and Vertix). Their back-end service is the one that controls the bots and initiates an attack. These back-end servers (handlers) are usually unregistered (hijacked IPs) or hacked servers. These criminals hijack IPs and change BGP prefixes to reroute traffic. So, it becomes near impossible to trace back these servers to a specific name or company.
Advanced DDoS booters offer a front–end service (HTTP) to hire using untraceable cryptocurrency. The same frontend is used to send instructions to an entire army of bots. These services own their bots or often use banks (Bot services like Zeus and Vertix). Their back-end service is the one that controls the bots and initiates an attack. These back-end servers (handlers) are usually unregistered (hijacked IPs) or hacked servers. These criminals hijack IPs and change BGP prefixes to reroute traffic. So, it becomes near impossible to trace back these servers to a specific name or company.
How to Trace a DDoS Attack?
Below are the necessary steps to act upon a DDoS attack.
a. First, get everything back on track and then hunt them down!
During the first few minutes of a DDoS attack, nobody wants to find the criminal; they only want to get back on their feet. Their priority is (and should be) to mitigate the attack. If the traffic looks suspicious, move upstream to your local ISP and get them to stop that particular traffic — before it goes downstream to your server. For websites and web applications, ISPs wouldn’t be able to do much. A most effective way to prevent DDoS or to lessen its intensity is to redirect traffic to a CDN (Content Delivery Network) and use a web application protection service. An AI deep learning WAF like SWAP is capable of taking all traffic in and recognizing web attack patterns. With a WAF behind a CDN, large-scale suspicious DDoS traffic loses power and is entirely filtered by the intelligent WAF.
 b. Tracing Bots and Controllers.
b. Tracing Bots and Controllers.
“I will strike the shepherd, and the sheep of the flock will be scattered” — A passage from the Bible and also quoted by Robert Greene, from the 48 Laws of Power. Tracing back a botnet can take a tremendous amount of energy, which is out of the question when the service is down. The best approach is to find the source of trouble coming from a single and powerful individual – The DDoS-er. But how do we do that? If the DDoS-er is hidden behind its army of bots? We could always “IP traceback” particular packets (or sequences of packets) coming in. We could:
- Trace bot’s IPs and operating system
- Track their geolocation (it could be anywhere in the world)
- Identity their backbone network providers
- Contact them and make them stop
Tracing one or two bots with IP traceback methods is feasible; tracking an entire botnet with 30,000 infected bots is not. As mentioned before, DDoS-ers use one or more controllers or proxies to hide behind the botnet. Attackers only use their machines to send encrypted (or obfuscated) messages to these controllers. Going after these controllers can be far more challenging but also far more efficient. Breaking down encrypted or obfuscated messages to trace these controllers is beyond the scope of this article.
c. Forensics will help.
Forensics uses trace evidence to attempt to reconstruct an attack from beginning to end. Going as deep as possible into the affected network or server will give forensics valuable evidence. But determining the source of DDoS is not an easy thing to do. Most DDoS-ers are masters at hiding and creating smokescreens to protect their true identity, but they are no Gods— they do make mistakes. Try gathering the following intelligence:
- Understanding their motivation can help build a criminal profile: Is the attacker after power, control, or money?
- Was the attacker only trying to open a backdoor or steal data?
- Did they use a DDoS Booter or a Botnet as a Service? Maybe someone internally made a DNS request to one of these services?
- DDoS-ers need resources (and lots of them); where do you think they are getting it from?
- Can you follow a payment trail?
- Can you tell whether they are using Low Orbit Ion Cannon (LOIC), hping, or similar stress testing tools?
Final Words.
Preventing a DDoS attack is sometimes the best way to fight against these nasty attacks. But doing it without any DDoS mitigation strategy can be challenging. You might be able to stop an attack (temporarily) if you play by their rules, like paying a ransom. But if they see you as an easy to comply target, they are likely to continue throwing DDoS attacks. Some attacks won’t stop unless you find the source and counterattack. Stay ahead and start your DDoS protection strategy today. Try SWAP’s AI-based web application protection and claim your free trial!